24 Javascript Cookie Secure Flag
Cookie XSRF-TOKEN created without the secure flag - Laravel 5.8. I am using Laravel 5.8 . I use Nikto to scan my site, I saw these issues. Cookie XSRF-TOKEN created without the secure flag. Cookie XSRF-TOKEN created without the httponly flag. Cookie laravel_session created without the secure flag. The cookies themselves are set by the application, and the cookie flags are part of that. Cookies can have several flags: "secure", "httponly", "samesite". Only the application knows which cookies should have which flags. If your proxy inserts the httponly flag and the application wants to access the cookie with Javascript, this will no longer ...
 Overwriting Httponly Cookie By Javascript Stack Overflow
Overwriting Httponly Cookie By Javascript Stack Overflow
Keeping JavaScript's Hands Away from the Cookie Jar. ... secure cookies with their own. Cookie Prefixes •Problem: -Server only sees cookie name and value in HTTP request, no information about its attributes -Impossible for server to know if a cookie it receives was set securely
Javascript cookie secure flag. The HttpOnly cookie flag is often added to cookies that may contain sensitive information about the user. Essentially, this type of flag tells the server to not reveal cookie information contained in embedded scripts. HttpOnly also tells the server that the information contained in the flagged cookies should not be transferred beyond the server. An HTTP cookie (web cookie, browser cookie) is a small piece of data that a server sends to the user's web browser. The browser may store it and send it back with later requests to the same server. Typically, it is used to tell if two requests came from the same browser — keeping a user logged-in, for example. It remembers stateful information for the stateless HTTP protocol. To prevent these hacks, we should be using HttpOnly flags in cookies. HTTPOnly attribute Forbids JavaScript from accessing the cookie . Note that a cookie that has been created with HttpOnly will ...
Securing Cookies with HttpOnly and secure Flags Any program that runs can be disassembled, but that doesn't mean it's going to be easy. In this skills course you'll… with the HttpOnly flag we tell the browser not to share the cookie with the client (eg. allowing JavaScript access to the cookie), limiting the blast radius of an XSS attack tagging the cookie as SameSite=Lax|Strict will prevent the browser from sending it in cross-origin requests, rendering any kind of CSRF attack ineffective In this lesson, we'll learn how to set the httpOnly flag on our session id cookie to ensure it is inaccessible from javascript, thereby defeating theft of the session id from the XSS attack we crafted in the previous lesson. However, we'll still leave ourselves open to other dangers from XSS, ...
Jan 31, 2018 - The secure attribute is always activated for secured cookies, so it is transmitted with encrypted connections, without any hassles and security issues. The httpOnly flag does not give cookie access to JavaScript or any non-HTTP methods. This is situated in the secure cookie header. The HTTPOnly flag and "secure flag" (which forces the cookie to be sent over https) should always be set. If you are an attacker, then you want to hijack a session. But there is an easy way to hijack a session despite the HTTPOnly flag. You can still ride on the session without knowing the session id. If set as the value of cookieFlags, it would create the Google Analytics cookie with an expiration of two hours (7200 seconds), set it on the simoahava domain and on the root path, and make sure it's only sent with HTTPS requests andmake it available as a third-party cookie.
Description: Cookie without HttpOnly flag set If the HttpOnly attribute is set on a cookie, then the cookie's value cannot be read or set by client-side JavaScript. The session cookies are deleted when the browser shuts down and if the cookies are permanent, they will expire at the time defined by Expires or Max-Age. The risk of client-side scripts accessing the protected cookie can be mitigated by including an additional "HttpOnly" flag in the Set-Cookie HTTP response header. Jul 13, 2017 - Support Forum · Members · Segment · To log in, please enable your browser cookies and then click retry · How to enable browser cookies · Community login · © 2021 Segment Privacy Policy Terms of Service · Powered by Forumbee
Cookies are small strings of data that are stored directly in the browser. They are a part of the HTTP protocol, defined by the RFC 6265 specification.. Cookies are usually set by a web-server using the response Set-Cookie HTTP-header. Then, the browser automatically adds them to (almost) every request to the same domain using the Cookie HTTP-header.. One of the most widespread use cases is ... php_value session.cookie_httponly 1 php_value session.cookie_secure 1 Note that session cookies will only be sent with https requests after that. This might come as a surprise if you lose a session in non-secured http page (but like pointed out in the comments, is really the point of the configuration in the first place…). Nov 20, 2017 - Find answers to Setting cookie secure flag using javascript? from the expert community at Experts Exchange
1 week ago - It also signals that the domain attribute must not be present, which prevents the cookie from being sent to other domains. For Chrome the path attribute must always be the origin. Note: The dash is considered part of the prefix. Note: These flags are only settable with the secure attribute. 24/8/2020 · The Secure flag is used to declare that the cookie may only be transmitted using a secure connection (SSL/HTTPS). If this cookie is set, the browser will never send the cookie if the connection is HTTP. This flag prevents cookie theft via man-in-the-middle attacks. Note that this flag can only be set during an HTTPS connection. If it is set during an HTTP connection, the browser ignores it. Example: … According to Michael Howard, Senior Security Program Manager in the Secure Windows Initiative group at Microsoft, the majority of XSS attacks target theft of session cookies. A server could help mitigate this issue by setting the HttpOnly flag on a cookie it creates, indicating the cookie should ...
May 23, 2016 - In the specification, regarding removal of cookies (.remove), the following is specified: IMPORTANT! when deleting a cookie, you must pass the exact same path, domain and secure attributes that wer... Cookies are not sent on normal cross-site subrequests (for example to load images or frames into a third party site), but are sent when a user is navigating to the origin site (i.e., when following a link).. This is the default cookie value if SameSite has not been explicitly specified in recent browser versions (see the "SameSite: Defaults to Lax" feature in the Browser Compatibility). Dec 15, 2016 - In an XSS breach case, an attacker could inject some Javascript, and potentially access to the cookies that, as a reminder, often contain sensitive information. First of all, it is obviously better to prevent the XSS breaches. Then you can avoid those weaknesses to be exploited by defining a Content Security Policy. The "secure" flag ...
In this situation, the HttpOnly flag should be set. Some cookies do need to interact with JavaScript based on their function, setting the HttpOnly flag, in this case, would render the cookie useless to the application. In order to demonstrate how the HttpOnly flag works two files were created. 22/3/2019 · When a secure flag is used, then the cookie will only be sent over HTTPS, which is HTTP over SSL/TLS. When this is the case, the attacker eavesdropping on the communication channel from the browser to the server will not be able to read the cookie (HTTPS provides authentication, data integrity and confidentiality). Jun 05, 2019 - Secure cookies can be read with JavaScript, but HTTPOnly ones cannot. This means that if both flags are set, they cannot be read - the flags are terribly named. Secure is to do with transmission - they should only be sent over HTTPS connections - but it is possible to set secure cookies from JS, ...
The first flag we need to set up is HttpOnly flag. By default, when there's no restriction in place, cookies can be transferred not only by HTTP, but any JavaScript files loaded on a page can also access the cookies. This ability can be dangerous because it makes the page vulnerable to cross-site scripting (XSS) attack. HttpOnly - This option on a cookie causes the web browsers to return the cookie using the http (or https) protocol only; the non-http methods such as JavaScript document.cookie references cannot access the Cookie. This option assists in preventing Cookie theft due to cross-site scripting. The secure attribute is an option that can be set by the application server when sending a new cookie to the user within an HTTP Response. The purpose of the secure attribute is to prevent cookies from being observed by unauthorized parties due to the transmission of the cookie in clear text.
24/5/2018 · The two cookie properties (or flags) which we saw earlier (HttpOnly and Secure) are the reason for this. HttpOnly Flag HttpOnly cookies are inaccessible to JavaScript's Document.cookie API; they are only sent to the server. For example, cookies that persist server-side sessions don't need to be available to JavaScript, and the HttpOnly flag ... The HttpOnly cookie is supported by most modern browsers. On a supported browser, an HttpOnly session cookie will be used only when transmitting HTTP (or HTTPS) requests, thus restricting access from other, non-HTTP APIs (such as JavaScript). In other words, HttpOnly cookies are made to be used only on the server side. I wrote an example in PHP: Mar 14, 2019 - Learn how to manipulate cookies using JavaScript with this tutorial. Re-usable functions for easy cookie access are provided, for use in your own scripts.
2 weeks ago - The Set-Cookie HTTP response header is used to send a cookie from the server to the user agent, so the user agent can send it back to the server later. To send multiple cookies, multiple Set-Cookie headers should be sent in the same response. 28/12/2020 · The httponly flag makes sure the cookie can not read from javascript, protecting the cookie from being stolen through use of a large variety of javascript-based attacks (such as cross-site scripting). Remediation. In order to remediate this issue, make sure the secure flag is set on all cookies and the httponly flag is set on all cookies which ... 14/5/2016 · Cookie Flags. Cookie flags are prefixes. At the moment, they are described in the RFC draft as a update to the RFC6265. These flags are used with the 'secure' attribute. __Secure- The dash is a part of the prefix. This flag tells the browser, the cookie should only be included in 'https'. __Host- A cookie with this flag
See Date.toUTCString() for help formatting this value.;secure Cookie to only be transmitted over secure protocol as https. Before Chrome 52, this flag could appear with cookies from http domains.;samesite SameSite prevents the browser from sending this cookie along with cross-site requests. Possible values are lax, strict or none. ... 12/3/2019 · The “HttpOnly” flag blocks the access of the related cookie from the client-side (it can’t be used from Javascript code): if an attacker was to succeed in injecting some javascript despite all your precautions, he won’t be able to access the cookies anyway. That will significantly limit the attack range. The Secure flag on the JSESSIONID is not enabled by default. To add the Secure flag to the JSESSIONID, make sure the option "Restrict cookies to HTTPS sessions" is selected. In the administrative console: click on Application servers > servername > Session management > Enable cookies WebSphere Application Server v7.0: HTTPOnly flag
A simple, lightweight JavaScript API for handling browser cookies - GitHub - js-cookie/js-cookie: A simple, lightweight JavaScript API for handling browser cookies
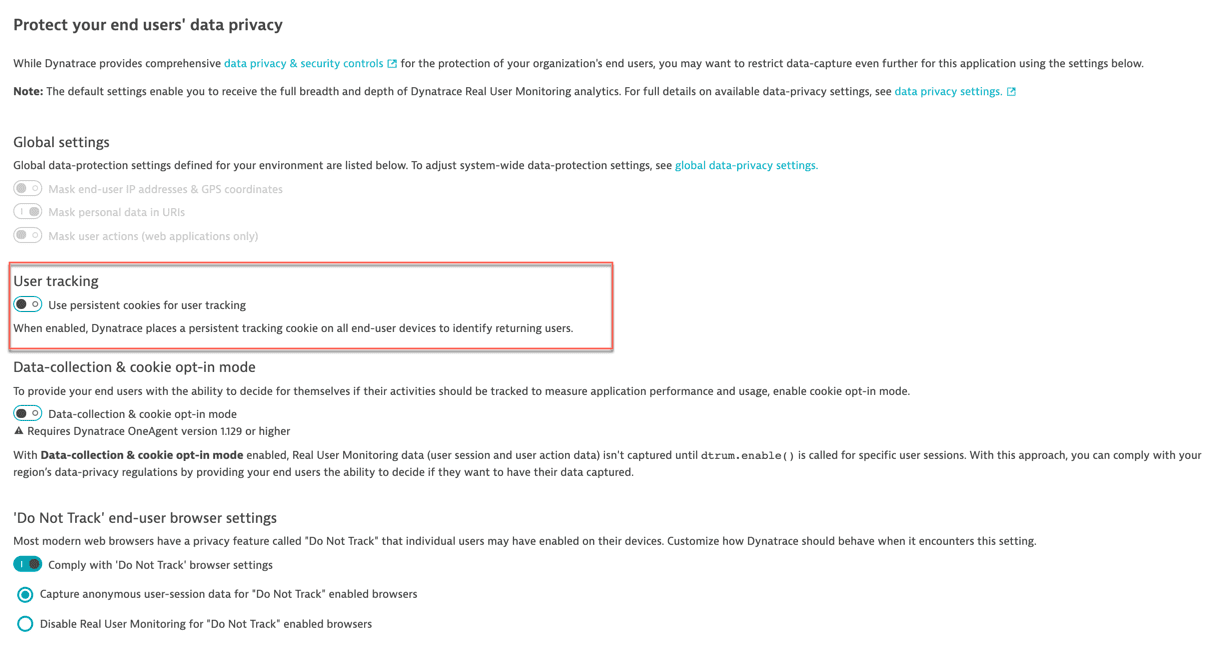
 Cookies Dynatrace Documentation
Cookies Dynatrace Documentation
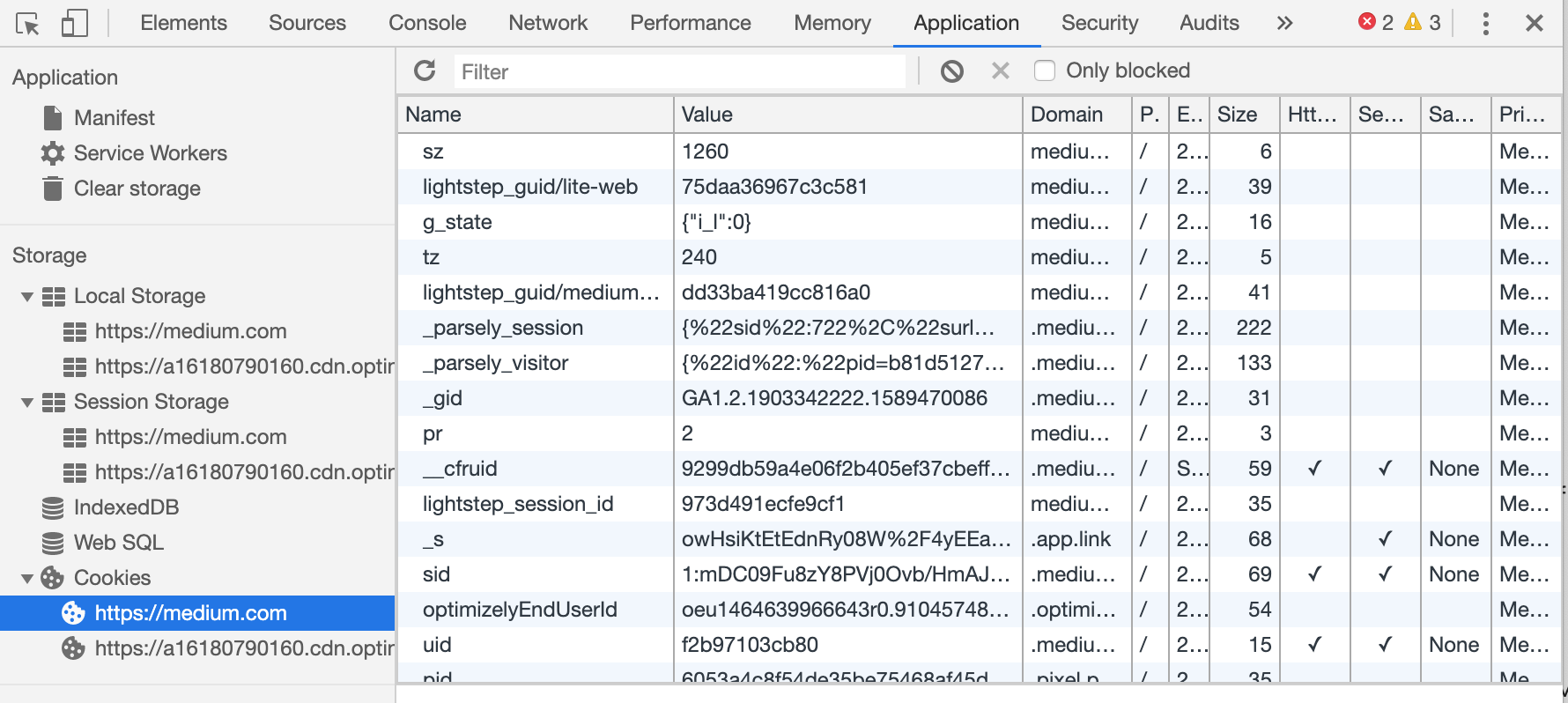 Local Storage Vs Session Storage Vs Cookie By Krishankant
Local Storage Vs Session Storage Vs Cookie By Krishankant
 Setting Secure Cookies Drupal Answers
Setting Secure Cookies Drupal Answers
 Localstorage Vs Cookies All You Need To Know About Storing
Localstorage Vs Cookies All You Need To Know About Storing
Tips For Testing And Debugging Samesite By Default And
 Chrome Developer Tools Gt Resources Gt Cookies Gt Http Column
Chrome Developer Tools Gt Resources Gt Cookies Gt Http Column
 Basic Shttponly Cookie Flag Set Cookie
Basic Shttponly Cookie Flag Set Cookie
 Why Are Browsers Not Displaying Httponly Flag Stack Overflow
Why Are Browsers Not Displaying Httponly Flag Stack Overflow
Cookies Com Auth0 Auth Have No Secure Flag Issue 1050
 How To Set Httponly And Secure Flag To Cookie In Java For
How To Set Httponly And Secure Flag To Cookie In Java For
Web Application Cookies Lack Httponly Flag Howtoforge
 Another Set Cookie Attribute For Secure Flag Stack Overflow
Another Set Cookie Attribute For Secure Flag Stack Overflow
 Httponly Set Cookie Http Response Header Owasp
Httponly Set Cookie Http Response Header Owasp
Xss Resolved Reflected Cross Site Scripting Cwe 79 Capec
Tips For Testing And Debugging Samesite By Default And
 Cookie Based Sample Login App Maven Project
Cookie Based Sample Login App Maven Project
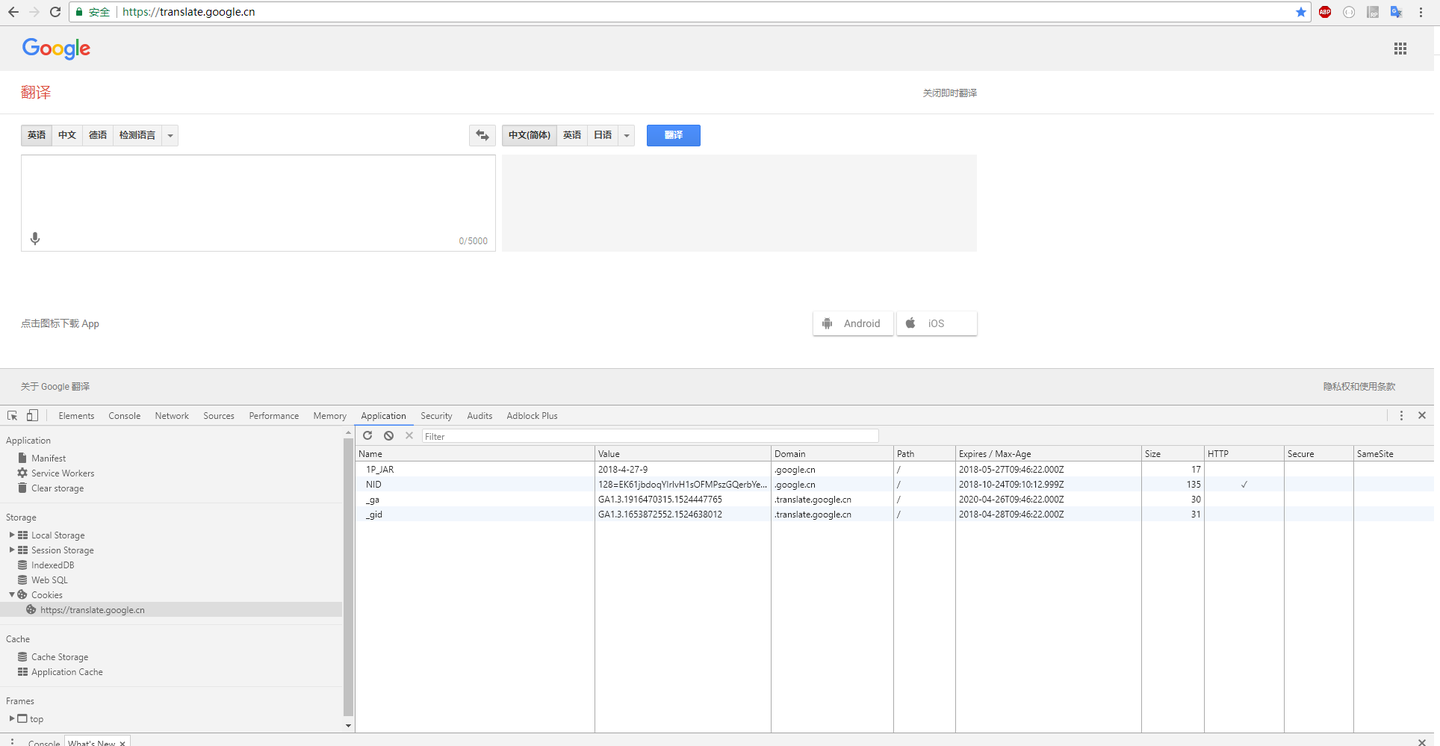 浅谈js 操作cookie 以及httponly 的限制 知乎
浅谈js 操作cookie 以及httponly 的限制 知乎
 Xss Gaining Access To Httponly Cookie In 2012
Xss Gaining Access To Httponly Cookie In 2012
Unable To Set Secure Flag For Cookies Using Cookies
 Missing Httponly Cookie Attribute In Laravel 7 Information
Missing Httponly Cookie Attribute In Laravel 7 Information
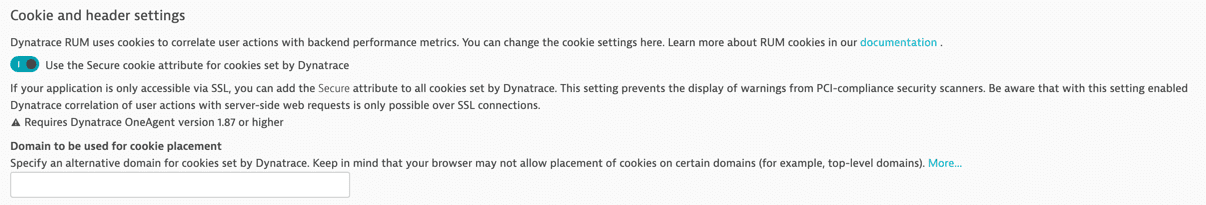 Cookies Dynatrace Documentation
Cookies Dynatrace Documentation
 Solved How To Set Up Httponly And Secure Flag For Session
Solved How To Set Up Httponly And Secure Flag For Session
 Why Are Httponly Cookies Not Being Set Correctly In Ie9
Why Are Httponly Cookies Not Being Set Correctly In Ie9
0 Response to "24 Javascript Cookie Secure Flag"
Post a Comment