26 Eval In Javascript Security Risk
The security risk # Inserting "evil" inline script tags into a page is a common attack. If you ever allow the user-produced content to be linked into the DOM (to control its appearance for example), then your website is vulnerable to this attack. If you allow the user to enter this text eval()executes a string of characters as code. You use eval()precisely because the string contents are not known in advance, or even generated server-side; basically, you need eval()because the JavaScript itself will generate the string from data which is available only dynamically, in the client.
 Library Causes Csp Issue No Error Issue 1311
Library Causes Csp Issue No Error Issue 1311
Dec 12, 2017 - Also, avoid the eval function therefore significantly decreasing the risk of such vulnerabilities. The eval function is used specifically for the speed benefits it offers but it can compile and execute any JS code. This gives rise to significant risk to the security of application.

Eval in javascript security risk. Jul 28, 2021 - Never use eval()! ... Warning: Executing JavaScript from a string is an enormous security risk. It is far too easy for a bad actor to run arbitrary code when you use eval(). See Never use eval()!, below. Feb 01, 2018 - In Javascript, eval() is one of the most interesting yet most dangerous functions in the language. Eval() takes a string and attempts to run it as Javascript code. While the above example is safe and… You should avoid eval () and new Function (). Dynamically evaluating code is slow and a potential security risk. It also prevents most tools (such as IDE's) that use static analysis from considering the code. Often, there are better alternatives.
May 04, 2021 - Learn some best practices for keeping your Node.js and JavaScript projects safe from code injection attacks. So let's evaluate the risk of 'unsafe-eval' in a Content-Security-Policy. What it effectively means is that your policy won't be able to protect you against an XSS (Cross-Site-Scripting) vulnerability involving JavaScripts eval () function. Eval is understood to be the step of converting a quoted string into a callable function and its arguments, whereas apply is the actual call of the function with a given set of arguments. The distinction is particularly noticeable in functional languages, and languages based on lambda calculus, such as LISP and Scheme.
eval() is a very powerful method and it is always considered as evil due to security and performance issues. Eval code execution is very slow, and it is very difficult to debug. So, eval() method in JavaScript should be used very carefully. A remote user can supply a specially crafted URL to pass arbitrary code to an eval () statement, which results in code execution. Note 1: This attack will execute the code with the same permission like the target web service, including operation system commands. Oct 25, 2014 - Passing user input to eval() is a security risk, but also each invocation of eval() creates a new instance of the JavaScript interpreter. This can be a resource hog.
While the cyber security guidelines can assist with risk identification and risk treatment activities, organisations will still need to undertake their own risk analysis and risk evaluation activities due to the unique nature of each system, its operating environment and the organisation's risk tolerances. SUBJECT: INFORMATION SECURITY RISK EVALUATION OF REGION I - KING OF PRUSSIA, PA (OIG-13-A-06) Attached is the Office of the Inspector General's (OIG) evaluation report titled, Information Security Risk Evaluation of Region I - King of Prussia, PA. The report presents the results of the subject evaluation. The agency agreed with the The following JavaScript security best practices can reduce this risk. Avoid eval (): Don't utilize this command in code, since it simply executes passed argument if it is a JavaScript expression. This means if the hacker succeeds in manipulating input value, he or she will be able to run any script she wants.
Sep 30, 2012 - What about security? If its your software that’s supplying eval with its argument then there’s very little to fear on this front. Sure, it would be unwise to eval the value of an input box, but running eval over a response generated by your own server code should present no special risk. The information security risk criteria should be established considering the context of the organization and requirements of interested parties and will be defined in accordance with top management's risk preferences and risk perceptions on one hand and will leave a feasible and appropriate risk management process on the opposite hand. The ... Jun 25, 2013 - However, if your use of eval() ... are no security risks. The most common attack vector cited these days is in eval()ing code that is returned from the server. This pattern famously began with the introduction of JSON, which rose in popularity specifically because it could quickly be converted into a JavaScript by using eval(). ...
JavaScript Security Risks. Abstract: This document addresses the issues that JavaScript introduces into a document format. It shows how basic JavaScript can be manipulated and obfuscated to evade signature detection, by using publically available and known methods. Code that introduces both a data hiding and data attack risk can be difficult to ... JavaScript eval () function The eval () function in JavaScript is used to evaluate the expression. It is JavaScirpt's global function, which evaluates the specified string as JavaScript code and executes it. The parameter of the eval () function is a string. Allows secure eval execution of JavaScript code in a browser context. - Prendus/secure-eval
Jan 01, 2021 - A comparison of working and performance of eval and safeEval and how they behave with examples . Oct 09, 2012 - JavaScript vulnerabilities are on the rise in India with the entry of HTML5 and faster JavaScript engines. Here are some key problem areas along with antidotes. Several native JavaScript functions or properties like.eval () and.innerHTML as well as several jQuery functions like.html () and.append () are considered as "unsafe", but why?
Node.js is the latest security risk for developers ... "Node is still JavaScript, so eval and all the terrible things on the client side still exist on the server side," Stuart said. Dec 10, 2020 - The eval() function essentially takes a string of code and attempts to run it as JavaScript. This function exists in several programming languages and has a few legitimate uses, but developers should be careful with it. That’s because using eval() in JavaScript can pose a major security risk. Aug 23, 2016 - Is there such thing as "secure javascript code" in general? ... Nope. Everything's as secure as everything else, which basically is not secure at all with all the debugging tools around. Personally (and I'll probably get kicked in the teeth for saying this, but...) I'm not that scared of eval (or ...
The 'strict-dynamic' source expression specifies that the trust explicitly given to a script present in the markup, by accompanying it with a nonce or a hash, shall be propagated to all the scripts loaded by that root script. At the same time, any allowlist or source expressions such as 'self' or 'unsafe-inline' will be ignored. For example, a policy such as script-src 'strict-dynamic' 'nonce ... The FDIC's Physical Security Risk Management Process . April 2019 EVAL-19-001 . Evaluation Report . Program Audits and Evaluations containing sensitive . REDACTED VERSION PUBLICLY AVAILABLE . Portions of this report information have been redacted and are marked accordingly. Now, the times I have used JavaScript to enrich user experience the most harming code I was able to have run in the browser was basically just a loop with spamming alert messages, this is more of an annoyance than a security risk though and can easily be disabled by the user on up-to-date browsers.
Eval () in JavaScript Security Risks The eval () function essentially takes a string of code and attempts to run it as JavaScript. This function exists in several programming languages and has a few legitimate uses, but developers should be careful with it. That's because using eval () in JavaScript can pose a major security risk. Security Controls Evaluation, Testing, and Assessment Handbook provides a current and well-developed approach to evaluation and testing of security controls to prove they are functioning correctly in today's IT systems. This handbook shows you how to evaluate, examine, and test installed security controls in the world of threats and potential breach actions surrounding all industries and systems. The eval() is an in-built JS function that evaluates arguments that are expressions and executes one or more statements given to it as arguments.. Reason eval() consider evil: There are several problems possessed by the use of eval() and out of all performance and code injection are considered the most problematic. Performance- since script compiler cannot pre-compile eval(), it runs the ...
Jul 25, 2013 - However, if your use of eval() ... are no security risks. The most common attack vector cited these days is in eval()ing code that is returned from the server. This pattern famously began with the introduction of JSON, which rose in popularity specifically because it could quickly be converted into a JavaScript by using eval(). ... sion of what elements make up a comprehensive information security risk assessment that examines both organizational and technology issues. Over time, as we develop and pilot an evaluation method consistent with the OCTAVE framework, we anticipate that the details described in this report will be modified. The eval () function has been around for a long time in JavaScript! You likely don't see it often anymore because it's widely agreed that it's harmful to use. Let's take a brief look at it, and some of the dangers associated with using it. The keyword eval is an abbreviation for "evaluate."
Also, I need to mention that eval() uses the scope in which it is called. Risks The main reason you should avoid using it is a security. Evaluating JavaScript code from a string is hazardous. A string may consist of malicious code that will be run on the user's machine, and the scope, where eval() was called will be exposed for possible attacks. Cloud Computing Standardize Root Mean Square Residual Security Risk Adoption Decision Formative Indicator These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves. Dec 14, 2018 - Allows secure eval execution of JavaScript code in a browser context.
Jul 15, 2019 - Website with the collection of all the cheat sheets of the project. The best method to prevent client-side JSON injections is never to use the eval function to evaluate JSON data. If you use the eval function and the untrusted data contains JavaScript code, that code will be executed. To avoid this, use JSON.parse. You can also enforce Content Security Policy, which by default prevents the use of eval. The danger of eval()is that an attacker may be able to manipulate data that is eventually run through eval()in other ways. If the eval()'d string comes from an HTTP connection, the attacker may perform a MITM attack and modify the string.
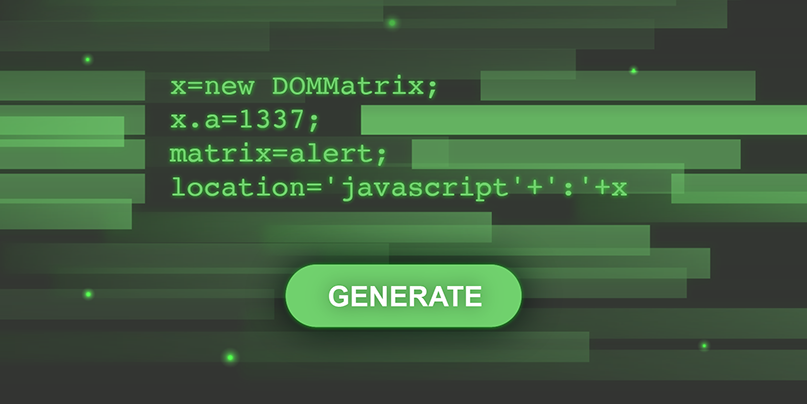 Javascript Without Parentheses Using Dommatrix Portswigger
Javascript Without Parentheses Using Dommatrix Portswigger
Content Security Policy Csp Explained Including Common
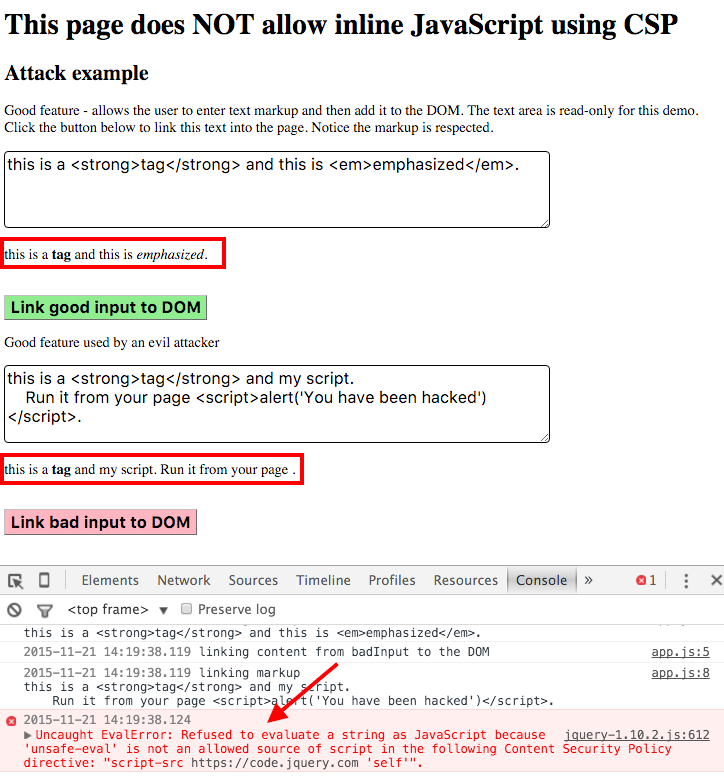 Disable Inline Javascript For Security Better World By
Disable Inline Javascript For Security Better World By
 Risk Analysis Framework Documentation Splunk Developer
Risk Analysis Framework Documentation Splunk Developer
 Understanding The Most Common Javascript Vulnerabilities
Understanding The Most Common Javascript Vulnerabilities
 Electron Js Not Displaying Data From Mysql Stack Overflow
Electron Js Not Displaying Data From Mysql Stack Overflow
 Safer Eval Library Branded Harmful With No Patch Planned
Safer Eval Library Branded Harmful With No Patch Planned
 Analyzing Malicious Javascript Infosec Resources
Analyzing Malicious Javascript Infosec Resources
 What Are Json Injections Acunetix
What Are Json Injections Acunetix
 3 Security Pitfalls Every React Developer Should Know
3 Security Pitfalls Every React Developer Should Know
 Identifying Client Side Javascript Security Vulnerabilities
Identifying Client Side Javascript Security Vulnerabilities
Github Escopecz Js Expression Eval Mathematical Expression
 Eval Is Evil Why We Should Not Use Eval In Javascript Dev
Eval Is Evil Why We Should Not Use Eval In Javascript Dev
 Auditing Csp Headers With Burp And Zap Gosecure
Auditing Csp Headers With Burp And Zap Gosecure
 The Evil Javascript Eval Dev Community
The Evil Javascript Eval Dev Community
 Developing Secure Node Js Applications A Broad Guide By
Developing Secure Node Js Applications A Broad Guide By
 Javascript Security An In Depth Guide To Protect Javascript
Javascript Security An In Depth Guide To Protect Javascript
 Identifying Client Side Javascript Security Vulnerabilities
Identifying Client Side Javascript Security Vulnerabilities
 Shape Engineering Shape Security Blog
Shape Engineering Shape Security Blog
 Rollup Use Of Eval Is Strongly Discouraged As It Posses
Rollup Use Of Eval Is Strongly Discouraged As It Posses
 The Game Performance Is Terrible When There Are A Lot Of
The Game Performance Is Terrible When There Are A Lot Of
Angular Js Security Fundamentals Cyber Security Blogs
 Formal Methods For Web Security Sciencedirect
Formal Methods For Web Security Sciencedirect
 3 Security Pitfalls Every React Developer Should Know
3 Security Pitfalls Every React Developer Should Know
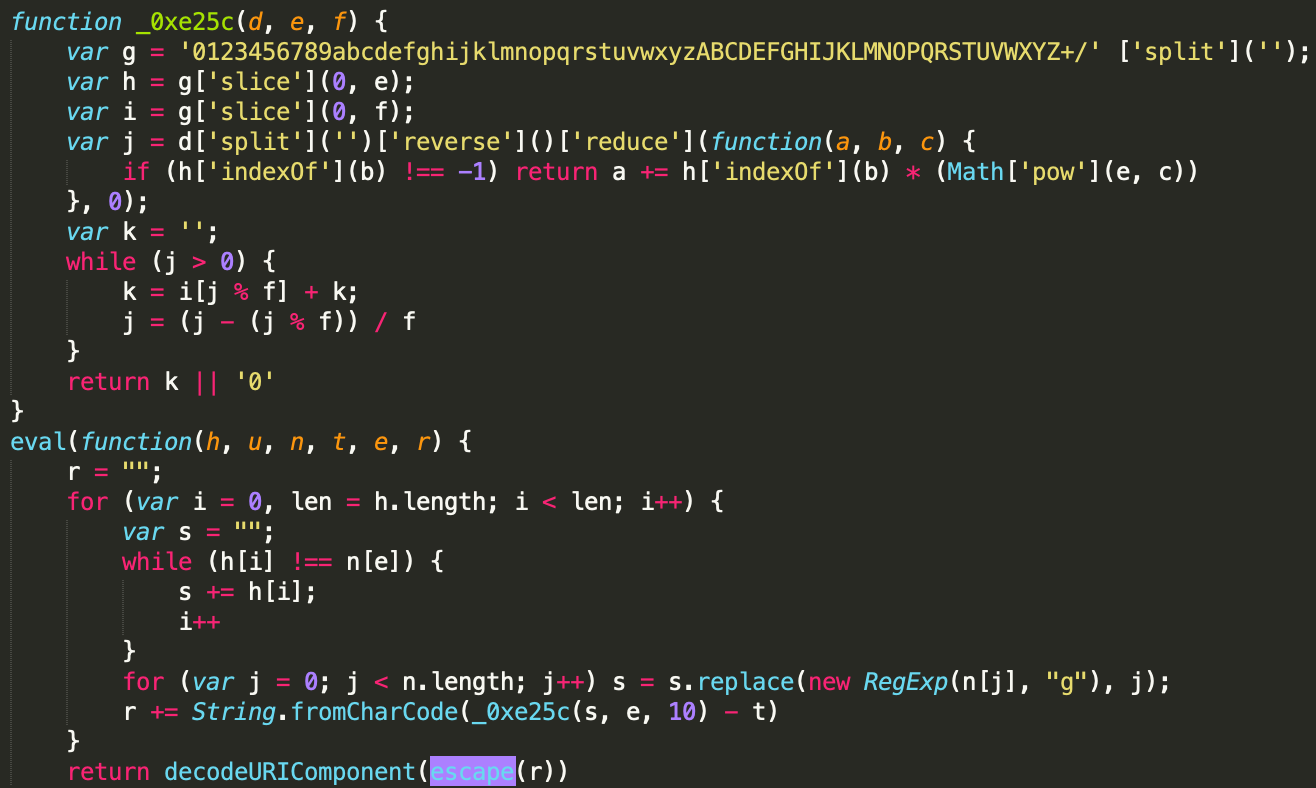 Javascript Sniffers New Tricks Analysis Of The E1rb Js
Javascript Sniffers New Tricks Analysis Of The E1rb Js
0 Response to "26 Eval In Javascript Security Risk"
Post a Comment