32 Javascript Alert Document Cookie Level10 Authorized Yes
javascript:void(document.cookie="level10_authorized=yes");alert(document.cookie);THAT IS THE CODE IF YOU DIDN'T GET IT BEFORE..... The window object represents an open window in a browser. If a document contain frames (<iframe> tags), the browser creates one window object for the HTML document, and one additional window object for each frame. Note: There is no public standard that applies to the Window object, but all major browsers support it.
 Hackthissite Basic Web Challenges 1 11 By Sampath
Hackthissite Basic Web Challenges 1 11 By Sampath
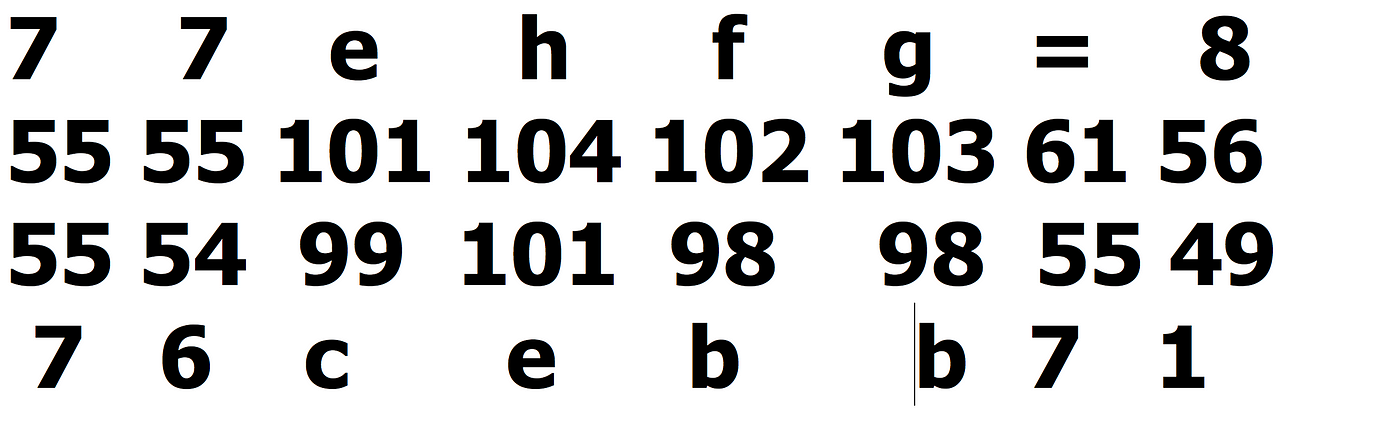
Using JavaScript a user can modify the current cookie settings. This can be performed with some basic JavaScript commands. To view the current contents of your current cookies, use the following JavaScript command. Put this in your browser's URL bar. javascript:alert(document.cookie); Contents:
Javascript alert document cookie level10 authorized yes. JavaScript function basics A JavaScript (Node.js) function is an exported function that executes when triggered ( triggers are configured in function.json ). The first argument passed to every function is a context object, which is used for receiving and sending binding data, logging, and communicating with the runtime. Three storage XSS were found in wtcms POC: javascript:alert(document.cookie) 1.Click on the background article management and fill in the XSS code at the source of the article Find the published article in the front desk and click on the... options Yes Object Determines whether the login and consent screens appear in a popup window, or on a separate browser page. Parameters described below. next No Function or String A URI to redirect the browser response, or a JavaScript function to call with the authorization response.
11/11/2011 · javascript:alert (document.cookie) Does not work in firefox 7 Ubuntu 11.10. I am trying to get the DSID of a web page by typing "javascript:alert (document.cookie)" in the url bar. I am supposed to get a window with the desired output which works fine in chromium. It does nothing in firefox 7 though. Cookies are not sent on normal cross-site subrequests (for example to load images or frames into a third party site), but are sent when a user is navigating to the origin site (i.e., when following a link).. This is the default cookie value if SameSite has not been explicitly specified in recent browser versions (see the "SameSite: Defaults to Lax" feature in the Browser Compatibility). If yes, then Close the alert (it was a false positive). Is the ATA Gateway involved in this alert a virtual machine? If yes, did it recently resume from a saved state? If yes, then Close this alert. If the answer to the above questions is no, assume this is malicious. Remediation
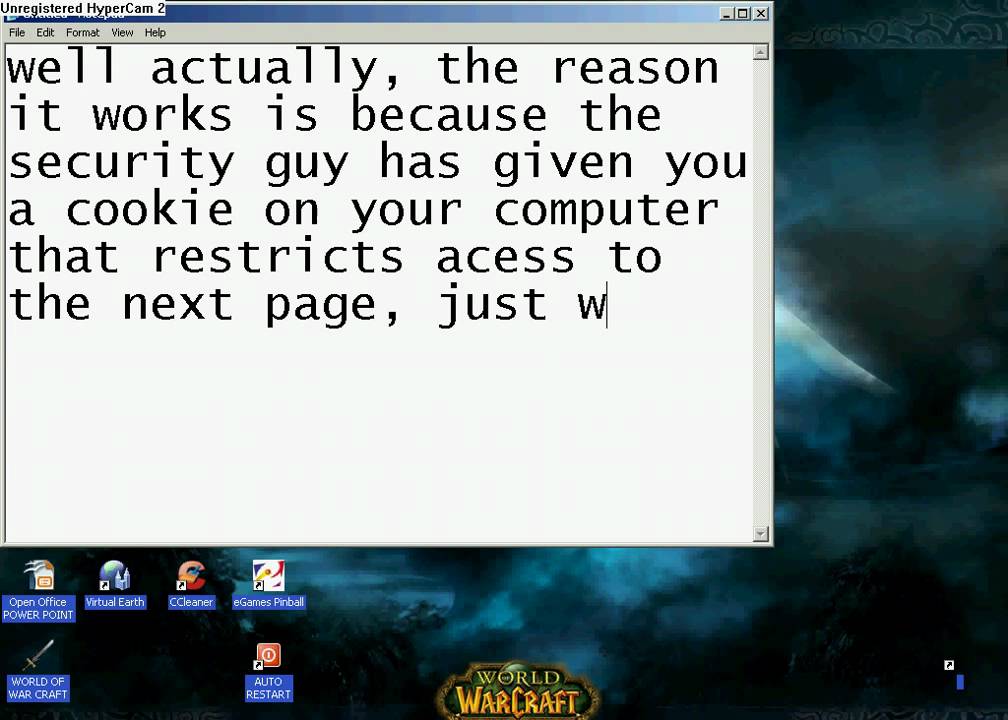
First off, check to see if the site you are visiting has set any cookies by using this script: javascript:alert(document.cookie); This will pop up any information stored in the sites cookies. To edit any information, we make use of the void(); command. javascript:void(document.cookie="Field = myValue"); menubar (yes/no) - shows or hides the browser menu on the new window. toolbar (yes/no) - shows or hides the browser navigation bar (back, forward, reload etc) on the new window. location (yes/no) - shows or hides the URL field in the new window. FF and IE don't allow to hide it by default. status (yes/no) - shows or hides the status ... Basic Mission 10 This mission is about cookies. To view your cookies, you can use JavaScript injection or a couple different Firefox plugins. Using JavaScript injection: Go to Basic 10, then put the following into your address bar and hit enter: [crayon-61291959b0ab2889712661/] This is your cookie. JavaScript makes it very easy to edit - just...
alert(document.cookie) either in the URL bar or in the Web Console section(if you're using Firefox.) For more information about JS injection you can refer to my Basic Mission 5 tutorial here. In the contents of the cookie there is something like "level10_authorized=no". You need to change that to "level10_authorized". javascript:void(document.cookie="Authorized=yes"); Would either make the field "authorized" or edit it to say "yes"... now wheter or not this does anything of value depends on the site you are injecting it on. closed console defaultStatus document frameElement frames history innerHeight innerWidth length localStorage location name navigator opener outerHeight outerWidth pageXOffset pageYOffset parent screen screenLeft screenTop screenX screenY sessionStorage self status top alert() atob() blur() btoa() clearInterval() clearTimeout() close() confirm ...
My problem is that the browser does the authorization automatically, and with jQuery and JavaScript methods you can only set the requestheaders and get the responseheaders. I couldn't find a method to get the requestheaders. The library gethttp could get some headers, but not the authorization header. My guess is that this header is hidden. 8/10/2012 · 5 Answers5. Active Oldest Votes. 3. Trick is right... in particular you need to put any past-value in the expires header. (These days you'd use a full-year, though; the two-digit format goes back to the early Netscapes only.) Also ensure you don't use smart quotes like in your quote above. javascript:alert (document.cookie='PREF=X;path=/;domain=. Yêu cầu biết : HTML, Javascript, Firefox, email View-source thấy như sau. Làm tương tự Mission 4, sẽ nhận được thông báo Điều này có nghĩa là phí server có kiểm tra referer, referer cho biết form ta gửi đến có phải từ chính trang hackthissite hay không ?
Get in touch with 老子 (@Gettre) — 495 answers, 353 likes. Ask anything you want to learn about 老子 by getting answers on ASKfm. Feb 28, 2019 - HackThisSite I'll be going through the HackThisSite basic missions in this walk-through/experience. I'll be completing all missions through the Firefox web browser. Basic Missions 1. The first basic mission is beyond easy. Simply inspect the element of the page and when you get near the ... javascript: alert (document. cookie); Second, to edit a certain value use: javascript: void (document. ... The value can be changed to yes with the following code: javascript: void (document. cookie = "active=yes"); If the field’s name does not exist, it will be created.
Definition and Usage. The host property sets or returns the hostname and port of a URL. Note: If the port number is not specified in the URL (or if it is the scheme's default port - like 80, or 443), some browsers will not display the port number. Cookies, document.cookie. Cookies are small strings of data that are stored directly in the browser. They are a part of the HTTP protocol, defined by the RFC 6265 specification. Cookies are usually set by a web-server using the response Set-Cookie HTTP-header. Then, the browser automatically adds them to (almost) every request to the same ... 18/8/2021 · This command can either alter existing information or create entirely new values. Replace “Field” with either an existing field found using the alert(document.cookie); command, or insert your very own value. Then replace “myValue” with whatever you want the field to be. For Example: Code: javascript:void(document.cookie="Authorized=yes");
Well yes, the access exception is due to the fact that document.domain must match in your parent and your iframe, and before they do, you won't be able to programmatically set the document.domain property of your iframe.. I think your best option here is to point the page to a template of your own: iframe.src = '/myiframe.htm#' + document.domain; Under the cookie tab you will the cookie named ‘level10_authorized‘ having the value as ‘no’, all you need to do is change it to ‘yes’ and press submit. What did we learn? Cookie are small units of data, almost every site that you visit sets a cookie on your browser, Most of the times they are encrypted and are not a threat, but one ... Last Friday's mission was to accomplish solving HackThisSite, basic mission 10. This mission teaches us how to use JavaScript to manipulate cookies on poorly coded cookie-based authorization.
Share alerts. Authorized users can share an alert with other app users by editing the alert permissions. When sharing an alert with a user without the Admin or Power role, the user needs permission to access the alerting features. For example, a user needs the capability to run a real-time search in order to access a real-time alert. The contentDocument property returns the Document object generated by a frame or iframe element. This property can be used in the host window to access the Document object that belongs to a frame or iframe element. Note: Because of security reasons, the contents of a document can be accessed from another document only if the two documents are ... Now we must change the value of the cookie called "level10_authorized" to "yes", and to do this, we can use raw Javascript or use a firefox addon such as Tamper Data, Firebug, etc... We use JavaScript: while on the 10th mission webpage enter this JavaScript code in the address bar: javascript:function a(){document.cookie...
<script>alert(document.cookie)</script> If this script is being executed, then there is a huge possibility, that XSS is possible. Also while testing manually for possible Cross Site Scripting attack, it is important to remember, that encoded brackets should also be tried. Client side read/write: document.cookie " Setting a cookie in Javascript: document.cookie = “name=value; expires=…; ” " Reading a cookie: alert(document.cookie) prints string containing all cookies available for document (based on [protocol], domain, path) " Deleting a cookie: document.cookie = “name=; expires= Thu, 01 … The next time you open your HTML file, it should be the previous file you've chosen. JavaScript code: function cssLayout() { document.getElementById("css").href = this.value;}function setCookie(){ var date = new Date("Februari 10, 2013"); var dateString = date.toGMTString(); var cookieString = "Css=document.getElementById("css").
With the HTTPOnly attribute turned on, type "javascript:alert(document.cookie)" in the browser address bar. Notice all cookies are displayed except the unique2u cookie. Solution: Follow the instructions. Cross Site Tracing (XST) Attacks. Challenge: Tomcat is configured to support the HTTP TRACE command. Now we can see that we are not authenticated and a whole bunch more irreverent stuff. Umm, how about we try changing this Boolean value? This can be done in a cookie editor or by passing this value to the browser with 'javascript:void(document.cookie="level10_authorized=yes")'. This will get ... JavaScript makes it very easy to edit - just use it to level10_authorized yes. To do this, place the following in the address bar and enter javascript:void (document.cookie'level10_authorized'yes); javascript:void (document.cookielevel10_authorized'yes); Click enter to apply it, and then click to submit leaving
JavaScript. javascript:void (document.cookie='level10_authorized=yes') 1. javascript:void(document.cookie='level10_authorized=yes') You will notice we are changing the cookie value from no to yes. Refresh the page and level 10 is completed. Now this is only one way of doing and there is another very popular way using FireFox's Addon Cookie ... With JavaScript, reading a cookie is very easy. You simply need to use the document.cookie string. And the value of document.cookie will return you the cookie. This string contains a record of the name and value (the string value of the cookie) of a cookie that is isolated by semicolons. 11392f. 775676. 88c21f
Hi is there anyway to remove all cookies saved by single website ? For example i can view the cookie stored by a particle websites by typing following code in bookmarklet. javascript:alert(document. Patrick Talmadge Posted on November 28, 2006 Posted in Hacking. Javascript injection is a fun technique that allows you to change a websites content without leaving the site, reloading the page, or saving the site to your desktop. Javascript injection can be very useful when you need to change hidden data before you send it to the server. By default, a cookie belongs to the page that sets the Cookie. document.cookie = "cookiename=cookievalue; expires= Thu, 21 Aug 2014 20:00:00 UTC; path=/ //create a cookie with a domain to the current page and a path to the entire domain. JavaScript get Cookie. You can access the Cookie like this, which will return all the cookies saved for the ...
alert(iframe.contentWindow.document.cookie); ... If your bank includes Google Analytics Javascript (from google ), can it access your Bank's authentication cookie? Yes! Javascript always runs with the permissions of the window ... Cookies do not indicate whether an authorized application submitted request since they're included in every ... The WebSocket protocol, described in the specification RFC 6455 provides a way to exchange data between browser and server via a persistent connection. The data can be passed in both directions as "packets", without breaking the connection and additional HTTP-requests. WebSocket is especially great for services that require continuous data exchange, e.g. online games, real-time trading ...

 Htsreport Docx Contents 1 0 Introduction 1 2 0 Report 2 2 1
Htsreport Docx Contents 1 0 Introduction 1 2 0 Report 2 2 1
蓝鲸的在hackthissite上的7到js题作业 Willsdims的专栏 Csdn博客
 Hack This Site Basic Level 10 Youtube
Hack This Site Basic Level 10 Youtube
Hackthissite Basic Mission Basic 1 Tes Dasar Keterampilan
 Hack This Site Realistic 12 Tutorial By Cwade12c
Hack This Site Realistic 12 Tutorial By Cwade12c
 Hack This Site Basic 3 Tutorial Spoiler By Cwade12c
Hack This Site Basic 3 Tutorial Spoiler By Cwade12c
 Hackthissite Basic Web Challenges 1 11 By Sampath
Hackthissite Basic Web Challenges 1 11 By Sampath
![]() Hackthissite Basic Level10 Aldeid
Hackthissite Basic Level10 Aldeid
 Goodnight Byte Hackthissite Walkthrough Part 9 Legal
Goodnight Byte Hackthissite Walkthrough Part 9 Legal
Hts Basic Level 10 Gensale Net
 Hack This Site Basic Mission 10 네이버 블로그
Hack This Site Basic Mission 10 네이버 블로그
 Hack This Site Realistic 12 Tutorial By Cwade12c
Hack This Site Realistic 12 Tutorial By Cwade12c

 Hackthissite Basic Missions Learning To Hack The Planet
Hackthissite Basic Missions Learning To Hack The Planet
 Eu Cookie Consent Popup With Javascript
Eu Cookie Consent Popup With Javascript
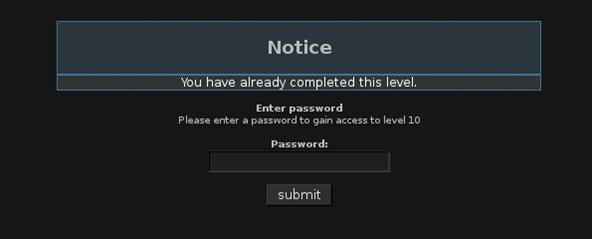 Goodnight Byte Hackthissite Walkthrough Part 9 Legal
Goodnight Byte Hackthissite Walkthrough Part 9 Legal
 Hackthissite Realistic Mission 5 By Chuck Moore
Hackthissite Realistic Mission 5 By Chuck Moore
 Hack This Site Javascript 7 Welcome To Codeingshuang Blog
Hack This Site Javascript 7 Welcome To Codeingshuang Blog
 Hackthissite Basic Missions Level1 10 攻略 台部落
Hackthissite Basic Missions Level1 10 攻略 台部落
 Hackthissite Realistic Mission 5 By Chuck Moore
Hackthissite Realistic Mission 5 By Chuck Moore
 Hackthissite Realistic Mission 5 By Chuck Moore
Hackthissite Realistic Mission 5 By Chuck Moore

 Hackthissite Basic Web Challenges 1 11 By Sampath
Hackthissite Basic Web Challenges 1 11 By Sampath
 Htsreport Docx Contents 1 0 Introduction 1 2 0 Report 2 2 1
Htsreport Docx Contents 1 0 Introduction 1 2 0 Report 2 2 1






0 Response to "32 Javascript Alert Document Cookie Level10 Authorized Yes"
Post a Comment