35 Javascript Escape Sql Injection
How to protect against an HTML Injection Attack. The general rule is this: Treat any user input as unsafe. This means that we need to sanitize any user-provided values. There are a number of ... Mar 03, 2019 - SQL injection is a technique, which used to attack data-driven applications, in which nefarious SQL statements are inserted into an entry field for execution. SQL injection must exploit a security vulnerability in an application, To prevent SQL injection in Node Js, You can escape user input ...
 Protect Your Web Application From Sql Injection Attacks
Protect Your Web Application From Sql Injection Attacks
In this course, Defeating Injection Attacks in ASP.NET and ASP.NET Core, you will gain the ability to defend against common injection attacks in ASP.NET applications. First, you will learn about SQL injection attacks, and how to thwart them. Next, you will discover how injection attacks can be applied to NoSQL, and how to properly defend ...

Javascript escape sql injection. Escape arrays in MySQL queries to prevent SQL injection vulnerabilities. This is especially useful in MySQL IN statements. ... A set helpers for writing dynamic SQL queries with `pg-sql` in Javascript. Developers do not usually generate dynamic SQL inside stored procedures. However, it can be done, but should be avoided. If it can't be avoided, the stored procedure must use input validation or proper escaping as described in this article to make sure that all user supplied input to the stored procedure can't be used to inject ... 8/4/2020 · mysql_real_escape_string () will not protect you against this. The fact that you use single quotes (' ') around your variables inside your query is what protects you against this. The following is also an option: $iId = (int)"1 OR 1=1"; $sSql = "SELECT * FROM …
Moreover, all the danger is coming from the very statement in question: zounds of PHP users still do believe that the notorious mysqli_real_escape_string() function's only purpose is "to protect SQL from injections" (by means of escaping some fictional "dangerous characters"). If only they ... The addslashes () is sometimes incorrectly used to try to prevent SQL Injection. Instead, database-specific escaping functions and/or prepared statements should be used. Why SQL Injection Matters. Standardized query language (SQL) is, in one form or another, still the dominant method of inserting, filtering and retrieving information from a database. Loads of SQL queries will be coursing through your web applications on almost every page load - regardless of if it's a tiny toy website with a tiny SQLite ...
Escaping characters prevents SQL injection. Injections occur when characters are not escaped, and malicious users can exploit this to close the query and start a new one to, say, drop a table or insert a fake record. With escaped characters, this is not possible. Wikipedia has some additional information on SQL Injection. Nov 29, 2018 - In this blog post, we discuss the research on Fragmented SQL Injection where the hackers control two entry points in the same context in order to bypass the authentication form. Our security researcher looks at the importance of single quotes and the solution, Prepared Statements. Nov 23, 2012 - SQL injection is possible despite using mysql.escape: var object = { 'a` = 2; INSERT INTO test_inject SET `a': 1 }; conn.query('INSERT INTO test_inject SET ?', objec...
SQL injection is one of the most common types of vulnerabilities found in web applications. Today, I'm going to explain what SQL injection attacks are and walk you through the process of exploiting a simple Spring Boot-based application. After we've exploited this simple Java app, we'll then learn how to fix the problem. Sound fun? Let's do it! Prerequisites Before starting, make sure you have ... SQL injection attacks are staged by sending malicious SQL commands to database servers through web requests. Any input channel can be used to send the malicious commands, including <input ... When you pass an Object to .escape() or .format(), .escapeId() is used to avoid SQL injection in object keys. Formatting queries You can use SqlString.format to prepare a query with multiple insertion points, utilizing the proper escaping for ids and values.
The SQL Injection usually occurs when you ask a user for input, like their name and instead of a name they give you a MySQL statement that you will unknowingly run on your database. Never trust the data provided by a user, process this data only after validation; as a rule, this is done by pattern matching. Aug 02, 2019 - SQL injections are one of the most utilized web attack vectors, used with the goal of retrieving sensitive data from organizations. When you hear about stolen credit cards or password lists, they often happen through SQL injection vulnerabilities. Fortunately, there are ways to protect your ... A SQL injection is a type of vulnerability that gives users access to the database associated with an application, allowing them to execute SQL queries. Using this access, an attacker can retrieve information from the database in an unauthorized way (especially from those tables that aren't typically accessible by users).
Aug 06, 2015 - In this multipart series, we will explore some of the the OWASP top web application security flaws including how they work and best practices to protect your application from them. The focus will be … May 25, 2019 - The code above utilizes the prepared ... escaped. Finally, stick to the Principal of Least Privilege. This principle applies across architecture and tends to be something every computer scientist learns early in their career so I won’t elaborate, check out Wikipedia if you need a refresher. ... SQL injection attacks have ... Jun 29, 2018 - SQL Injections occur when improperly escaped strings are concatenated to generate SQL queries.
26/2/2019 · Exploiting SQL Injection: a Hands-on Example. In this series, we will be showing step-by-step examples of common attacks. We will start off with a basic SQL Injection attack directed at a web application and leading to privilege escalation to OS root. SQL Injection is one of the most dangerous vulnerabilities a web application can be prone to. Caution These methods of escaping values only works when the NO_BACKSLASH_ESCAPES SQL mode is disabled (which is the default state for MySQL servers). In order to avoid SQL Injection attacks, you should always escape any user provided data before using it inside a SQL query. SQL injection must exploit a security vulnerability in an application's software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed.
The HTML, JavaScript and URL encoders are available to your code in two ways, you can inject them via dependency injection or you can use the default encoders contained in the System.Text.Encodings.Web namespace. If you use the default encoders then any you applied to character ranges to be treated as safe won't take effect - the default ... Three of the top five most common website attacks - SQL injection, cross-site scripting (XSS), and remote file inclusion (RFI) - share a root cause in common: input sanitization. Or to be more ... From my understanding, PHP's implementation of prepared statements, among other things, helped greatly in the prevention of SQL injections. I'm worried, though, that my node.js app may be open to similar attacks, even with the string escaping provided by default (as in the code snippet below).
SQL injection attacks can also be used to change data or damage the database. The SQL injection hacker might enter the following into the txtFilter textbox to change the price of the first product from $18 to $0.01 and then quickly purchase a few cases of the product before anyone notices what has happened: SQL injection cheat sheet. This SQL injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. String concatenation. You can concatenate together multiple strings to make a single string. SQL injection is a type of attack where a malicious user is able to execute arbitrary SQL code on a database. This can result in records being deleted or data leakage. Django's querysets are protected from SQL injection since their queries are constructed using query parameterization. A query's SQL code is defined separately from the query ...
While Node.js can help improve developer productivity, it's prone to SQL injection bugs as much as any other modern programming language in use today. In this article, we walk through a SQL injection issue, it's impact, and how to fix it. A classic example using MySQL Imagine a web app that requires you to verify your bank account so you can access your personal funds. Upon verifying some ... Structured Query Language Injection (SQLI) is a potentially devastating use of a code injection vulnerability specifically targeting the database query language SQL. SQL injection is the result of... javascript sql sql-server sqlite-database android-application sql-injection java-8 html-css nsu-cse327 ... sql escape sql-injection mssql tsql querybuilder tedious Updated ... 3 adet açık içeren (XSS, SQL Injection, Script) basit bir web uygulaması geliştirip sunum sırasında bunlara saldırı yapmak ve saldırılardan nasıl ...
Escape JavaScript before putting untrusted data inside data values. ... What is the difference between XSS and SQL injection? The main difference is that the target in XSS is the end user, while SQL injection modifies the logic of database queries on the server side. Jan 17, 2019 - I am using Security Shepherd as a training tool and I am now in the challenge, SQL Injection Escaping Challenge. The Challenge: When I make a query just like the one above (just with different t... One among that is Javascript Injection. OutSystems escapes all content before showing it to the user, by default. However, the developer can explicitly disable this mechanism if there is the need to inject custom HTML or Javascript, likely to prevent SQL injection. You need to take care when you do this.
14/11/2020 · SQL injection is a technique used to exploit user data through web page inputs by injecting SQL commands as statements. Basically, these statements can be used to manipulate the application’s web server by malicious users. SQL injection is a code injection technique that might destroy your database. Escapes the characters in a String using Java String rules. Deals correctly with quotes and control-chars (tab, backslash, cr, ff, etc.) So a tab becomes the characters '\\' and 't'. The only difference between Java strings and JavaScript strings is that in JavaScript, a single quote must be escaped. Example: 27/4/2017 · 3 Answers3. The best way to is to use prepared statements or queries (link to documentation for NPM mysql module: https://github /mysqljs/mysql#preparing-queries) If prepared statements is not an option (I have no idea why it wouldn't be), a poor man's way to prevent SQL injection is to escape all user-supplied input as described here: ...
May 17, 2019 - With all the talk about working with databases using MySQL and PHP in this tutorial series, one thing we didn't cover yet is SQL Injection and how to protect your site from it. The syntax for MySQL is very specific, and if you don't get it right, it is easy to break. As we build… Almost all SQL databases are based on the RDBM (Relational Database Model) One important fact for SQL Injection Amongst Codd's 12 rules for a Truly Relational Database System: 4. Metadata (data about the database) must be stored in the database just as regular data is Therefore, database structure can also be read and Structured Query Language (SQL) is a language designed to manipulate and manage data in a database. Since its inception, SQL has steadily found its way into many commercial and open source databases. SQL injection (SQLi) is a type of cybersecurity attack that targets these databases using specifically crafted SQL statements to trick the systems ...
Jun 03, 2017 - It's absolutely vital to sanitize user inputs to insure that they do not contain dangerous codes, whether to the SQL server or to HTML itself. One's first idea is to strip out "bad stuff", such as quotes or semicolons or escapes, but this is a misguided attempt. Apr 16, 2020 - Caution These methods of escaping values only works when the NO_BACKSLASH_ESCAPES SQL mode is disabled (which is the default state for MySQL servers). In order to avoid SQL Injection attacks, you should always escape any user provided data before using it inside a SQL query. Escaping inputs - It is a simple way to protect against most SQL injection attacks. Many languages have standard functions to achieve this. You need to be aware while using escape characters in your code base where an SQL statement is constructed. Some of the other methods used to prevent SQL Injection are:
Nov 17, 2011 - I realize that parameterized SQL queries is the optimal way to sanitize user input when building queries that contain user input, but I'm wondering what is wrong with taking user input and escaping...
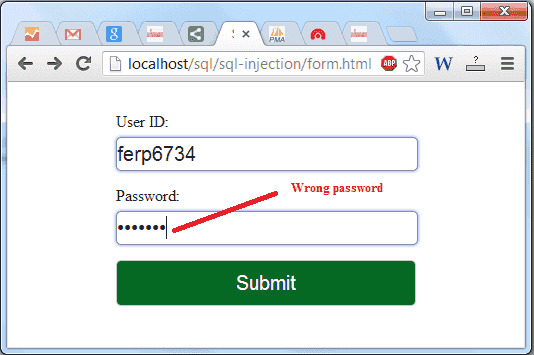 Sql Injection Tutorial W3resource
Sql Injection Tutorial W3resource
 Fragmented Sql Injection Attacks The Solution Netsparker
Fragmented Sql Injection Attacks The Solution Netsparker
 Sql Injection Testing Tutorial Example And Prevention Of Sql
Sql Injection Testing Tutorial Example And Prevention Of Sql
 Securing Applications In Node Js Sql Injection In Action Packtpub Com
Securing Applications In Node Js Sql Injection In Action Packtpub Com
 Injection And Cross Site Script Xss Outsystems
Injection And Cross Site Script Xss Outsystems
 How To Prevent Sql Injection Attacks And Defense Techniques
How To Prevent Sql Injection Attacks And Defense Techniques
 Preventing Sql Injection In Node Js And Other Vulnerabilities
Preventing Sql Injection In Node Js And Other Vulnerabilities
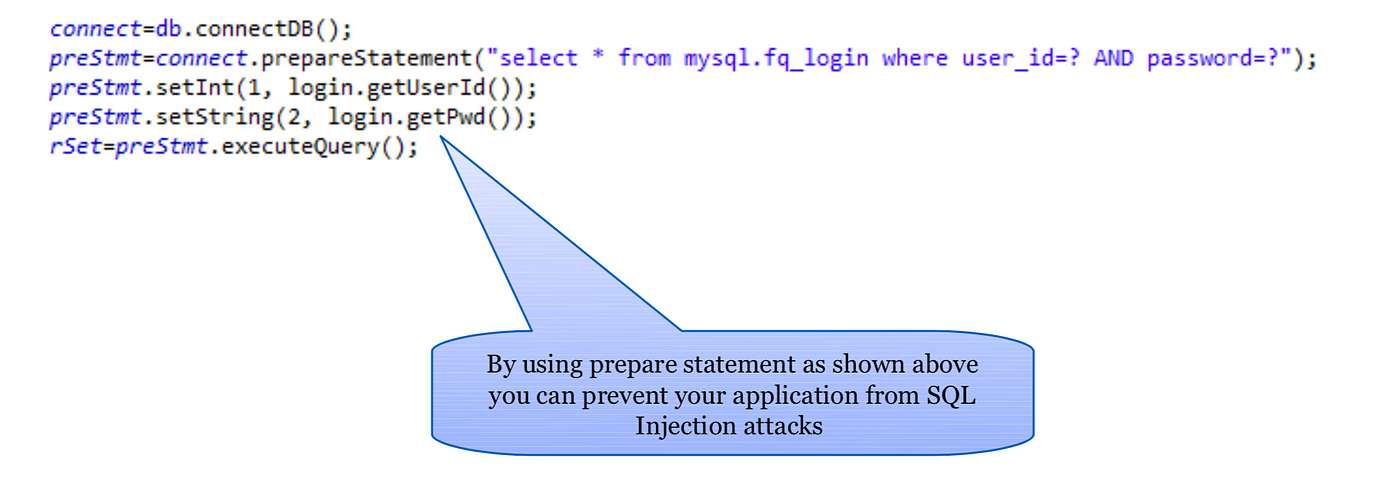 Preventing Sql Injection And Xss Attacks By Lakshmi
Preventing Sql Injection And Xss Attacks By Lakshmi
 How To Escape Sanitise Untrusted Data Params In Sql Queries
How To Escape Sanitise Untrusted Data Params In Sql Queries


 Sql Injection Attacks Know How To Prevent Them Dzone Security
Sql Injection Attacks Know How To Prevent Them Dzone Security
 Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
 What Is Sql Injection Amp How To Prevent It Netsparker
What Is Sql Injection Amp How To Prevent It Netsparker
 How Hackers Take Over Web Sites With Sql Injection And Ddos
How Hackers Take Over Web Sites With Sql Injection And Ddos
 Sql Injection And Cross Site Scripting Codeproject
Sql Injection And Cross Site Scripting Codeproject
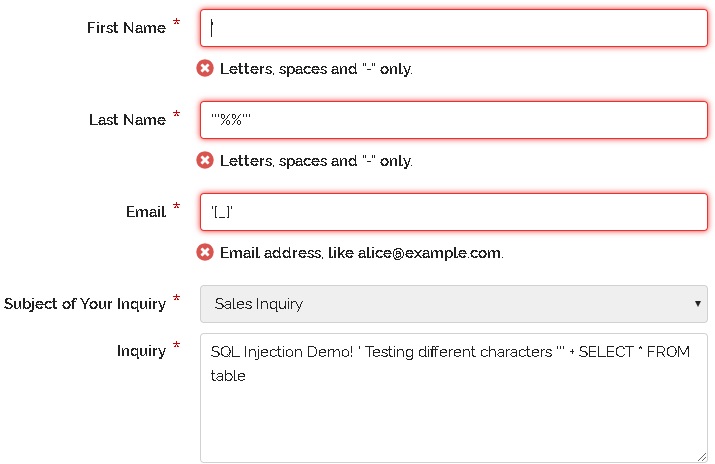 Sql Injection Detection And Prevention
Sql Injection Detection And Prevention
 Sql Injection Attacks How To Really Stay Safe Alex Web
Sql Injection Attacks How To Really Stay Safe Alex Web
 5 Ways To Prevent Code Injection In Javascript And Node Js
5 Ways To Prevent Code Injection In Javascript And Node Js
 Preventing Sql Injections In Java And Other Vulnerabilities
Preventing Sql Injections In Java And Other Vulnerabilities
 Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
 Fixing Sql Injection Orm Is Not Enough Snyk
Fixing Sql Injection Orm Is Not Enough Snyk
 How To Prevent Sql Injection Attacks And Defense Techniques
How To Prevent Sql Injection Attacks And Defense Techniques
 Bypass Login Using Sql Injection
Bypass Login Using Sql Injection
 How To Protect Your Website Against Sql Injection Attacks
How To Protect Your Website Against Sql Injection Attacks
 5 Ways To Prevent Code Injection In Javascript And Node Js
5 Ways To Prevent Code Injection In Javascript And Node Js
Preventing Sql Injection Issue 512 Dmfay Massive Js Github
 Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
Sql Injection Cheat Sheet 8 Best Practices To Prevent Sql
 How To Prevent Nosql Injections In Mongodb In A Node Js App
How To Prevent Nosql Injections In Mongodb In A Node Js App
 Exploiting Sql Injection A Hands On Example Acunetix
Exploiting Sql Injection A Hands On Example Acunetix
 Common Sql Injection Attacks Pentest Tools Com Blog
Common Sql Injection Attacks Pentest Tools Com Blog
 What Is Sql Injection Sql Injection Prevention Veracode
What Is Sql Injection Sql Injection Prevention Veracode
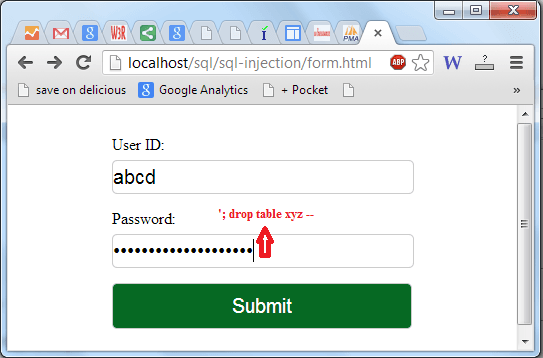 Sql Injection Tutorial W3resource
Sql Injection Tutorial W3resource
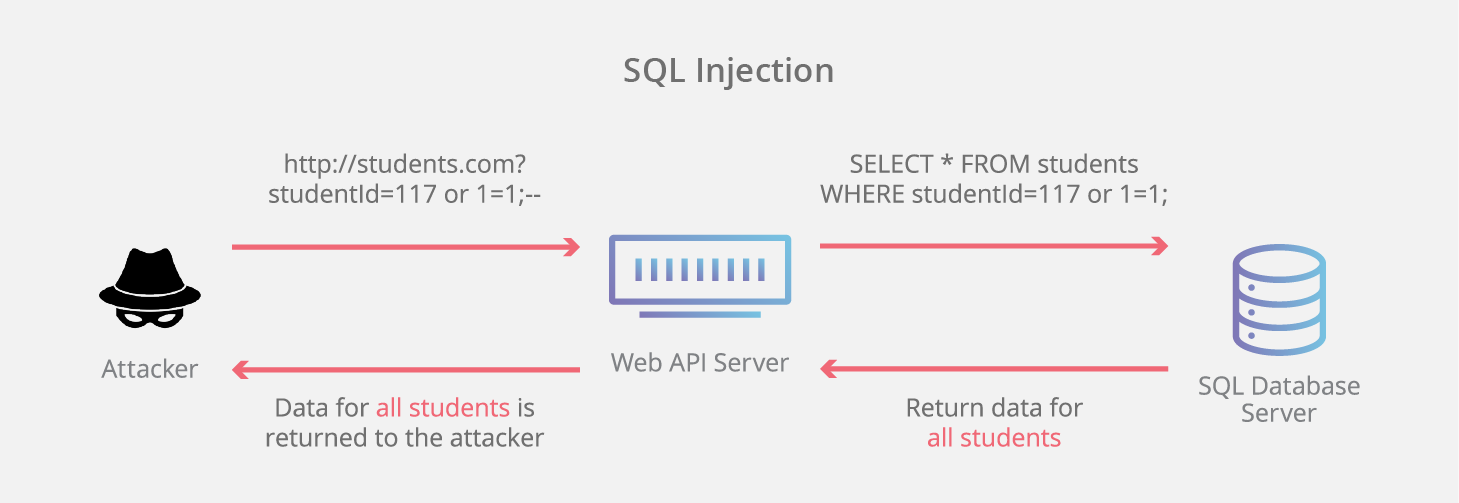 What Is Sql Injection Cloudflare
What Is Sql Injection Cloudflare
0 Response to "35 Javascript Escape Sql Injection"
Post a Comment