29 Javascript Steal Session Cookie
XSS Cookie Stealing Attack The example shows how the attacker could use an XSS attack to steal the session token. If an attacker sends a crafted link to the victim with the malicious JavaScript, when the victim clicks on the link, the JavaScript will run and complete the instructions made by the attacker.
 What Is Json Hijacking Or Javascript Hijacking The
What Is Json Hijacking Or Javascript Hijacking The
javascript cookies session-management angularjs. Share. Improve this question. ... within your web app can steal the token and hijack the session to impersonate the victim, even after the victim closes the browser (by contrast, the typical session cookie is flagged as httponly, ...
Javascript steal session cookie. Cookies are often used in web applications to identify a user and their authenticated session. Stealing a cookie from a web application leads to hijacking the authenticated user's session. Common ways to steal cookies include using social engineering or by exploiting a cross-site scripting (XSS) vulnerability in the application - In computer science, session hijacking, sometimes also known as cookie hijacking is the exploitation of a valid computer session—sometimes also called a session key—to gain unauthorized access to information or services in a computer system. In particular, it is used to refer to the theft of a magic cookie used to authenticate a user to a remote server. You can secure your site right now by installing a Session Hijacking & Cookie Stealing Protection Plugin. It will scan your website regularly and alert you if a hacker injects any malicious code that will enable them to steal cookies. Using the plugin, you can clean up the hack promptly & avoid repercussions. What Is Cookie Stealing?
*ONLY FOR EDUCATIONAL PURPOSES*In this video, we are going to learn how we can sniff cookies of any user in our network. The use for cookies stealing comes w... As stated earlier, when we request a webpage to a server the server contacts that site and renders the webpage to our local machine. While rendering the webpage which is mostly HTML, CSS & some JavaScript along with that it also sends a cookie (1st party cookie) which identifies the session. In order to steal cookies, a cookie must first be available on the web domain the user is viewing. This happens whenever the user views the website. While it's absolutely possible to inject JavaScript into websites using a man-in-the-middle attack, or by exploiting a vulnerable website, both of these would require additional effort to implement.
It is commonly used to run malicious javascript in the browser to do attacks such as stealing session cookies among other malicious actions to gain higher level privileges in the application. Local File Inclusion A vulnerability in the application caused by the programmer requiring a file input provided by the user and not sanitizing the input ... Session hijacking is a technique used to take control of another user's session and gain unauthorized access to data or resources. For web applications, this means stealing cookies that store the user's session ID and using them to fool the server by impersonating the user's browser session. If successful, the attacker can act as a legitimate application user, steal money or valuable ... Cookie Stealing with Non-Persistent vs Persistent XSS: Persistent: if you inject this code in Persistent XSS vulnerable site, it will be there forever until admin find it. It will be shown to all users.
As demonstrated, the application had an evident stored XSS vulnerability that allowed the attacker to steal administrator user's cookies, including the session token. The XSS would have much less impact if the cookie was stored with http-only flag, thus making it inaccessible from javascript. Steal Web Session Cookie An adversary may steal web application or service session cookies and use them to gain access to web applications or Internet services as an authenticated user without needing credentials. Web applications and services often use session cookies as an authentication token after a user has authenticated to a website. The session cookie is marked as httpOnly So javascript would not access it But the session is returned in response body, Javascript would not access the cookie but it can access the response body...
Protecting your sensitive cookies is very important as stolen session cookie means an attacker can take your identity and wreak havoc. ... Alright, we've mitigated the risk that the attacker will steal or change our cookies from javascript. But there are more ways to steal our cookies. One of them is in-transit. You want to make it do something useful, like steal cookies. Cookie stealing is when you insert a script into the page so that everyone that views the modified page inadvertently sends you their session cookie. By modifying your session cookie (see the above linked tutorial), you can impersonate any user who viewed the modified page. If the victim followed that link, the hacker can use that session and gain access. 2. Session SideJacking(session Sniffing): In this method, the attacker use packet sniffing to and steal the Session cookie. In order to prevent this, some websites use SSL(encrypts the session). but do not use encryption for the rest of the site once authenticated.
HttpOnly cookies are inaccessible to JavaScript's Document.cookie API; they are only sent to the server. For example, cookies that persist server-side sessions don't need to be available to JavaScript, and the HttpOnly flag should be set. His objective is to set up a XSS attack to steal the admin session cookie, send it to him, and use it to gain access to the admin account. In this scenario the server running our DVWA site is a Windows computer with the IP address of 192.168.1.16 . PHP Cookies and JavaScript Cookies. We all know that in PHP, to set a session only cookie, all you need to do is leave the expire parameter blank or set it to ZERO (0). Of course we always need to set the path to "/" in most cases. However, it is quite different when it comes to JavaScript. The syntax for setting up cookie in JavaScript is ...
The key here being whether you can output arbitrary JavaScript or whether you're limited in the kind of JavaScript you can get executed. Though if you're limited in what can be output you could use more advanced methods of getting your custom code to execute which are a bit out of scope of the question. Cross-site scripting (XSS) attacks are often aimed at stealing session cookies. In such an attack, the cookie value is accessed by a client-side script using JavaScript (document.cookie). However, in everyday use, web applications rarely need to access cookies via JavaScript. When the script runs, it lets the hacker steal the cookie. Server or application vulnerabilities are exploited to inject client-side scripts (usually JavaScript) into webpages, leading the browser to execute the code when it loads the compromised page.
The web-server uses the Set-Cookie header to set a cookie. Also, it may set the httpOnly option. This option forbids any JavaScript access to the cookie. We can't see such a cookie or manipulate it using document.cookie. Level : Medium - Hard. My previous tutorial was talking about how to perform Basic Hacking via Cross Site Scripting (XSS) that has a relations with today tutorial.. As I have already wrote on my previous post about two types of Cross Site Scripting (XSS) there is Non-persistent and persistent attack which non persistent data was provided by a web client, and persistent type if the server ... It is easy to steal session id cookies with javascript functions planted in trusted sites by other users. What are the possible counter-measures for this kind of attack? Rejecting all javascript scripts on the client-side is probably difficult because almost all sites use js. What are the possible counter-measures on the server-side?
JavaScript can create, read, and delete cookies with the document.cookie property. With JavaScript, a cookie can be created like this: document.cookie = "username=John Doe"; You can also add an expiry date (in UTC time). Currently the Session ID and the Cookie details of the Attacker was : Now accessing the Web Server by the Victim Machine which is having the Administrator Privileges, the Attacker will steal the...
 Is Your Session Hijacked How To Prevent Session Hijacking
Is Your Session Hijacked How To Prevent Session Hijacking
 Session Hijacking Or Cookie Stealing Using Php And Javascript
Session Hijacking Or Cookie Stealing Using Php And Javascript
 What Is Session Hijacking And How Can You Prevent It
What Is Session Hijacking And How Can You Prevent It
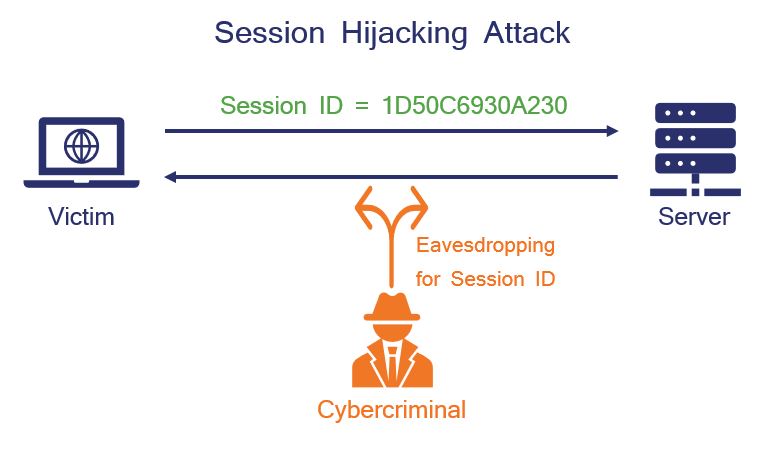 The Ultimate Guide To Session Hijacking Aka Cookie Hijacking
The Ultimate Guide To Session Hijacking Aka Cookie Hijacking
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
Webhacking101 Xss Reflected Steal Cookie Md At Master
 Securing Your Cookies Httponly Flag For Cookie Theft Defense
Securing Your Cookies Httponly Flag For Cookie Theft Defense
 Hackfi How To Steal Session Cookies
Hackfi How To Steal Session Cookies
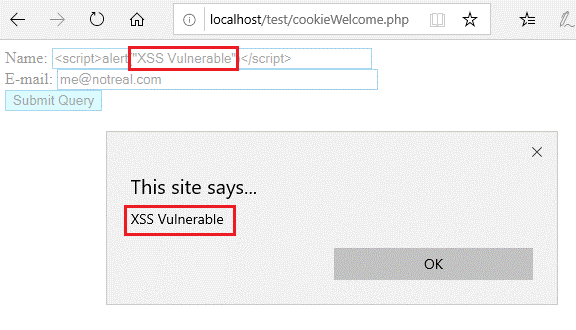 Securing Your Cookies Httponly Flag For Cookie Theft Defense
Securing Your Cookies Httponly Flag For Cookie Theft Defense
 What Is Session Hijacking How To Ensure Session Privacy
What Is Session Hijacking How To Ensure Session Privacy
 What Is Session Hijacking Your Quick Guide To Session
What Is Session Hijacking Your Quick Guide To Session
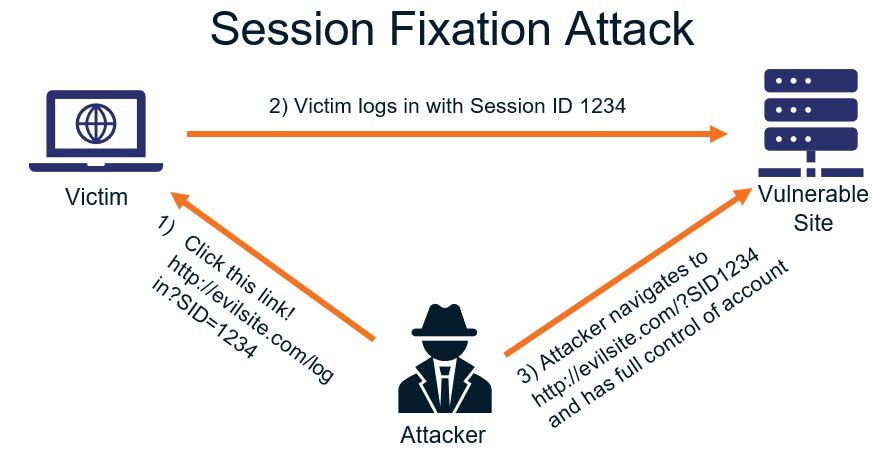 The Ultimate Guide To Session Hijacking Aka Cookie Hijacking
The Ultimate Guide To Session Hijacking Aka Cookie Hijacking
 How To Write An Xss Cookie Stealer In Javascript To Steal
How To Write An Xss Cookie Stealer In Javascript To Steal
Session Hijacking And Session Riding Lucideus Malware
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
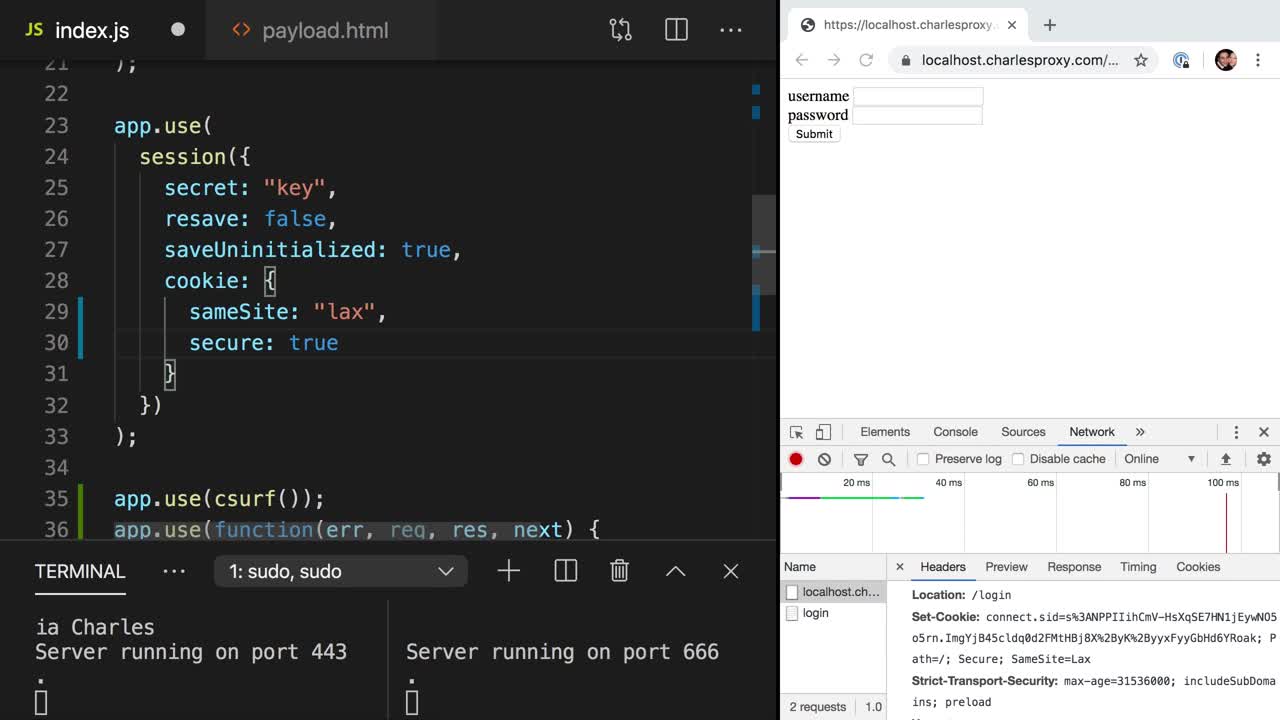 Set The Httponly Cookie Flag In Express To Ensure Cookies Are Inaccessible From Javascript
Set The Httponly Cookie Flag In Express To Ensure Cookies Are Inaccessible From Javascript
 Steal Web Session Cookies From Facebook In Chrome
Steal Web Session Cookies From Facebook In Chrome
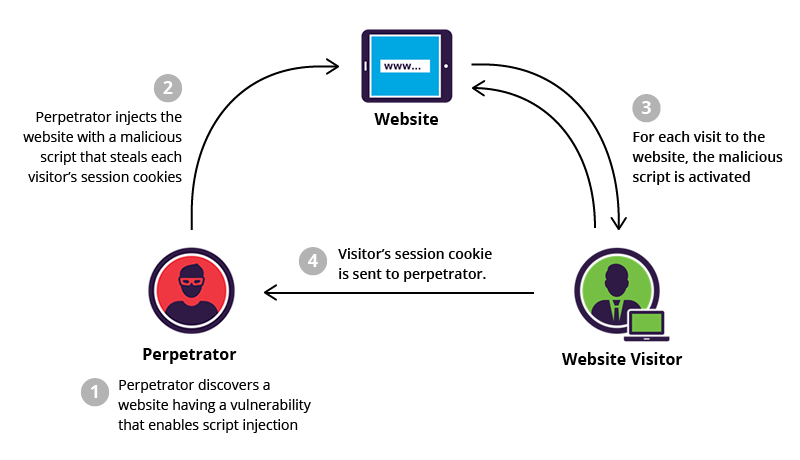 What Is Xss Stored Cross Site Scripting Example Imperva
What Is Xss Stored Cross Site Scripting Example Imperva
 Cookie Theft With Cross Site Scripting Xss Laconic Wolf
Cookie Theft With Cross Site Scripting Xss Laconic Wolf
 Kbid 39 Httponly Session Hijacking Xss Write Ups
Kbid 39 Httponly Session Hijacking Xss Write Ups
 How Can You Steal Cookies From Chrome Information Security
How Can You Steal Cookies From Chrome Information Security
 Cookie Hijacking Protection Web App Firewall
Cookie Hijacking Protection Web App Firewall
 Fake Wordprssapi Stealing Cookies And Hijacking Sessions
Fake Wordprssapi Stealing Cookies And Hijacking Sessions
 Session Hijacking Cookie Stealing Wordpress Malware Spotted
Session Hijacking Cookie Stealing Wordpress Malware Spotted
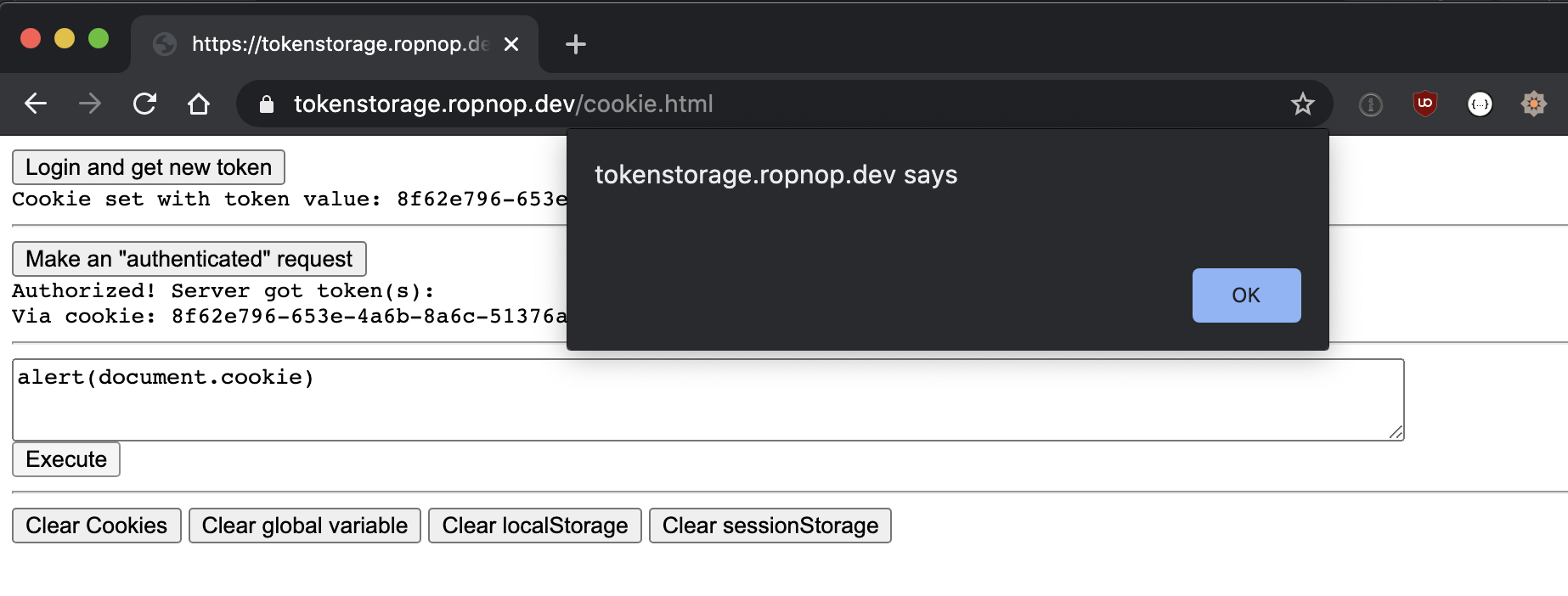 How To Store Session Tokens In A Browser And The Impacts Of
How To Store Session Tokens In A Browser And The Impacts Of
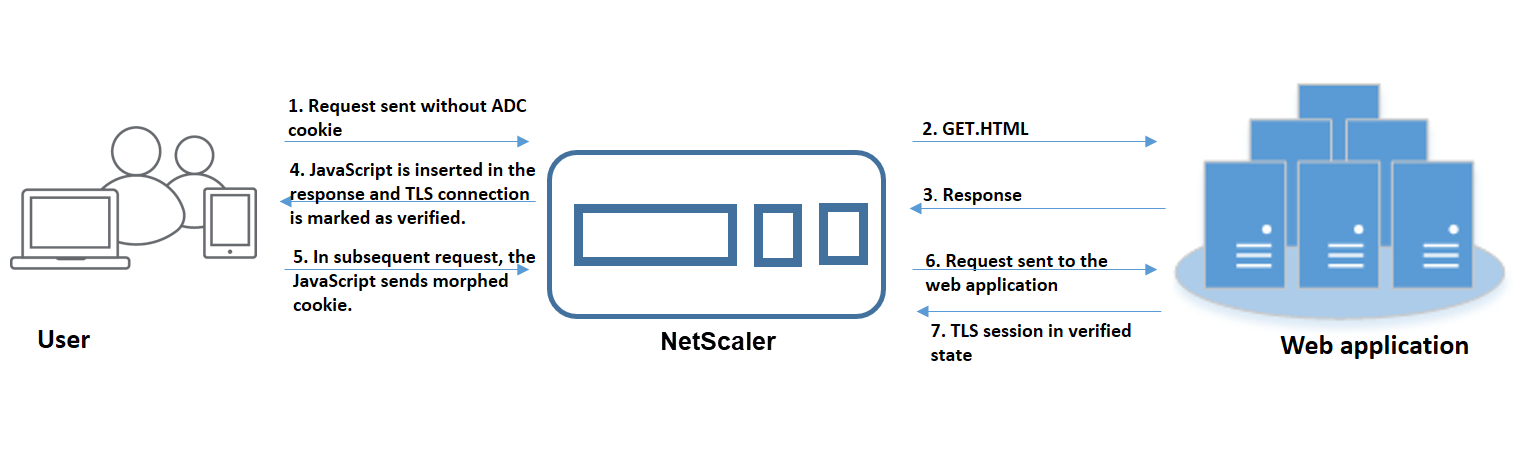 Cookie Hijacking Protection Web App Firewall
Cookie Hijacking Protection Web App Firewall
 Predizione Sospettare Meta Stole Cookies Php Nave Da Guerra
Predizione Sospettare Meta Stole Cookies Php Nave Da Guerra
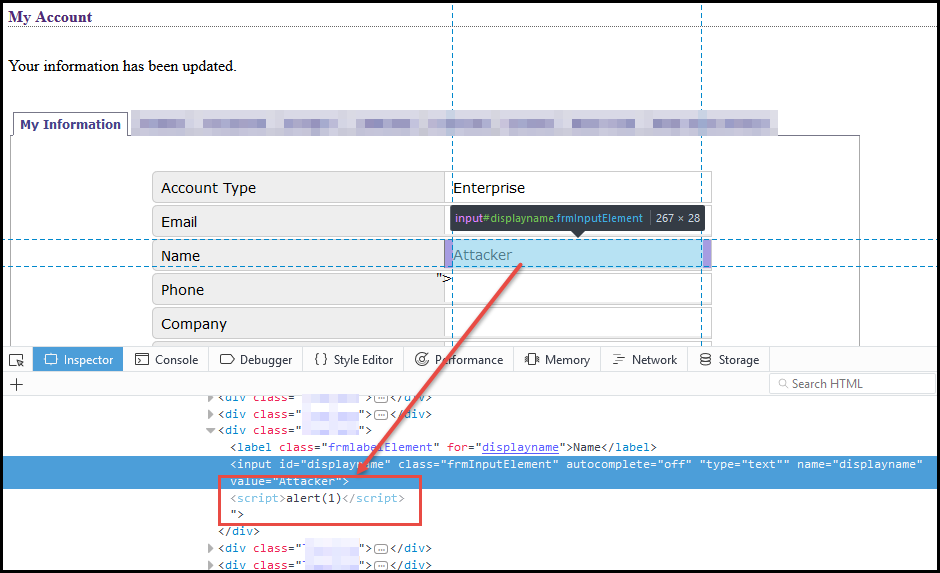
0 Response to "29 Javascript Steal Session Cookie"
Post a Comment