27 Javascript Secure Coding Guidelines
JavaScript Web Application Secure Coding Practices is a guide written for anyone who is using the JavaScript Programming Language for web development. The main goal of this guide is to help developers avoid common mistakes while, at the same time, learning a new programming language through a hands-on approach. Nov 06, 2011 - What are the established coding standards for JavaScript?
 Security Code Review 101 Code Review Is Hopefully Part Of
Security Code Review 101 Code Review Is Hopefully Part Of
Secure Coding Guidelines To achieve security, it is very essential to have a 'Secure Coding standard' identified for a program at the very beginning of the application development, and this helps the team in taking care of the Secure Defaults for the software and help to protect it from the attacks.

Javascript secure coding guidelines. It provides a more complete set of security-specific coding guidelines targeted at the Java programming language. These guidelines are of interest to all Java developers, whether they create trusted end-user applications, implement the internals of a security component, or develop shared Java class libraries that perform common programming tasks. can execute code on the same system as an application may be able to access such data if the application, That uses objects to return any sensitive data whose contents are not cleared or junk-collected right after use. Noncompliant Code: The following code reads the username & password from the console and stores the password General Guidelines The secure coding practice strongly suggests that the developer should only use the approved tools, secure language subset and coding standard should maintain. Static code analysis has to be done here to find the coding errors and issues. Some common tools for .NET platform are: FxCop
Oct 15, 2020 - You do not want to use any broken ... worse, code with intentionally malicious scripts. ... Adopting good coding practices can secure applications against common JavaScript vulnerabilities on both the client-side and server-side. When using JavaScript, always follow the following key guidelines for enhanced ... Secure Coding Guidelines. This guide walks you through the most common security issues Salesforce has identified while auditing applications built on or integrated with the Lightning Platform. This guide takes into account that many of our developers write integration pieces with the Lightning Platform and includes examples from other web ... When designing and writing your code, you need to protect and limit the access that code has to resources, especially when using or invoking code of unknown origin. So, keep in mind the following techniques to ensure your code is secure: Do not use Code Access Security (CAS). Do not use partial trusted code.
Formatting Guidelines # Formatting Guidelines. The following guidelines should be followed to ensure that the content of the doc blocks can be parsed properly for inclusion in the code reference. Short descriptions: Short descriptions should be a single sentence and contain no markup of any kind. For more information about CSPs refer to these guidelines. 5. Always Keep Strict Mode On. Having Strict mode on will limit you from writing unsafe code. Besides, its straightforward to enable this mode. It's as simple as adding the below line as the first in your JavaScript files. use strict. When the strict mode is on; Overview. By using Kintone's "JavaScript / CSS Customization" features, the UI and features of Kintone and it's Applications can be customized. This page introduces guidelines for Kintone JavaScript customization that you should read before you start coding for Kintone customizations.
Guidelines exist for secure coding in general, language-specific coding, and Oracle Solaris-specific coding and tools. The following web sites track coding vulnerabilities and promote secure coding practices: Common Weakness Enumeration. National Vulnerability Database Version 2.2. CERT Secure Coding Standards. ISO/IEC JTC 1/SC 22/ WG 23 ... Institute of Information Security offers Java Script Web Applications Development Training in Mumbai, Delhi, Chandigarh, Pune, Noida, Hyderabad, Bengaluru. Feb 16, 2019 - The OWASP Cheat Sheet Series project provides a set of concise good practice guides for application developers and defenders to follow.
JavaScript Coding Conventions. Coding conventions are style guidelines for programming. They typically cover: Naming and declaration rules for variables and functions. Rules for the use of white space, indentation, and comments. Programming practices and principles; Coding conventions secure quality: Improves code readability; Make code ... Google JavaScript Style Guide 1 Introduction. This document serves as the complete definition of Google's coding standards for source code in the JavaScript programming language. A JavaScript source file is described as being in Google Style if and only if it adheres to the rules herein.. Like other programming style guides, the issues covered span not only aesthetic issues of formatting ... Apr 09, 2021 - However, that’s the wrong way to approach JavaScript security. To avoid XSS, you should avoid inserting HTML directly into the document and instead, programmatically create DOM nodes and append them to the DOM. This means avoiding .html(), .innerHTML, and other related functions, and instead ...
The secure coding guidelines page is a living document and constantly updated to reflect new recommendations and techniques. Information that is listed is accurate and can be immediately used to bolster security in your application. If you have comments, suggestions or concerns please email mcoates <at> mozilla How should Secure Coding Practices address the use of ActiveX? I would like to see some mention of where the use of ActiveX falls in relation to the above guidelines. This is still a very popular methodology involving a lot of expense which probably leads to violating some of the above guidelines, ... Nov 28, 2017 - You need to enable JavaScript to run this app
A multi-pronged approach for preventing JavaScript security issues in source code should include: Improving awareness of best practices among developers Proper auditing of application code to detect potential vulnerabilities Writing unit tests not only to ensure that code behaves as expected, but also that it executes securely Integrate secure coding principles into SDLC components by providing a general description of how the secure coding principles are addressed in Architecture and Design documents. If a secure coding principle is not applicable to the project, this should be explicitly documented along with a brief explanation. GitLab Security Secure Coding Training. This page contains information on secure training initiatives sponsored by the GitLab Security team. Security Development Process. For information on developing security fixes in GitLab, please see the Security Release Documentation. (Required) Secure Coding Guidelines
Dec 20, 2017 - The team has also begun efforts to create secure coding standards for additional languages: Ada, C#, Fortran, Python, JavaScript, and SPARK. Our secure coding standards consist of actionable guidelines (rules and recommendations), which provide information about the types of security flaws ... Sep 01, 2019 - Many thanks to Google’s Mike Samuel for contributing this article on JavaScript security. 6/10/2019 · JavaScript Web Application Secure Coding Practices is a guide written for anyone who is using the JavaScript Programming Language for web development. This book is a collaborative effort by the Checkmarx Security Research Team and it follows the OWASP Secure Coding Practices - Quick Reference Guide v2 (stable) release.
Coding Guidelines - ReactJS Table of Contents Basic Rules Naming Ordering Alignment Quotes Tags Stateless function components PropTypes declarations Prefixing none React methods Prefixing component wide variables Using handler methods Using "container" components for loading data from Stores Closing Components without children List ... It is a good coding practice to put all declarations at the top of each script or function. This will: Give cleaner code. Provide a single place to look for local variables. Make it easier to avoid unwanted (implied) global variables. Reduce the possibility of unwanted re-declarations. // Declare at the beginning. Oct 09, 2012 - JavaScript vulnerabilities are on the rise in India with the entry of HTML5 and faster JavaScript engines. Here are some key problem areas along with antidotes.
This coding standard, as part of the Software Security and Quality Assurance (SSQA) Framework, developed by the Ministry of Transport and Communications (MOTC), provides specific direction for JavaScript developers to help mitigate common threats to JavaScript applications and enhance the quality of code developed using the JavaScript language. Read our guide on javascript security and the common vulnerabilities such as cross-site scripting (XSS) and cross-site request forgery (CSRF). Coding guidelines help in detecting errors in the early phases, so it helps to reduce the extra cost incurred by the software project. If coding guidelines are maintained properly, then the software code increases readability and understandability thus it reduces the complexity of the code. It reduces the hidden cost for developing the software.
OWASP Secure Coding Practices-Quick Reference Guide on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security of software. Store Donate Join. This website uses cookies to analyze our traffic and only share that information with our analytics partners. ... DISA STIG security guidelines are important for software developed for the DoD. And using Klocwork can help you ensure your code is secure. That's because Klocwork is the most trusted static analyzer for C, C++, C#, Java, and JavaScript coding languages. See for yourself how Klocwork can help you ensure secure software and systems. First of all, take a look at the XSS Cheat Sheet and the HTML5 Security Cheat Sheet about the many ways a website can be exploited using cross-site scripting (XSS) techniques. Persistent XSS can occur when a website prints or injects text or HTML code into the page.
Cisco DevNet is Cisco's developer program to help developers and IT professionals who want to write applications and develop integrations with Cisco products, platforms, and APIs. Cisco DevNet includes Cisco's products in software-defined networking, security, cloud, data center, internet of ... Secure coding standards are rules and guidelines used to prevent security vulnerabilities. Used effectively, these security standards prevent, detect, and eliminate errors that could compromise software security. Here, we cover the key secure coding standards. CWE and CWE Top 25 Developing and managing software is no easy feat. Consider that an operating system can contain over 50 million lines of code. To help developers rise to the software security challenge, enter OWASP, the Open Web Application Security Project. Comprised of thousands of super-smart participants collaborating globally, OWASP provides free resources "dedicated to enabling organizations to ...
Javascript has several encoding formats: C-style backslash \ encoding of special terminal characters and string literals. 2 byte hex encoding of the corresponding ASCII code point: \xNN. 3 digit octal encoding of the corresponding code point \NNN. 4 byte hex encoding of a 4 byte UTF-16 plane: \uNNNN. 16/8/2021 · Communications between the server and the client should be secured using TLS. Be mindful of what code you’re reusing. Threat actors abused vulnerable packages or infected others with malicious code in several attacks. Most of the code your application is running doesn’t belong to you, so be aware of the possible security implications. The focus is on secure coding requirements, rather then on vulnerabilities and exploits. It includes an introduction to Software Security Principles and a glossary of key terms. It is designed to serve as a secure coding kick-start tool and easy reference, to help development teams quickly understand secure coding practices. Sections of the Guide:
Aug 16, 2017 - Most important Security principles in JavaScript. Actionable items to make your JavaScript based Web application more secure.
 Secure Coding Guidelines For Content Security Policy
Secure Coding Guidelines For Content Security Policy
 Most Common Security Vulnerabilities Using Javascript
Most Common Security Vulnerabilities Using Javascript
 Code Review Checklist To Perform Effective Code Reviews
Code Review Checklist To Perform Effective Code Reviews
 Software Security And Development Guide Perforce
Software Security And Development Guide Perforce
 Angularjs Security Fundamentals Snyk
Angularjs Security Fundamentals Snyk
 How To Give Developers Secure Coding Training Synopsys
How To Give Developers Secure Coding Training Synopsys
 Creating A Secure Rest Api In Node Js Toptal
Creating A Secure Rest Api In Node Js Toptal
 Javascripts Security And Best Practices That You Need To Know
Javascripts Security And Best Practices That You Need To Know
 Security Assurance In The Sdlc For The Internet Of Things
Security Assurance In The Sdlc For The Internet Of Things
Secure Coding Practices Quick Reference Guide
 Pros And Cons Of Node Js Web App Development Altexsoft
Pros And Cons Of Node Js Web App Development Altexsoft
 Node Js Best Practices And Security
Node Js Best Practices And Security
 The Javascript Guide Web Application Secure Coding Practices
The Javascript Guide Web Application Secure Coding Practices
 Pros And Cons Of Node Js Web App Development Altexsoft
Pros And Cons Of Node Js Web App Development Altexsoft
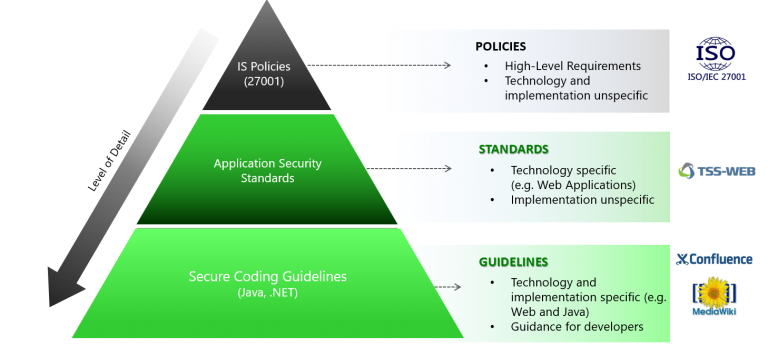 Security Standards Amp Guidelines Secodis Gmbh
Security Standards Amp Guidelines Secodis Gmbh
 Sei Secure Coding Secure Your Software With Sei Cert C
Sei Secure Coding Secure Your Software With Sei Cert C
 8 Secure Coding Best Practices Learned From Owasp
8 Secure Coding Best Practices Learned From Owasp
Javascript Secure Coding Standard
 Secure Coding Tutorials Red Hat Developer
Secure Coding Tutorials Red Hat Developer
 Top 11 Node Js Security Best Practices Sqreen Blog
Top 11 Node Js Security Best Practices Sqreen Blog
Application Security Verification Standard 4 0
 Perfomatix Nodejs Coding Standards
Perfomatix Nodejs Coding Standards
 How To Maintain Mobile App Security While Coding In 2021
How To Maintain Mobile App Security While Coding In 2021
 How To Write Secure Javascript Applications
How To Write Secure Javascript Applications
 Express Js Security Tips How You Can Save And Secure Your App
Express Js Security Tips How You Can Save And Secure Your App
 Javascript Static Code Analysis Amp Security Review Tool
Javascript Static Code Analysis Amp Security Review Tool
0 Response to "27 Javascript Secure Coding Guidelines"
Post a Comment