26 Javascript Public Key Encryption
I may work to do something fancy with generating random numbers with higher entropy, or adding a passphrase to protect the private key. First you need to generate a key pair. (Actually, it's four numbers: p, q, d, and e: p * q and e make the "public key" and p, q, and d make the "private key.") This is the slowest part. Pick how large a key you want. Jul 22, 2021 - For this reason CryptoJS might does not run in some JavaScript environments without native crypto module. Such as IE 10 or before. If it's absolute required to run CryptoJS in such an environment, stay with 3.1.x version. Encrypting and decrypting stays compatible.
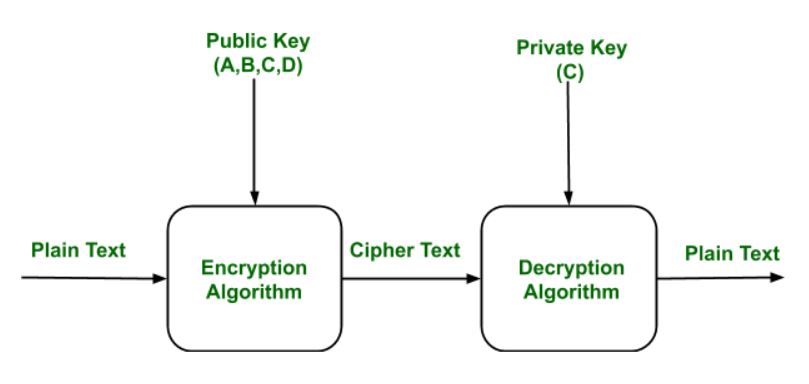 Public Key Encryption Geeksforgeeks
Public Key Encryption Geeksforgeeks
JavaScript port of TweetNaCl crypto library, providing secret and public-key authenticated encryption, hashing, and signatures

Javascript public key encryption. Dec 30, 2020 - Public-key cryptography — or asymmetric cryptography — is a cryptographic system in which keys come in pairs. The transformation performed by one of the keys can only be undone with the other key. One key (the private key) is kept secret while the other is made public. Apr 25, 2020 - First, the data you are trying to encrypt should be much shorter than the bit strength of your keys. For example, the EncryptOEAP documentation says “The message must be no longer than the length of the public modulus minus twice the hash length, minus a further 2.” Within your terminal (Unix based OS) type the following. openssl genrsa -out rsa_1024_priv.pem 1024. This generates a private key, which you can see by doing the following…. cat rsa_1024_priv.pem. You can then copy and paste this in the Private Key section of within index.html. Next, you can then get the public key by executing the following ...
23/4/2016 · Connection is HTTPS. Possible Solution: Generate public-key and private-key on server for each login request. Send public-key to browser. Use JavaScript to encrypt the password with the public-key and send to server. Decrypt using the private-key and validate. Delete keys after login. When browsing the internet looking for a good solution to RSA Javascript encryption, ... Next, you can then get the public key by executing the following command. openssl rsa -pubout -in rsa_1024_priv.pem -out rsa_1024_pub.pem. You can see the public key by typing... Javascript public key. Public Key Cryptography The Public Key Cryptography is the cryptographic mechanism that allows the Internet to be secure.Public-key cryptography, or asymmetric cryptography, is any cryptographic.. Hi I'd like to generate a public/private keypair in node-js, and use the public key to encrypt message and the private key to decrypt the message.
On the PHP side, a temporary private key will be generated (it will expire after a short time). The caller (in Javascript) is responsible for asking for a new public key when it expires. The reason for private key expiration is to prevent logged encrypted data decryption, in case the server which stores the private key is later compromised. RSA and ECC in JavaScript The jsbnlibrary is a fast, portable implementation of large-number math in pure JavaScript, enabling public-key crypto and other applications on desktop and mobile browsers. 5/12/2000 · public encryption key (c1, c2, r) in which r is the product of two relatively prime numbers, and in which c1 and r, as well as c2 and r, are relatively prime numbers, is used in an encryption algorithm x=c1 m1 +c2 m2 (mod r). The decryption algorithm will be equivalent to solving simultaneous linear equations derived from the encryption algorithm.
Oct 27, 2018 - Public-key cryptography, or asymmetric ... to the owner. This accomplishes two functions: authentication, where the public key verifies that a holder of the paired private key sent the message, and encryption, where only the paired private key holder can decrypt the message encrypted ... Oct 20, 2020 - If you write web applications (and the authentication for them) or work in the space of cryptocurrenc... A JSON Web Key (JWK) [6] is a JSON data structure that represents a cryptographic key. Using a JWK rather than one or more parameters allows for a generalized key as input that can be applied to a number of different algorithms that may expect a different number of inputs. All JWE and JWS operations expect a JWK rather than inflexible function ...
1 Answer1. Active Oldest Votes. 4. In common cryptographic protocols there is only a need to generate RSA asymmetric keys now and then, say once a year. The key pair generation does not have to take place in the same environment either; e.g. you could use openssl command line if that is available. Note that RSA key pair generation time depends ... Generating RSA Keys (Mac and Linux) We start by generating a private key. The following command will spit out a .pem file with the name "rsa_private". The 1024 at the end of the command is the key size. Bigger the key the bigger the message you can encrypt, but it will increase encryption time and may affect application performance. openssl ... The encrypt () method of the SubtleCrypto interface encrypts data. It takes as its arguments a key to encrypt with, some algorithm-specific parameters, and the data to encrypt (also known as "plaintext"). It returns a Promise which will be fulfilled with the encrypted data (also known as "ciphertext").
21/11/2008 · Does anyone knows How "JAVAScript Public Key Encryption" works? I am trying to secure my web page. The users are going to be log in to my website. I want to give them a 4 digit pin, that will match the Private key generated by JAVAScript Public Key Encryption algorithm. Something like that. You cannot secure your webpage with clientside code, methinks. I Want to Encrypt in Javascript Using Public Key & Decrypt in Java Using Private Key . I Have Generated Private Key & Public Key Using Open SSL 1) openssl genrsa -out rsa.pem 1024 2) openssl rsa -in rsa.pem -pubout I am Using pidCrypt for Encrypt in JavaScript RSA . At Java Using Instance as RSA( Cipher.getInstance("RSA") ) . But Output is ... A typical application is in authenticating a sender, where the senders private key is used to encrypt a message, and then is decrypted by the receiver with the senders public key (which is known to anyone who wants it). It is also typically used for encrypting disks/files, such as for EFS.
Public Key Cryptography In contrast to symmetric encryption, public key cryptography (asymmetric encryption) uses pairs of keys (one public, one private) instead of a single shared secret - public keys are for encrypting data, and private keys are for decrypting data. A public key is like an open box with an unbreakable lock. Users will generate their public and private key with their password. I would like to know if using Javascript RSA and using RSA signatures to authenticate is safe or can people forge RSA signatures. ... Yet, at the time of writing this, I would be cautious when it comes to Javascript cryptography. To decrypt a PGP message encrypted by an RSA key: Insert the exported private key block. Press Decode/Decrypt to decrypt the private key. If the key is encrypted a Password is required. If the key was successfully decrypted, replace the displayed result by an encryted message. Press Decode/Decrypt to decrypt the message block.
The idea is to implement all the needed OpenPGP functionality in a JavaScript library that can be reused in other projects that provide browser extensions or server applications. It should allow you to sign, encrypt, decrypt, and verify any kind of text - in particular e-mails - as well as managing keys. This project is maintained by ProtonMail. This page contains my Javascript version of RSA Public Key encryption. It is a clone of John Hanna's RSA implementation with a few minor modifications to adapt it for use with GnuPG's multi precision integers. The implementation consists of the following Javascript sources: RSA Encryption in Javascript Now, we have our public keys generated. We will use this public key in javascript for the RSA encryption. To perform RSA encryption at client-side, we will be using JSEncrypt.
RSA Algorithm Javascript Page Welcome to the cryptography home (designed by Cary Sullivan and Rummy Makmur.) We have designed a model of RSA public-key cryptosystem. Following a brief background and description, you can ask another person to encrypt a "message"( actually a letter) and let you decrypt it, using your computer-generated private ... plaintext ::52cee64bb3a38f6403386519a39ac91c:: public key of sender ::52cee64bb3a38f6403386519a39ac91c:: signature · This concatenated block is then encrypted with CBC AES and concatenated with the encrypted AES key to form the complete encrypted message. ... An easy-to-use encryption system utilizing RSA and AES for javascript... 31 Jul 2019 — Server generates RSA public and private keys and store them in the session. Over a server call the client html page recieves the public key. Now ...1 answer · 4 votes: you should add -----BEGIN PUBLIC KEY----- and -----END PUBLIC KEY----- like this -----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQE... -----END PUBLIC KEY-----`
This page contains my Javascript version of RSA Public Key encryption. It is a clone of John Hanna's RSA implementation with a few minor modifications to adapt it for use with GnuPG's multi precision integers. The implementation consists of the following Javascript sources: 17 Sep 2012 — The caller (in Javascript) is responsible for asking for a new public key when it expires. The reason for private key expiration is to prevent ...5 answers · Top answer: I've used something similar for my login page; it encrypts login credentials using the given ... Apr 21, 2021 - In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message. The security of the system depends on the secrecy of the private key, which must not become known to any other.
Dec 31, 2018 - You could encrypt the data using an asymmetric encryption — i.e. a public rsa key to encrypt the data, store the encrypted data temporarily on the device and only decrypt the data once it has been transmitted to the server (as a side note: please use a ssl/tls connection to transmit the data). Hi I'd like to generate a public/private keypair in node-js, and use the public key to encrypt message and the private key to decrypt the message. I need to encode user's secretKey because I use them for individually validation. And then I should decode it. I guess I can use public/private key encryption for this. Public key encryption in Javascript? 199 views. ... public encryption key (c1, c2, r) in which r is the product of two relatively prime numbers, and in which c1 and r, as well as c2 and r, are relatively prime numbers, is used in an encryption algorithm x=c1 m1 +c2 m2 (mod r). The decryption algorithm will be equivalent to
6 Dec 2020 — It's faster when compared to public key (asymmetric) cryptography and therefore used for encryption and decryption of bulk messages.Secret key cryptography · Implementing secret key cryptography in JavaScript A public key, known to all users of your application, is used for encryption. A private key, known only to you - the provider - is used for decryption. So before we get started, we need to generate public/private key pairs and a certificate. Here's an example of data encryption via public key using JSEncrypt. More about JSEncrypt http://travistidwell /jsencrypt. The library is also capable of encryption but keep in mind that if you use it on client side the public key will be visible. (function ( global, factory) { typeof exports === 'object' && typeof module !== 'undefined' ?
With this information, we can translate a private key format to the variables required with the jsbn library from Tom Wu by using the following mappings. modulus => n public exponent => e private exponent => d prime1 => p prime2 => q exponent1 => dmp1 exponent2 => dmq1 coefficient => coeff ... A Javascript library to perform OpenSSL RSA Encryption... Implementing Public Key Cryptography in JavaScript Cryptography refers to the encoding and decoding of messages to maintain confidentiality, integrity, and authentication of information in transit. Public key cryptography is also known as asymmetric cryptography. In this method, there is a public key and a private key. Emscripten-compiled Javascript version of NaCl, the Networking and Cryptography library. ... RSA public/private key crypto for Node. ... Provides a simple wrapper around the fantastic work done by Tom Wu for RSA Encryption for JavaScript.
Public key Encryption is important because it is infeasible to determine the decryption key given only the knowledge of the cryptographic algorithm and encryption key. Either of the two key (Public and Private key) can be used for encryption with other key used for decryption. Due to Public key cryptosystem, public keys can be freely shared ... 18 Sep 2017 · 3 answersDue to ProtonMail's efforts, there is now an open source Symmetric Key Encryption implementation in the browser at: https://openpgpjs /. Upon submitting the SI you will download the server's RSA public key, likely RSA-2048 will suffice here, as you can generate new key-pairs manually on a frequent basis. RSA with JavaScript could be a good starting point, as it shows how you could encrypt a string with the public key and offers decryption options as well within the source code.
Apr 26, 2021 - While, for asymmetric encryption, different key pairs are used for encryption and decryption. A public key that is shared by authorized users is used for encryption whereas a secret key from the recipient is used for decrypting. The secret key is kept secret by their owners. Sep 07, 2013 - Now to authenticate users my server ... will encrypt the string and sign it. The server will check if the signature matches the public key stored for the user. Users will generate their public and private key with their password. I would like to know if using Javascript RSA and using ... Jul 21, 2021 - Return key size in bits. ... Return max data size for encrypt in bytes.
Public private key encryption javascript. Encryption. Using Cryptography Tweetnacl Js To Protect User Data By. Public Key Encryption Article Khan Academy. Asymmetric Encryption In Nodejs Blog By Marco Melilli. Public Key Encryption Article Khan Academy. Difference Between Public Key And Private Key Javatpoint.
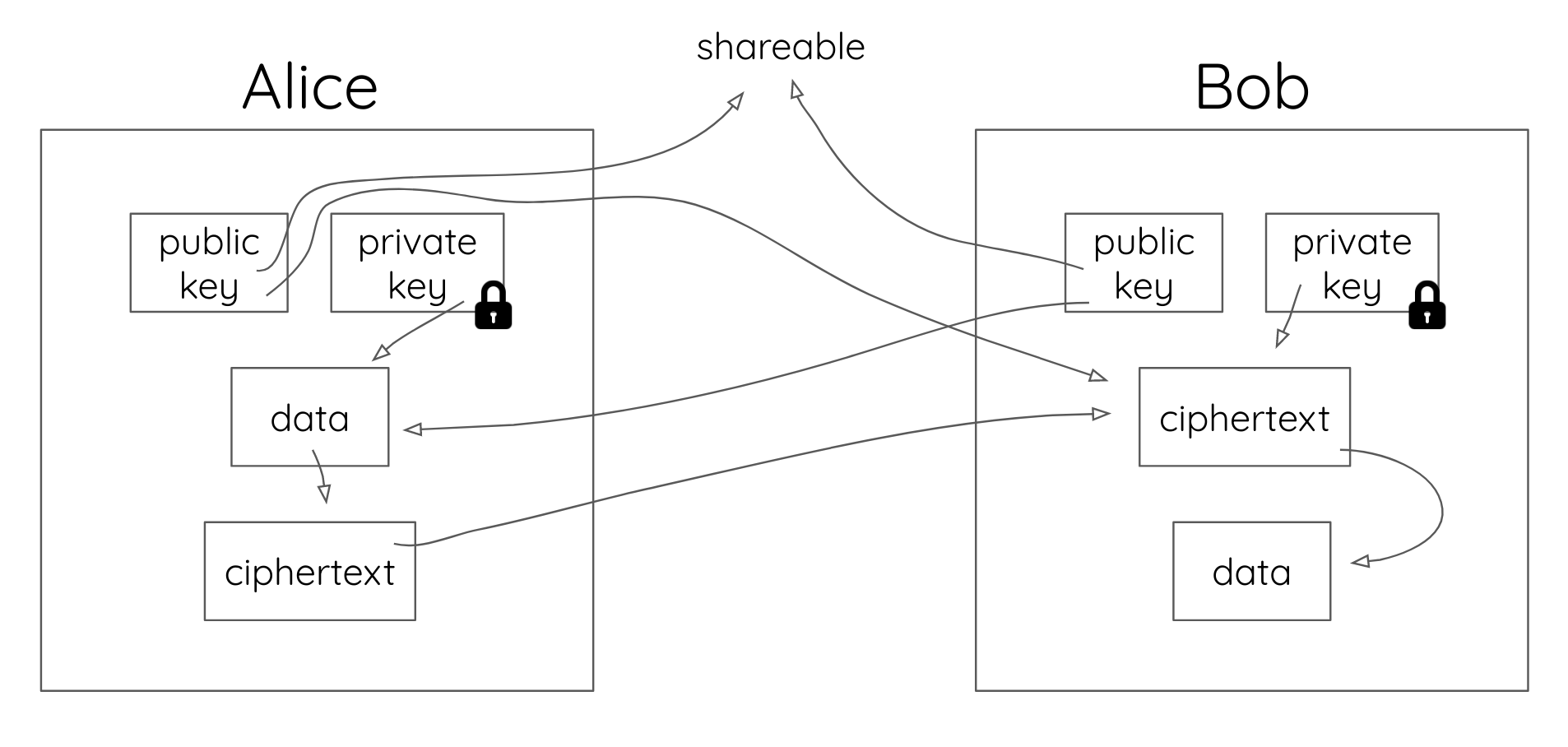 Why Public Key Cryptography Matters Okta Developer
Why Public Key Cryptography Matters Okta Developer
Difference Between Public Key And Private Key In Cryptography
 Si110 Asymmetric Public Key Cryptography
Si110 Asymmetric Public Key Cryptography
 Public Key Cryptography Computer Security A Brief Look
Public Key Cryptography Computer Security A Brief Look
Asymmetric Keys And Encryption Methods Coding At School
 Asymmetric Encryption In Nodejs Blog By Marco Melilli
Asymmetric Encryption In Nodejs Blog By Marco Melilli
 Implementing Rsa Encryption And Signing In Node Js With
Implementing Rsa Encryption And Signing In Node Js With
 What Is Public Key And Private Key Cryptography And How Does
What Is Public Key And Private Key Cryptography And How Does
 A Deep Dive On End To End Encryption How Do Public Key
A Deep Dive On End To End Encryption How Do Public Key
 Why Don T You Use Public Key Encryption To Protect Your Data
Why Don T You Use Public Key Encryption To Protect Your Data
 How Asymmetric Public Key Encryption Works
How Asymmetric Public Key Encryption Works
 Encrypt With Private And Decrypt With Public Information
Encrypt With Private And Decrypt With Public Information
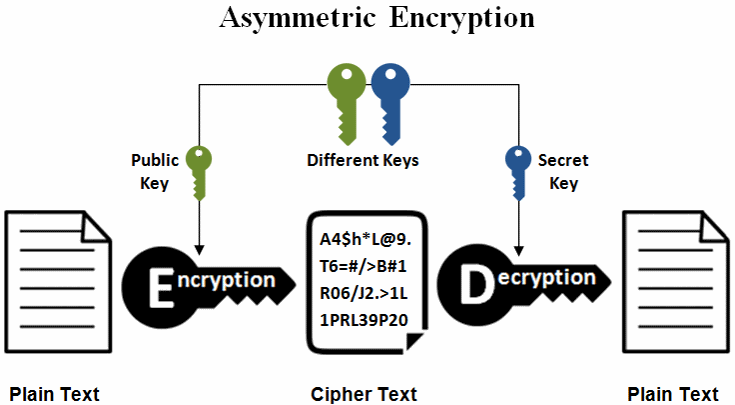 Ecc Encryption Decryption Practical Cryptography For
Ecc Encryption Decryption Practical Cryptography For
 High Speed Public Key Cryptography In Javascript Part 1
High Speed Public Key Cryptography In Javascript Part 1
![]() Implementing Public Key Cryptography In Javascript
Implementing Public Key Cryptography In Javascript
How Javascript Works Cryptography How To Deal With Man In
 Why Public Key Cryptography Matters Okta Developer
Why Public Key Cryptography Matters Okta Developer
 An Introduction To Utilizing Public Key Cryptography In
An Introduction To Utilizing Public Key Cryptography In
Public Key Cryptography Klein Project Blog
 Backpack Algorithms And Public Key Cryptography Made Easy
Backpack Algorithms And Public Key Cryptography Made Easy
 Securing Your Apps With Public Key Cryptography Amp Digital
Securing Your Apps With Public Key Cryptography Amp Digital
 Asymmetric Public Private Key Encryption Rsa In Node Js
Asymmetric Public Private Key Encryption Rsa In Node Js
 How Does Public Key Encryption Work Security Boulevard
How Does Public Key Encryption Work Security Boulevard
 Asymetric Encryption In C And Javascript Network
Asymetric Encryption In C And Javascript Network
0 Response to "26 Javascript Public Key Encryption"
Post a Comment