34 Javascript Injection Alert Test
Dependency injection is not a magic bullet that will solve all of your problems for you. As we discussed, it can sometimes lead to function interfaces becoming very complicated and hard to use. fixture-injection. Note: fixture-injection is still in alpha stage. fixture-injection is a test helper tool for Jest and Jasmine to inject fixtures into test functions and beforeAll() by leveraging dependency injection.. Test functions use fixtures by declaring the fixture names as arguments.
 How To Prevent Sql Injection Attacks And Defense Techniques
How To Prevent Sql Injection Attacks And Defense Techniques
JavaScriptExecutor is an interface that provides a mechanism to execute Javascript through selenium driver. It provides "executescript" & "executeAsyncScript" methods, to run JavaScript in the context of the currently selected frame or window. Generate Alert Pop Window

Javascript injection alert test. Cross-site Scripting (XSS) is a client-side code injection attack. The attacker aims to execute malicious scripts in a web browser of the victim by including malicious code in a legitimate web page or web application. The actual attack occurs when the victim visits the web page or web application that executes the malicious code. The Alert test object corresponds to alerts displayed in web browsers using the JavaScript alert function. You can get the alert text using the Message property and close the alert by simulating a click on its child OK button. XSS is usually the attack to read up on when one talks about javascript injection. Basically you load malicious javascript into a web page that can be later used for phishing. I don't think there are great javascript tools that can uncover XSS vulnerabilities.
5/4/2021 · Code injection is a specific form of broad injection attacks, in which an attacker can send JavaScript or Node.js code that is interpreted by the browser or the Node.js runtime. The security vulnerability manifests when the interpreter is unable to make a distinction between the trusted code the developer intended, and the injected code that the attacker provided as an input. JavaScript - Create an alert on clicking an HTML button. Javascript Web Development Front End Technology Object Oriented Programming. To fire an alert on click of a button, use addEventListener (). Let's say the following is our button on an HTML web page −. <button type="button">Please Press Me</button>. Wherever your application handles user-supplied URLs, enter javascript:alert(0) or data:text/html,<script>alert(0)</script>. Create a test user profile with data similar to the test strings above.
First, fire up the test page in your browser, and enter javascript:alert("Hi!"); in your address bar. That's all, it's that simple. If you want to do something more "productive", try entering javascript:alert(document.getElementById("txt-field").value); - Yes, Javascript works here as usual, just as you do with a code editor. 12/6/2013 · yes quentin! its input type="text". I usually do it element.value="<script>alert('test');</script>". So bsically i have an XSS issue where in when a user enters <script>alert('test');</script> . For this am doing escape and doing an unescape to set in input type="text" but that seems to be executing the alert – Waseem Jun 12 '13 at 9:49 The visitor can type something in the prompt input field and press OK. Then we get that text in the result.Or they can cancel the input by pressing Cancel or hitting the Esc key, then we get null as the result.. The call to prompt returns the text from the input field or null if the input was canceled.. For instance:
TestComplete records and plays back interactions with JavaScript alert boxes using the Alert test object and its child UI objects. It also lets you get the alert text using the Alert.Message property. The following example demonstrates how you can automate an alert box: Web (Cross-platform) Classic. Web (Cross-Platform) Code injection is the exploitation of a computer bug that is caused by processing invalid data. The injection is used by an attacker to introduce (or "inject") code into a vulnerable computer program and change the course of execution.The result of successful code injection can be disastrous, for example, by allowing computer viruses or computer worms to propagate. 31/8/2014 · I want to test a site against javascript injection. I am familier with following syntaxes which are working fine. javascript:alert(document.cookie); javascript:void(document.cookie="authorization=...
During your initial mapping of the application, you should already have identified any obvious areas of attack surface in relation to injection vulnerabilities. Visit the web page of the application that you are testing. Return to Burp and ensure "Intercept is on" in the … HTML injection is a type of attack focused upon the way HTML content is generated and interpreted by browsers at client side. Otherwise, JavaScript is a widely used technology in dynamic web sites, so the use of techniques based on this, like injection, complements the nomenclature of 'code injection'. Step 1 − Login to Webgoat and navigate to cross-site scripting (XSS) Section. Let us execute a Stored Cross-site Scripting (XSS) attack. Below is the snapshot of the scenario. Step 2 − As per the scenario, let us login as Tom with password 'tom' as mentioned in the scenario itself. Click 'view profile' and get into edit mode.
JavaScript Security Analyzers. JavaScript security analyzers are JavaScript security tools that perform code analysis on client-side applications. These analyzers can typically test for JavaScript security vulnerabilities, issues in implementation, configuration errors and other risks that can be exploited by attackers. Selenium Testing | Selenese - Commands. Selenium commands, often called selenese, are the set of commands that run tests. A sequence of these commands is a test script. Here we explain those commands in detail, and we present the many choices you have in testing web application when using Selenium. Exploiting script injection flaws in ReactJS apps. Bernhard Mueller. Aug 1, 2017 · 6 min read. ReactJS is a popular JavaScript library for building user interfaces. It enables client-rendered ...
Server-side JSON injection happens when data from an untrusted source is not sanitized by the server and written directly to a JSON stream. Client-side JSON injection happens when data from an untrusted JSON source is not sanitized and parsed directly using the JavaScript eval function. javascript:alert ('Executed!'); If in the newly opened page includes a text box with the message 'Executed!', then this type of injection attack is possible for the tested form. If in both the ways a text box with the message appears, you can try to break the website with more tricky JS Injection methods. Prevent JavaScript Injection Attacks and Cross-Site Scripting Attacks from happening to you. In this tutorial, Stephen Walther explains how you can easily defeat these types of attacks by HTML encoding your content. ... This text represents a JavaScript script that displays an alert message box.
One obvious way to craft an XSS exploit is to terminate the double quotation marks that enclose the attribute value, close the attribute tag, and then employ some means of introducing JavaScript, such as a script tag. For example: "><script>alert (document.domain)</script>. Check that the payload appears unmodified in the response, before ... Lesson 1: Using JavaScript to Show an Alert Overview. In this lesson, you will use JavaScript to display an alert after the web page has loaded. Learner Outcomes. At the completion of this exercise, you will have learned: how a client-side script fits within the context of an HTML page. some basic Javascript syntax. Activities Now when attacker will execute malicious string in browser for testing order by SQL injection then the IDS of the network should also capture this content and will generate the alert. As per our prediction from given image you can observe the snort has generated alert for order by sql injection when capture malicious string.
Published: 27 January 2016 at 10:39 UTC Updated: 04 September 2020 at 08:04 UTC Abstract. Naive use of the extremely popular JavaScript framework AngularJS is exposing numerous websites to Angular Template Injection. This relatively low profile sibling of server-side template injection can be combined with an Angular sandbox escape to launch cross-site scripting attacks on otherwise secure sites. JavaScript Message Boxes: alert (), confirm (), prompt () JavaScript provides built-in global functions to display messages to users for different purposes, e.g., displaying a simple message or displaying a message and take the user's confirmation or displaying a popup to take the user's input value. JavaScript Alert: Before Page Loads. The above example uses the JavaScript onClick event to trigger the alert box. This example, on the other hand, loads automatically as the page is loading. By placing the code by itself (i.e. not within a link/button), this will automatically trigger the alert box as soon as the page is loading.
Read Cross-Site Scripting Attacks (XSS) and learn with SitePoint. Our web development and design tutorials, courses, and books will teach you HTML, CSS, JavaScript, PHP, Python, and more. Contribute to xsuperbug/payloads development by creating an account on GitHub.
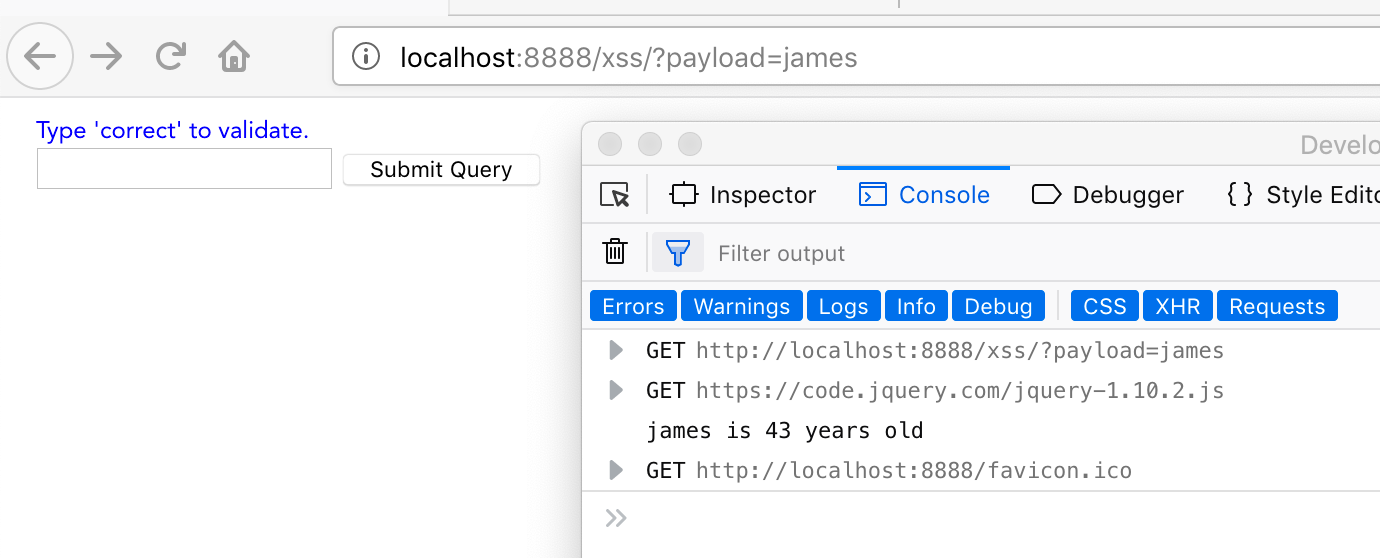 Day 33 Xss Json Js Injection So You Have Found An App
Day 33 Xss Json Js Injection So You Have Found An App
 Handling Common Javascript Problems Learn Web Development Mdn
Handling Common Javascript Problems Learn Web Development Mdn
 Web Attack Lab Remote Javascript Injection
Web Attack Lab Remote Javascript Injection
 Cross Site Scripting In Wordpress Practical Tips For
Cross Site Scripting In Wordpress Practical Tips For
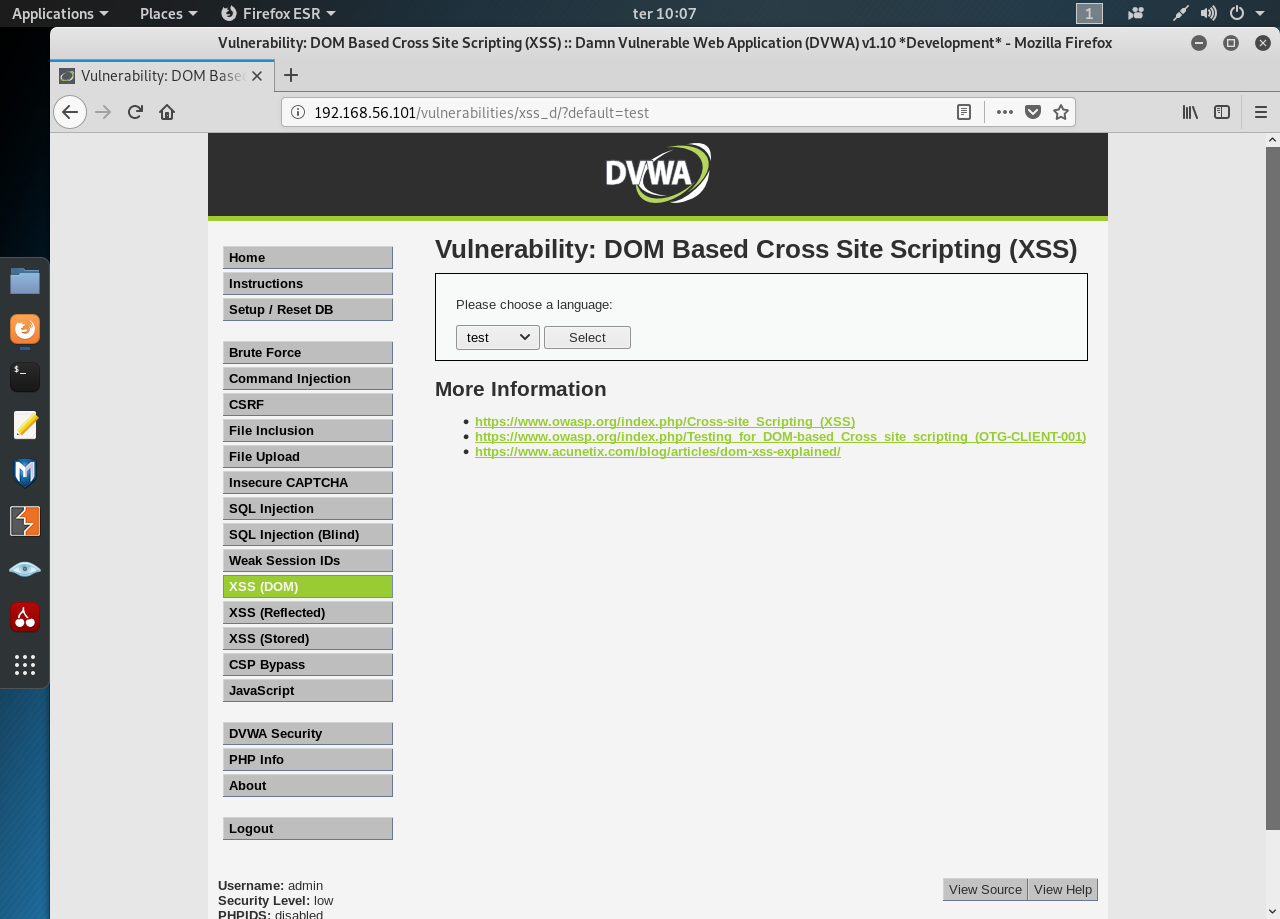 Dvwa 1 9 Xss Dom Xss Stands For Cross Site Scripting By
Dvwa 1 9 Xss Dom Xss Stands For Cross Site Scripting By
 Options In Using Manual Injection For The Browser Rum
Options In Using Manual Injection For The Browser Rum
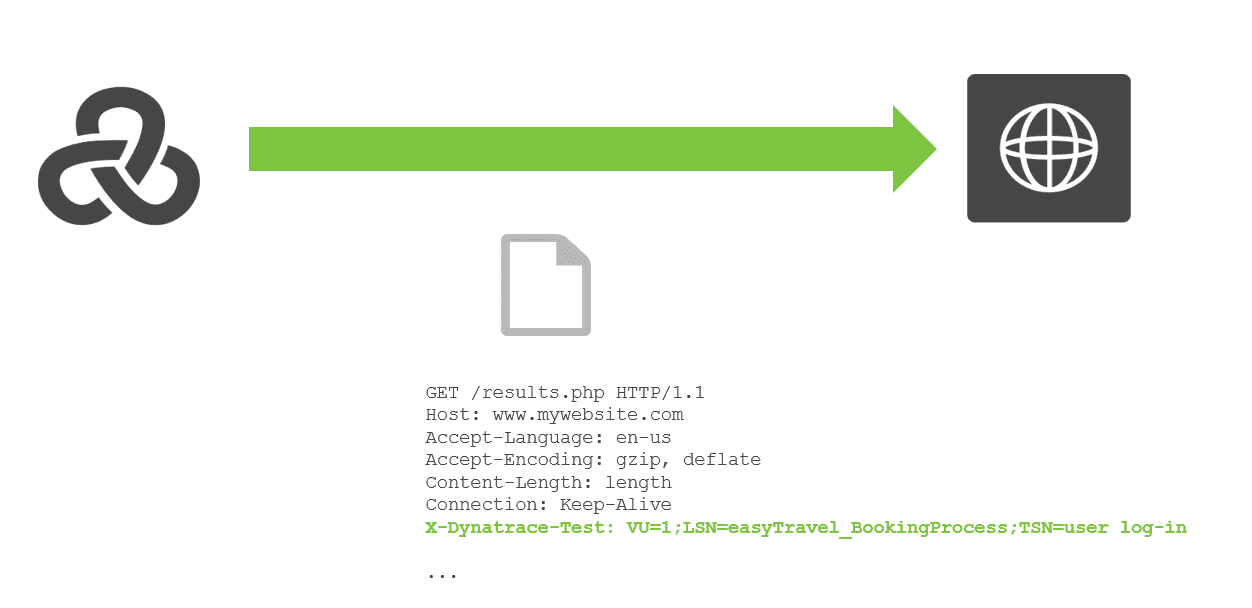 Dynatrace And Loadrunner Integration Dynatrace Documentation
Dynatrace And Loadrunner Integration Dynatrace Documentation
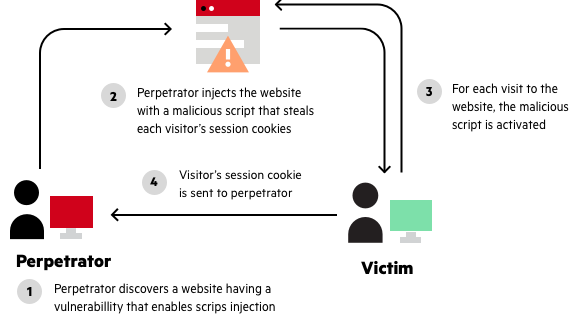 Reflected Xss How To Prevent A Non Persistent Attack Imperva
Reflected Xss How To Prevent A Non Persistent Attack Imperva
 Cross Site Scripting Xss Injection Hacking Lethani
Cross Site Scripting Xss Injection Hacking Lethani
 How To Use Javascript Injections 8 Steps With Pictures
How To Use Javascript Injections 8 Steps With Pictures
 Frame Injection Attacks Netsparker
Frame Injection Attacks Netsparker
 Xss Filter Evasion Cheat Sheet Owasp
Xss Filter Evasion Cheat Sheet Owasp
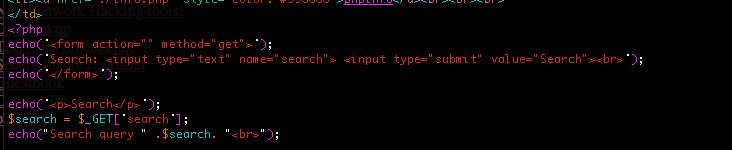 Client Side Injection Attacks Alert Logic
Client Side Injection Attacks Alert Logic
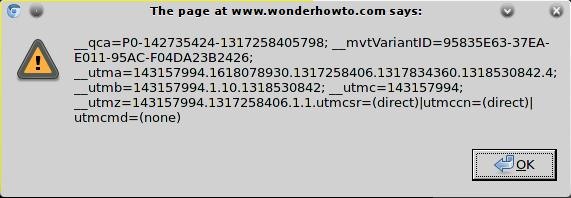 How To Use Javascript Injections To Locally Manipulate The
How To Use Javascript Injections To Locally Manipulate The
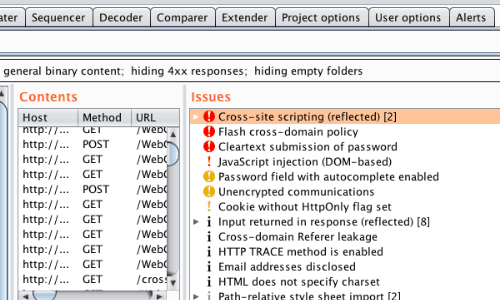 Penetration Testing Process And Tools
Penetration Testing Process And Tools
 5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog
 5 Ways To Prevent Code Injection In Javascript And Node Js
5 Ways To Prevent Code Injection In Javascript And Node Js
 What Is Lt Script Gt Alert 1 Lt Script Gt Quora
What Is Lt Script Gt Alert 1 Lt Script Gt Quora
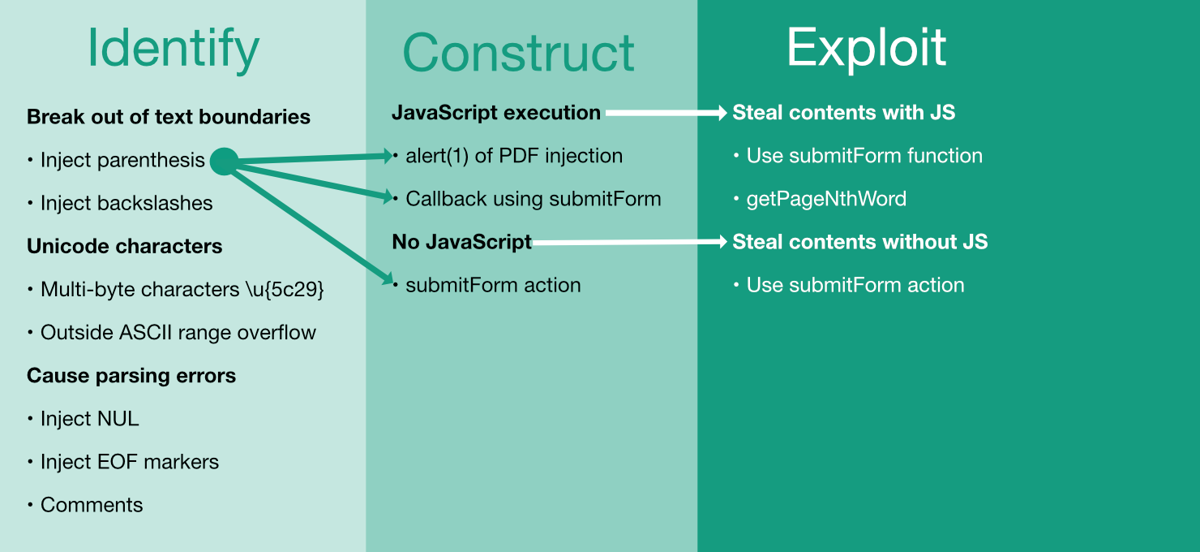 Portable Data Exfiltration Xss For Pdfs Portswigger Research
Portable Data Exfiltration Xss For Pdfs Portswigger Research
Node Js Server Side Javascript Injection Detection
 If Ajax Is Disabled The Javascript Token Injection Don T
If Ajax Is Disabled The Javascript Token Injection Don T
 Frame Injection Attacks Netsparker
Frame Injection Attacks Netsparker
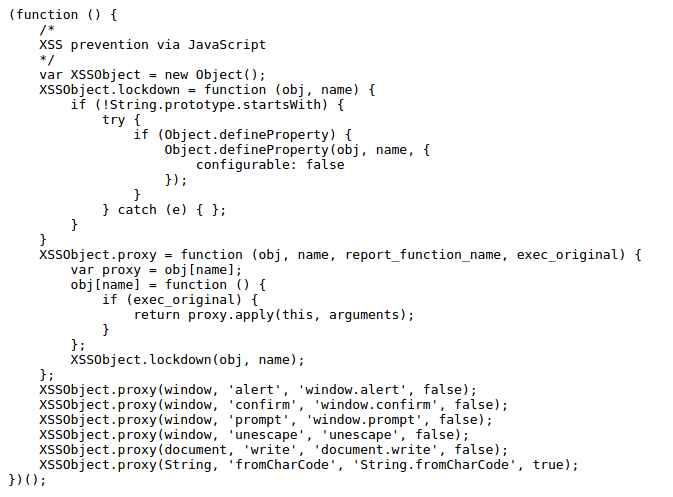 Bypassing Javascript Overrides Brute Xss
Bypassing Javascript Overrides Brute Xss
 How To Use Javascript Injections To Locally Manipulate The
How To Use Javascript Injections To Locally Manipulate The
 5 Ways To Prevent Code Injection In Javascript And Node Js
5 Ways To Prevent Code Injection In Javascript And Node Js
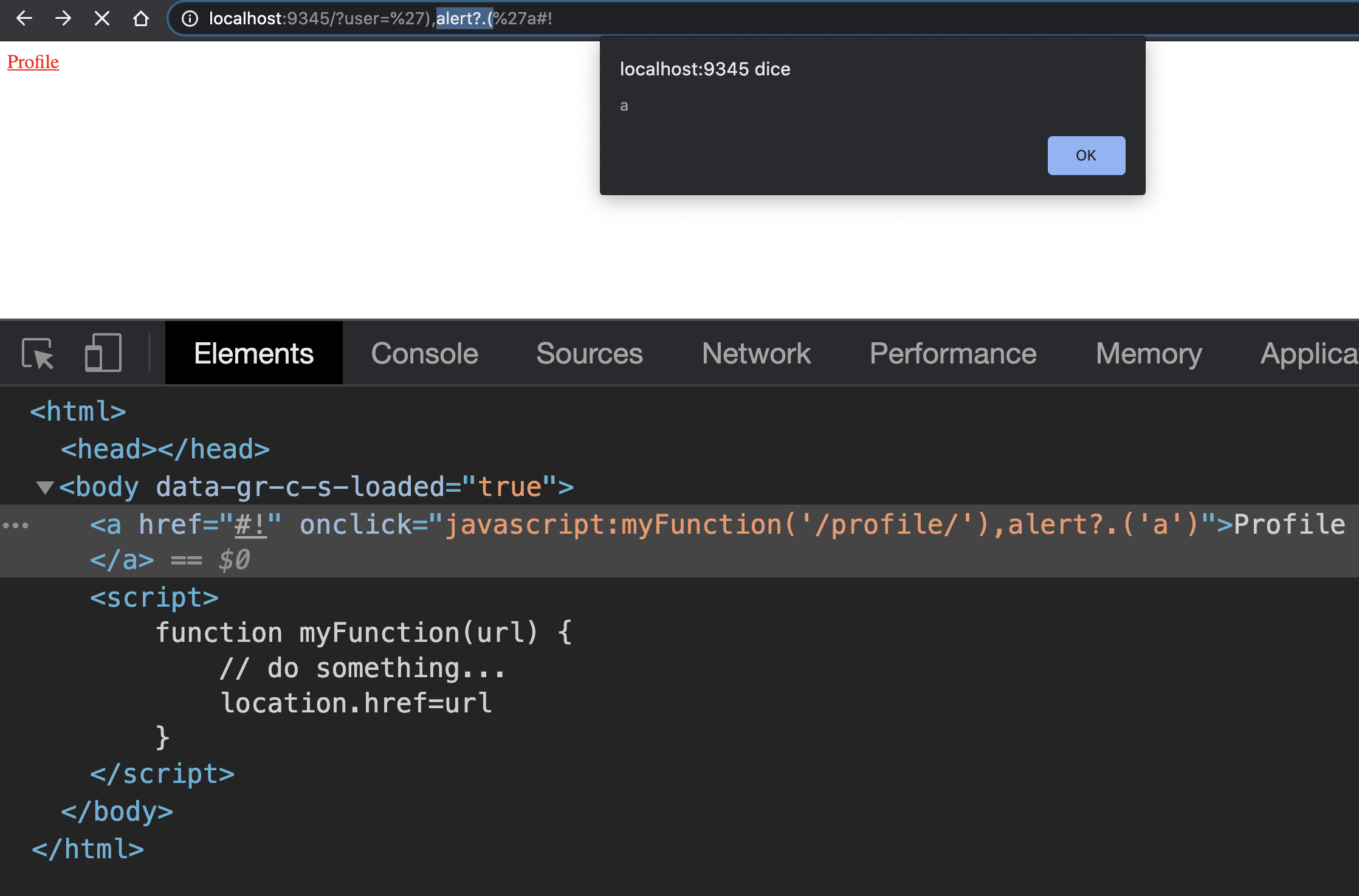 Xss Bypass Filters Amp Sanitization
Xss Bypass Filters Amp Sanitization
 How To Use Javascript Injections 8 Steps With Pictures
How To Use Javascript Injections 8 Steps With Pictures
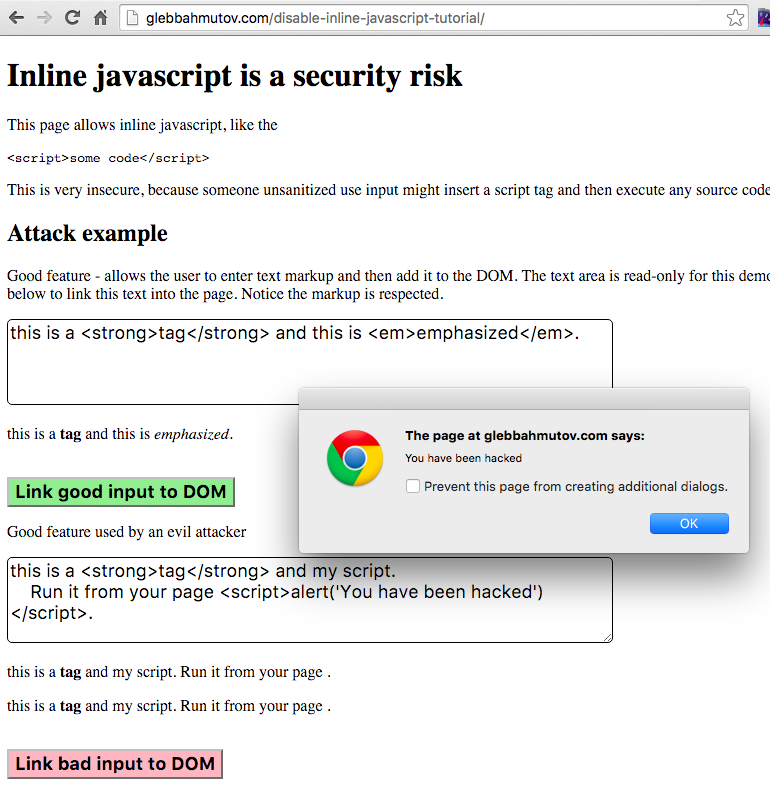 Disable Inline Javascript For Security Better World By
Disable Inline Javascript For Security Better World By
 Javascript Injection Tutorial Test And Prevent Js Injection
Javascript Injection Tutorial Test And Prevent Js Injection
 Frame Injection Attacks Netsparker
Frame Injection Attacks Netsparker
 Javascript Injection Good For Fraud Detection Bad For Security
Javascript Injection Good For Fraud Detection Bad For Security
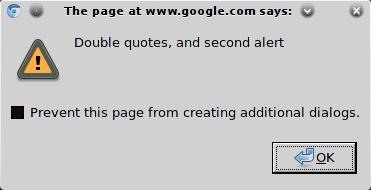 How To Use Javascript Injections To Locally Manipulate The
How To Use Javascript Injections To Locally Manipulate The
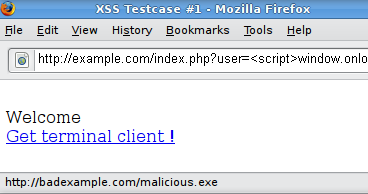
0 Response to "34 Javascript Injection Alert Test"
Post a Comment